Contents:
In order to avoid US sanctions that avert victims from paying ransom demands, Evil Corp threat actor has released a new ransomware dubbed Macaw Locker.
About Evil Corp
Also known as the Dridex gang or INDRIK SPIDER, the Russia-based hacking group Evil Corp has been around since at least 2007 and is notorious for developing and distributing the banking trojan known as Dridex.
As ransomware operations became more profitable, Evil Corp cybercriminal organization released BitPaymer, which was distributed via the Dridex malware to infected business networks.
In December 2019, the U.S. Treasury Department’s Office of Foreign Assets Control (OFAC) took action against Evil Corp sanctioning the members after using Dridex to cause more than $100 million in financial losses.
As a result of these sanctions, ransomware negotiation companies will no longer facilitate ransom payments for Evil Corp-related operations.
In order to avoid these sanctions, Evil Corp gang members started renaming their ransomware campaign to different names such as WastedLocker, Hades, and Phoenix, and PayloadBin.
DoppelPaymer, which has recently changed its name to Grief, is yet another ransomware group suspected of being linked to Evil Corp. However, the link between the two has not been confirmed.
“New Kid On the Block”
This month, Olympus, a firm that specializes in medical technology and Sinclaire TV Stations known as Sinclair Broadcast Group, revealed they have suffered cyberattacks that seriously impacted their operations.
Following the attack on Sinclair TV Stations, the Active Directory services would have been shut down and the network domain resources access would have been blocked. The attack also affected various corporate assets including newsroom systems, broadcasting, and e-mail servers.
Still dealing with technical difficulties at @CBS6Albany …. Our 11pm newscast (which is starting late after football) will be unconventional. We’re working with handwritten notes, and it’s going to be a bit more conversational. Tune in, and thanks for bearing with us! ??? pic.twitter.com/D620UCD72F
— Leanne DeRosa (@CBS6Leanne) October 18, 2021
It was recently found that both attacks were carried out by a novel ransomware dubbed Macaw Locker. Emsisoft CTO Fabian Wosar told BleepingComputer, that based on code analysis, MacawLocker is the latest rebrand of Evil Corp’s ransomware gang.
Macaw Locker allegedly asked for a 450 bitcoin ransom, or $28 million, for one victim and $40 million for the other. We don’t know yet which company has to pay what ransom.
Macaw Locker M.O.
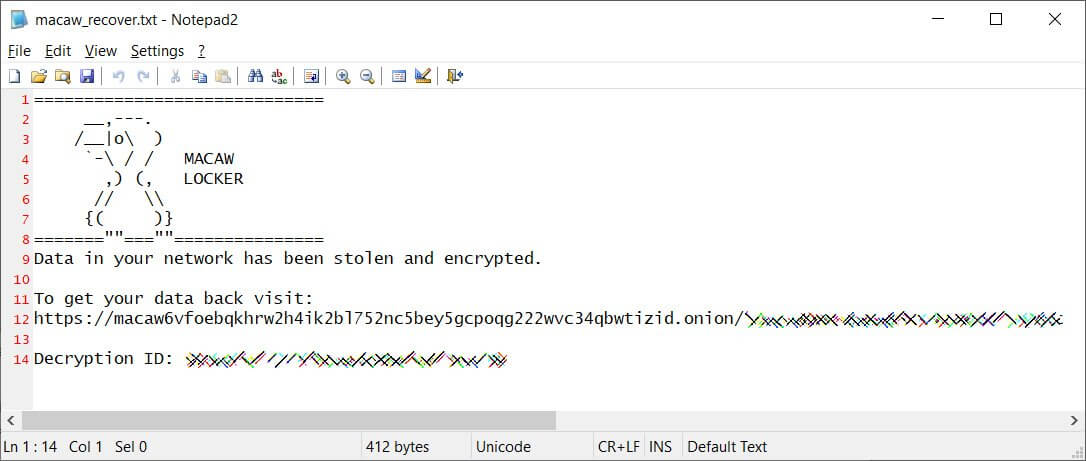
The new ransomware encrypts targets’ files and adds the .macaw extension to the file name of the encrypted files. The ransomware will generate ransom messages in each folder named macaw recover.txt whilst encrypting files.
As explained by BleepingComputer, the ransom notification for each attack includes a unique victim negotiation page on the Macaw Locker’s Tor website and an associated decryption ID, or campaign ID.
The group’s dark web negotiation site includes a short explanation of what happened to the victim, a tool for free decryption of three files, and a chatbox to discuss terms with the threat actors.
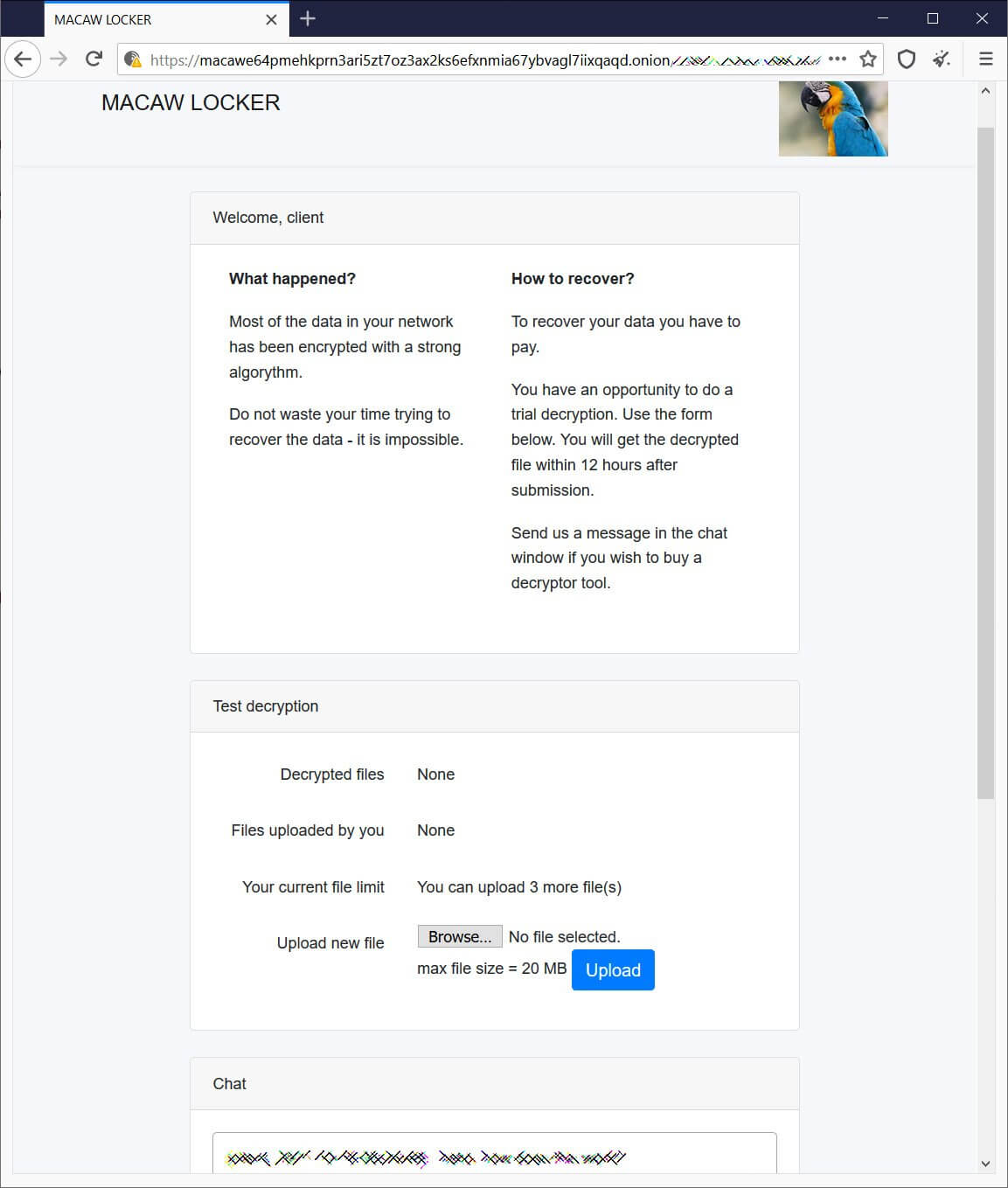
Because now everybody found out about Macaw Locker, Evil Corp’s latest rebrand, the ransomware actor will probably come up with another version and make more victims.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










