Contents:
Mars Stealer, a newly released information-stealing malware variant, is gaining traction on the cyber scene. A first large-scale campaign using it has now been observed by security analysts.
Mars Stealer Background
Mars Stealer stands for a reimagining of the Oski malware, which was discontinued in 2020. It shows sophisticated data-stealing functionalities and targets a wide range of applications.
Mars Stealer has expanded modestly until lately when the sudden Raccoon Stealer shutdown took place and determined threat actors to search for other options. It was promoted on hacking forums at inexpensive pricing between $140-$160, as BleepingComputer mentions.
A great number of new users have shown interest in Mars Stealer, and because the service works in a similar way as Raccoon, it’s poised to become the launchpad for a slew of new campaigns.
New Mars Stealer Campaign Identified by Experts
Morphisec threat experts say they’ve observed several of these new campaigns. This includes also a campaign that employs a cracked malware version packed with instructions for use.
The experts published a report on this topic. Morphisec has discovered a new Mars Stealer campaign that leverages Google Ads to promote cloned OpenOffice sites in Canadian search results.
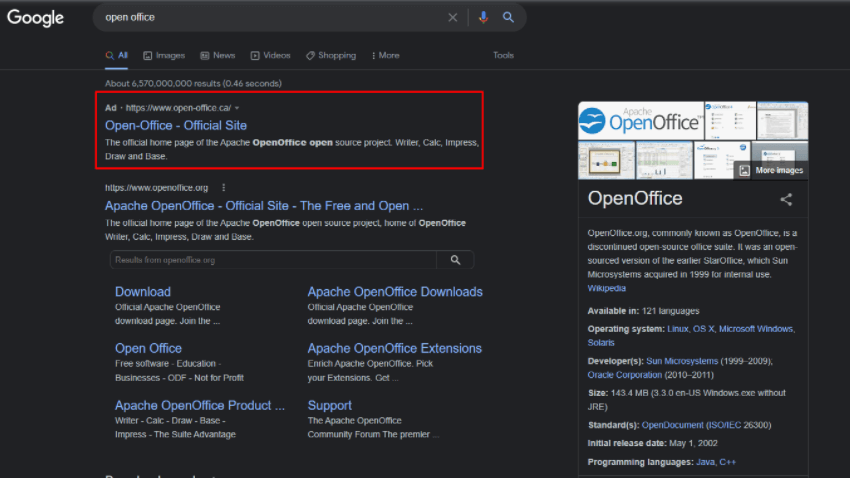
The fake site’s OpenOffice installer is actually a Mars Stealer executable that includes a Babadeda crypter or the Autoit loader, infecting the users without their knowledge.
The operator has managed to expose the victims’ ‘logs’ directory by means of a flaw in the cracked version’s configuration instructions, providing any visitor full access.
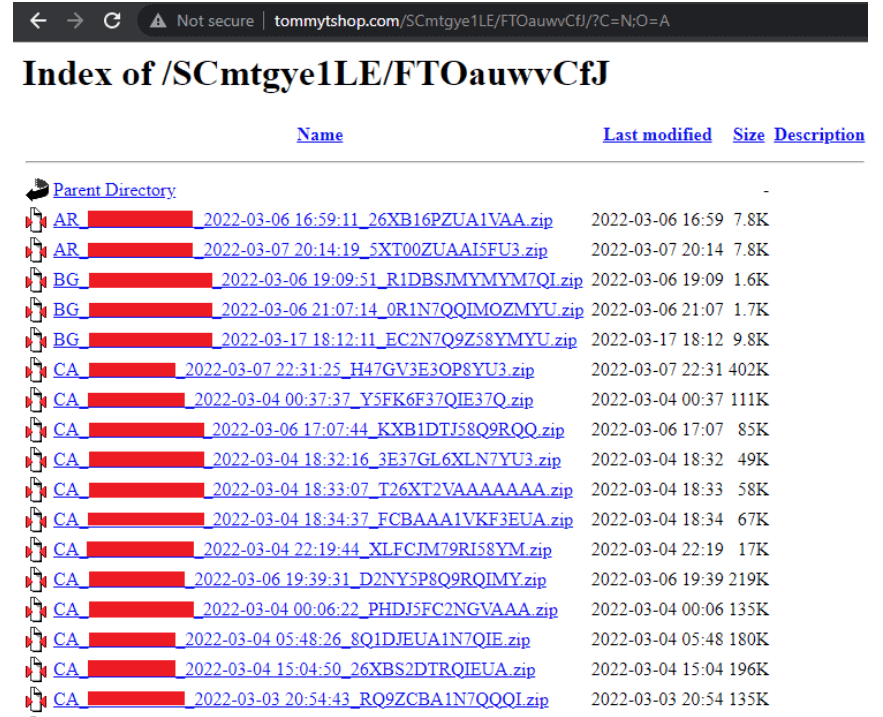
A log represents a compressed file encompassing data stolen by a Trojan and uploaded to the hackers’ command and control servers.
What’s also interesting to mention, according to the researchers, is that Mars Stealer seems to have stolen in this campaign:
- browser auto-fill data
- browser extension data
- credit cards
- IP address
- country code
- and timezone data
During debugging, the hackers appear to have infected themselves with a Mars Stealer copy, managing thus to also expose their sensitive data. Due to this fact, the researchers under discussion were able to link the cyberattacks to a Russian speaker and identify the threat actor’s GitLab accounts among other things.
We looked at the actor’s screenshots and discovered they were debugging their Mars Stealer builds using HTTP Analyzer. This revealed their second Mars Stealer C2 – http://5.45.84[.]214 which was improperly configured, similar to the first C2. An additional screenshot led us to the actor’s GitLab account, which was continuously updated with the latest Mars Stealer builds under the name of “Tony Mont,” which has been active since late November 2021. We are assuming they do this for automation purposes.
What’s Open Office?
OpenOffice is a free document and spreadsheet editor. Users may open and save Word, Excel, and PowerPoint documents. Microsoft Office files can be read and written by OpenOffice.org.
Info Stealers Focus on Crypto Assets
Mars Stealer is a growing danger, with over 47 darknet sites and hacking forums, Telegram channels, and “unofficial” distribution routes such as the cracked pack promoting it.
The operators of these info-stealers, according to Morphisec, are particularly focused on cryptocurrency assets.
MetaMask, Coinbase Wallet, Binance Wallet, and Math wallet, all “hot” wallets for managing cryptocurrency assets, were the most stolen browser plugins from the investigated campaign.
Morphisec also discovered credentials linked to a Canadian healthcare infrastructure provider, as well as compromise signals on other high-profile Canadian service firms.
How to Protect Yourself from Info-Stealers
- Click on official websites and avoid Google Ad results
- Scan executables using an antivirus before actually letting them run
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








