Contents:
You might have heard that the well-known automaker Kia Motors America (KMA) suffered what seems to have been a ransomware attack that affected internal and customer-facing systems in February 2021.
Kia Motors denied being attacked but acknowledged to have experienced an extended systems outage that affected multiple systems, including the Kia Owner Portal, UVO Mobile Apps, and the Consumer Affairs Web portal.
Aside from Kia Motors, Hyundai also experienced system outages, having its internal systems and dealer sites rendered unreachable.
Both companies denied being affected by ransomware attacks, but journalists from Bleeping Computer got a hold of a ransomware note that indicates the fact that the companies were in fact attacked by a threat actor.
Kia Motors America also placed the following statement on their website, in what seems to be a confirmation regarding the attack:
Kia Motors America, Inc. (“Kia”) is currently experiencing an extended systems outage. Affected systems include the Kia Owners Portal, UVO Mobile Apps, and the Consumer Affairs Web portal. We apologize for any inconvenience to affected customers and are working to resolve the issue as quickly as possible with minimal interruption to our business. We are also aware of online speculation that Kia is subject to a “ransomware” attack. At this time, we can confirm that we have no evidence that Kia or any Kia data is subject to a “ransomware” attack.
What Happened?
In February Kia Motors USA experienced a nationwide outage affecting its IT servers, self-payment phone services, dealer platforms, and phone support.
The Kia Owners Portal went offline and displayed an error message stating that Kia was “experiencing an IT service outage that has impacted some internal networks.”
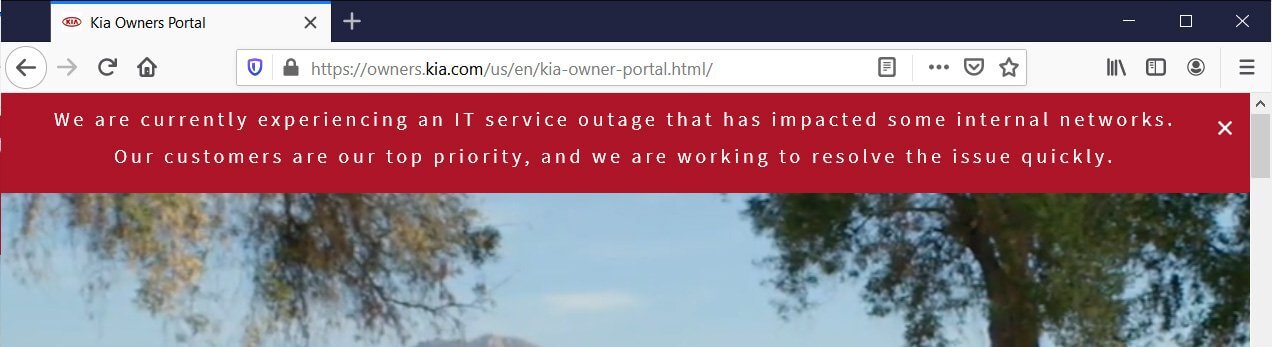
The company’s phone self-help services were also impacted as part of the attack, having the support numbers stating that they have server issues that may affect their ability to help customers.
The outage also affected the company’s mobile apps, such as ‘Kia Access with UVO Link’, ‘UVO eServices’, and ‘Kia Connect’.
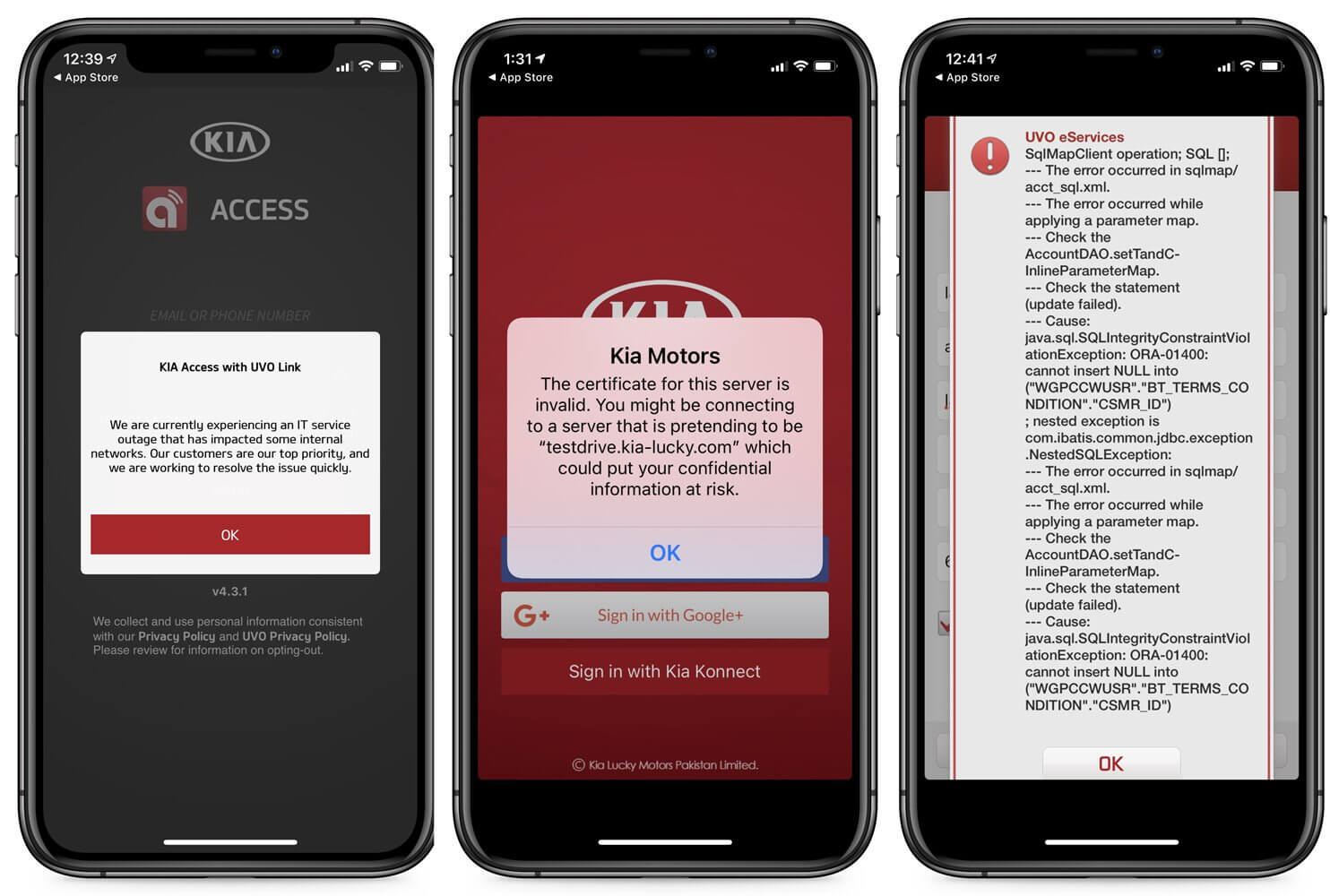
When attempting to use the apps, users were greeted with a few messages, including SQL errors, bad certificates, or maintenance messages stating there is an IT outage, as shown above.
At the same time, the situation made buyers unable to get their cars from dealerships because of a system outage that was caused most likely by the ransomware attack.
The company apologized for the inconveniences created and promised to restore the affected systems as quickly as possible.
Hyundai experienced system outages as well, which were very similar to those experienced by Kia motors, with its internal systems and dealer sites becoming unreachable.
Who Was Behind the Attack?
A note received by the journalists was saying that the attackers are from the DoppelPaymer ransomware group. In the note, the ransomware gang was claiming to have attacked KIA’s parent company Hyundai Motor America, and were threatening to publish the exfiltrated data within 2-3 weeks if Kia Motors would refuse to reach a settlement, while also increasing the ransom from 404 Bitcoins to 600 Bitcoins.
As usually happens with this type of attack the ransomware gang took responsibility for the attack and demanded $20 million worth of Bitcoin to decrypt files and not leak the sensitive data online.
DoppelPaymer ransomware gang operates on the double extortion policy by threatening to publish the stolen data online if the victim refuses to pay the ransom.
As a coercion tactic, DoppelPaymer has placed their demands in a ransom note on a website they are using to leak files if ransoms are not paid, with the website showing that the attackers targeted Hyundai Motor America and that they will leak the data if the ransom is not paid.
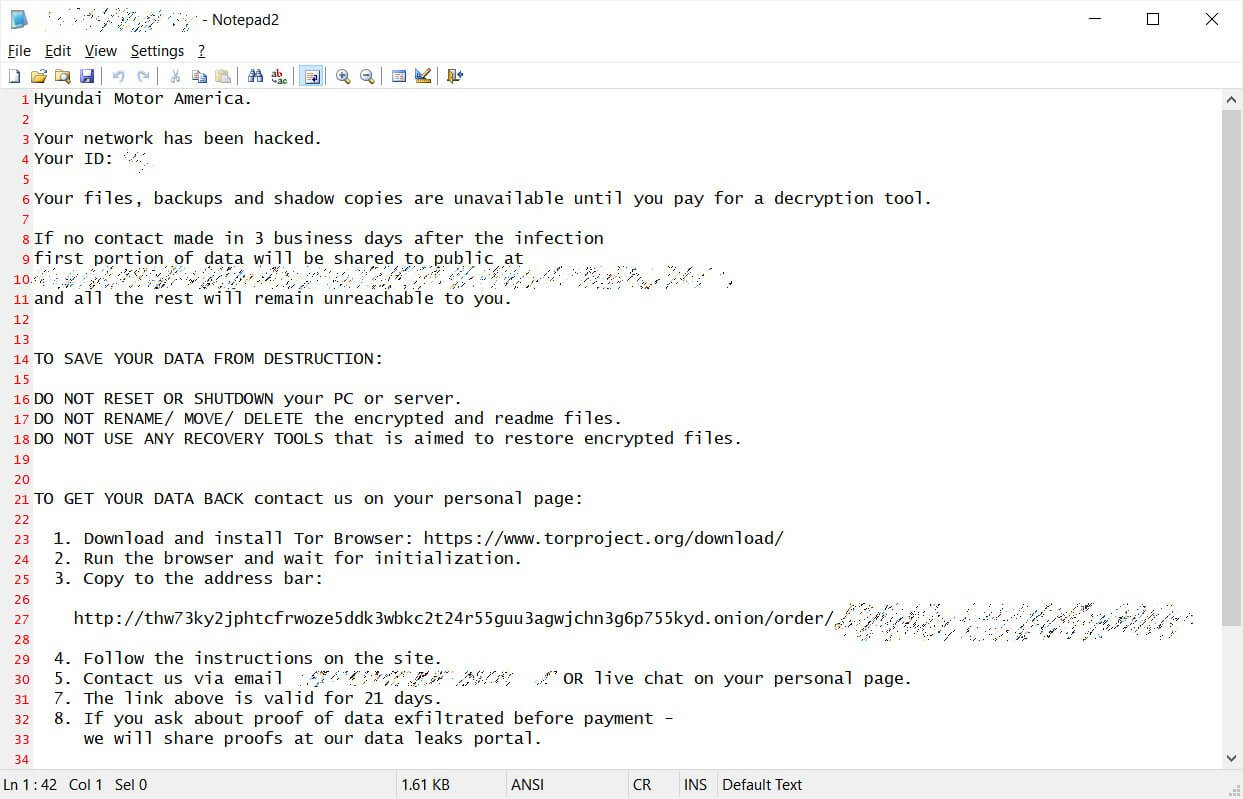
DoppelPaymer ransomware group did not disclose the type of data they have allegedly stolen from Kia and Hyundai Motors, but it’s worth noting that the disruptions appear too coincidental to be just random technical glitches.
Kia and Hyundai may try to cover up the ransomware attack, or the DoppelPaymer ransomware group wanted to capitalize on the outage in order to improve their street credibility.
Wrapping up…
Even if a few months have passed it’s still not 100 percent sure what went on in regards to this cyber incident.
It remains a clear fact that the company’s systems have been offline for days, and as we know this type of outage can cause more financial loss than the ransomware in itself.
It’s unknown if Kia paid the ransom, or if the company was actually attacked, making us wonder about the importance of transparency in such a digitalized era.

Heimdal™ Ransomware Encryption Protection
- Blocks any unauthorized encryption attempts;
- Detects ransomware regardless of signature;
- Universal compatibility with any cybersecurity solution;
- Full audit trail with stunning graphics;










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








