Contents:
Last Friday, e-commerce enterprise Mercari has revealed it has suffered an important data breach that took place due to exposure from the Codecov supply-chain attack.
The Codecov breach led to tens of thousands of client information being exposed to cybercriminals.
As we showed in our previous articles, the popular code coverage tool Codecov fell victim to a supply-chain attack. The cyberattack occurred around January 31 2021 when cybercriminals obtained private access to hundreds of networks belonging to Codecov’s users by interfering with one of the company’s software development tools.
The code coverage and testing tools provider made the cyberattack public on April 15, stating that hackers interfered with the Bash Uploader script and modified it. Codecov-actions uploader for GitHub, Codecov CircleCl Orb, and the Codecov Bitrise Step has been compromised.
This allowed threat actors to export information contained in user continuous integration (CI) environments. Hundreds of customers were potentially affected, and now the e-commerce giant revealed it was impacted.
The first pre-IPO startup unicorn Mercari is a Japanese e-commerce company having as the main product the Mercari marketplace app that is currently Japan’s largest community-powered marketplace with over JPY 10 billion in transactions carried out on the platform each month.
According to BleepingComputer, the compromised record includes:
- 17,085 records related to the transfer of sales proceeds to customer accounts that occurred between August 5, 2014, and January 20, 2014.
- 7,966 records on business partners of “Mercari” and “Merpay,” including names, date of birth, affiliation, e-mail address, etc. exposed for a few.
- 2,615records on some employees including those working for a Mercari subsidiary
- 217customer service support cases registered between November 2015 and January 2018.
- 6 records related to an event that occurred in May 2013.
The e-commerce company has illustrated the attack and how this data was exposed to third-party actors in the following infographic:
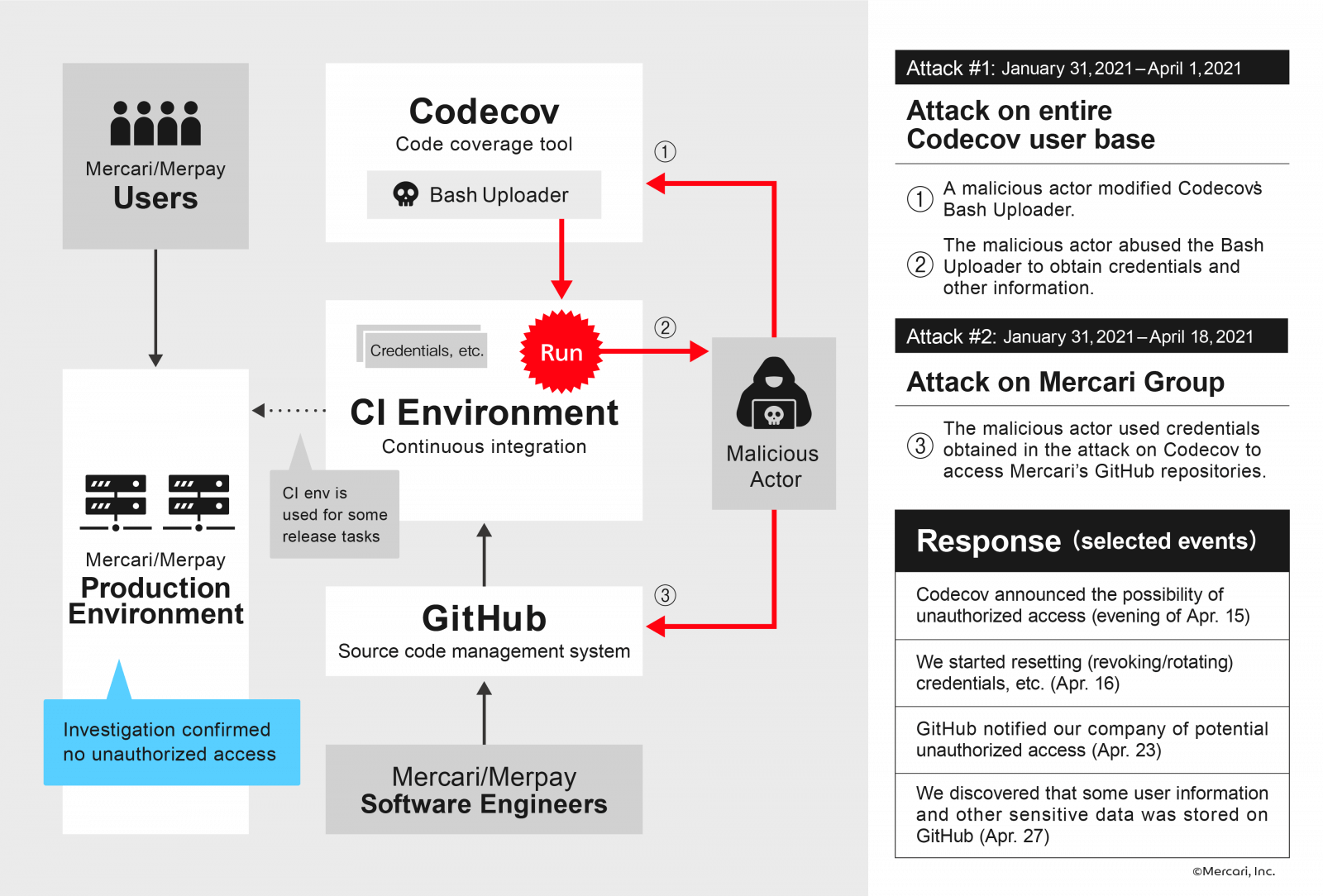
The organization declared it had to wait on making the data breach public because its inquiry activities had been in progress. And until any security vulnerabilities could be entirely identified and fixed, the e-commerce giant risked being attacked again.
Because the investigation is over now, Mercari has been able to disclose the details of the attack.
According to BleepingComputer, several Mercari repositories used the Codecov Bash Uploader that had been compromised.
All the affected customers have been contacted one by one by the Japanese company, and relevant authorities such as the Personal Information Protection Commission, Japan have been informed of the Codecov attack.
At the same time as this announcement, we will promptly provide individual information to those who are subject to the information leaked due to this matter, and we have also set up a dedicated contact point for inquiries regarding this matter
In the future, we will continue to implement further security enhancement measures and investigate this matter while utilizing the knowledge of external security experts, and will promptly report any new information that should be announced.
We sincerely apologize for any inconvenience and concern caused by this matter.
The Mercari attack disclosure comes shortly after monday.com has revealed it had suffered a Codecov supply-chain attack. During the cyberattack, threat actors accessed a read-only copy of its source code.
Another company affected by the Codecov supply-chain attack is the software organization HashiCorp. According to them, a private code-signing key has been exposed focusing on collecting developer credentials.
All the affected clients were informed via email addresses on record and through the Codecov app.
Codecov customers who have utilized the Bash Uploaders between January 31, 2021, and April 1, 2021, are urged to re-roll all of their records, tokens, or keys situated in the environment variables in their CI processes.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










