Contents:
A more advanced version of the LockBit ransomware operation is deliberately looking to “hire” corporate staff members, former employees, contractors, etc in order to receive help with breaching and encrypting their organization’s systems.
LockBit Ransomware 2.0 Ransomware-as-a-Service
In June 2021, the LockBit ransomware threat actor introduced their new LockBit 2.0 ransomware-as-a-service to the public.
#LockBit ransomware gang announced the start of the LockBit 2.0 affiliate program. The developers claim it’s “the fastest encryption software all over the world”. Alongside ransomware, they offer a stealer named StealBit to download victims’ data. pic.twitter.com/uHXWpSpyb2
— KELA (@Intel_by_KELA) June 21, 2021
Multiple ransomware groups function as a Ransomware-as-a-Service, an illicit ‘parent-affiliate(s)’ business infrastructure, in which operators (i.e., malicious software owner and/or developer) provision tools to affiliates (i.e., customers) to carry out ransomware attacks. To find out more about Ransomware-as-a-Service, check out my colleague’s article on this topic here.
When a victim pays the demanded ransom, the amount of money is split between the Ransomware-as-a-Service provider and the affiliates. As the average ransom demand increased, some affiliates are making up to 80% of each successful ransomware attack.
Of course, there are also situations when instead of attacking an organization by themselves, these affiliates prefer to buy access to corporate systems from third-party individuals who identify security flaws within a network or system, also knowns as pentesters.
According to BleepingComputer, the LockBit 2.0 aims to get rid of intermediaries and as an alternative use insiders who will give them access to corporate networks.
What’s in It for the Insiders?
The answer is simple. A lot of money. As payment for their assistance, the LockBit 2.0 ransomware threat actor promise to reward all the corporate insiders with “millions of dollars”.
Below you can see New LockBit 2.0 wallpaper recruiting insiders.
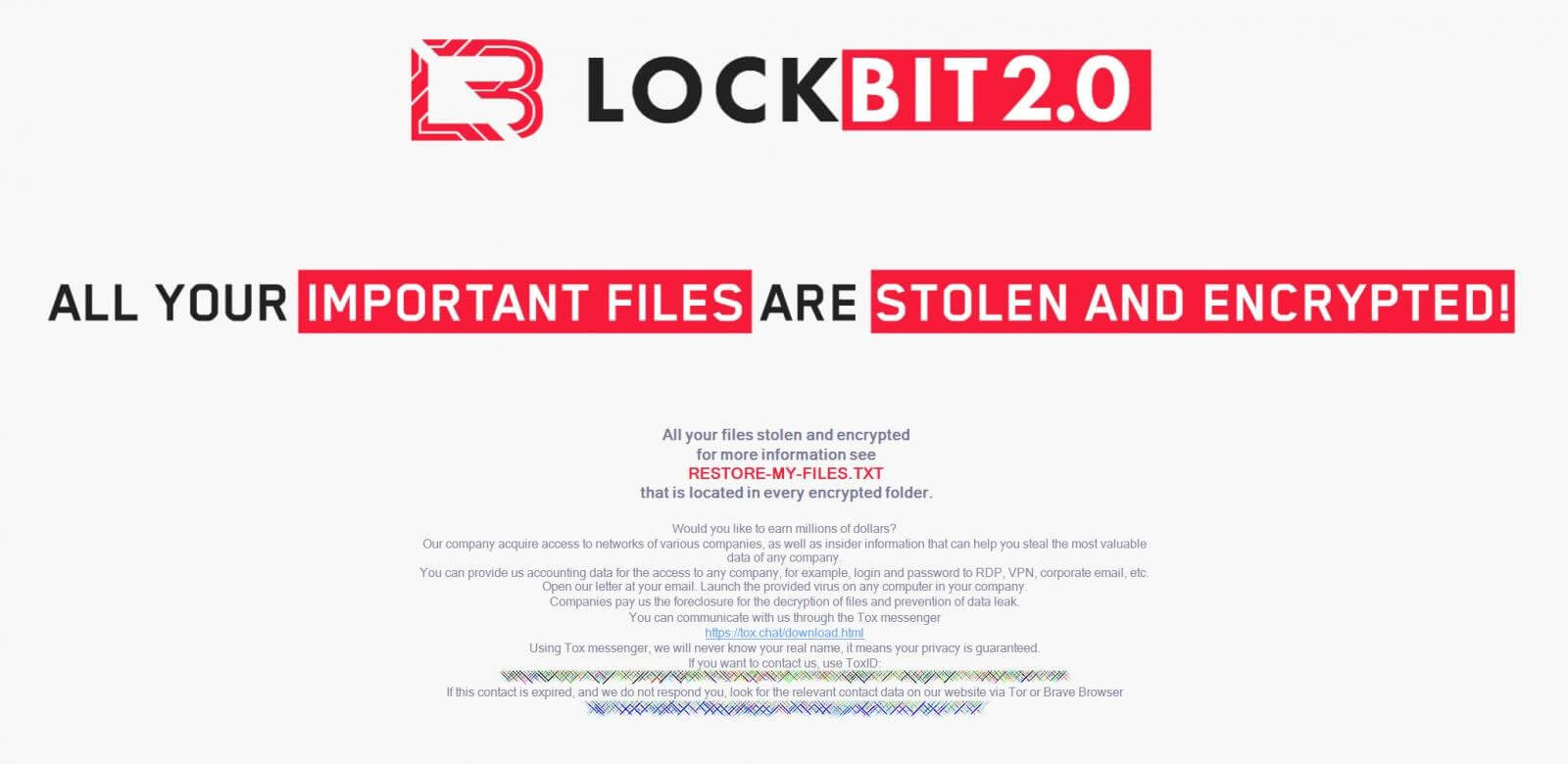
The LockBit message shows that the RaaS service is trying to obtain VPN, RDP, and corporate email private information that will most likely help the threat actor break the corporate system.
According to the message, all the insiders will receive a virus they have to execute on a device in order to facilitate access to the network.
Unfortunately, this is not the first time and definitely not the last when cybercriminals employ the “recruit affiliates” strategy.
As mentioned by BleepingComputer, last year in August, the FBI arrested a Russian-based hacker when tried to recruit a man working for Tesla to place malware on the Tesla’s Nevada Gigafactory network.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








