Contents:
Aqua’s security assessment team has recently announced the discovery of a new type of ransomware. The yet-to-be-named malware uses Python-based scripting for malicious file encryption and subsequent obfuscation. Telemetry indicates that the emergent Python-based ransomware strain may have originated in Russia and that it was specifically engineered to target and ransom out JupyterLab Web notebooks.
Nameless Malware ‘Honeypotted’ After the Attack
Following the incident, security analysts from Aqua Security have successfully sequenced the ransomware. Very few facts are known regarding the malware’s origin or its purpose; the initial assessment indicated that the ransomware might have Russian roots and that it might have been used to study the potential (and inherent limitations) of Python-powered malware.
Popularity-wise, Python’s not exactly the go-to choice when it comes to malware development, most going for C++, Go, Objective-C, Swift, and Delphi 2. However, this does not amount to the fact that Python is an ineffective malware creation language; far from it.
Python has been successfully employed for some time now to create backdoors and viruses; a fact corroborated by Valery Linkov who deployed customized “Poisonous Python” libraries to build a virus, a locker, and an encryptor. So, it’s not that uncommon for threat actors to code malware in Python.
As far as the JupyterLab Web incident is concerned, the Python-based ransomware’s discovery was, more or less, a sporting chance. The ransomware managed to gain access to JupyterLab’s web platform by leveraging a series of victim-side misconfigurations. However, the most baffling aspect is that the ransomware timed out before encrypting the assets hosted on the web platform.
According to one working hypothesis, the hacker’s purpose was never to ransom out encrypted files, but to highlight existing vulnerabilities. Of course, there’s also the learning curve – the attacker may simply want to study the interaction between Python-based malware and the available Response & Remediation methodologies. The available data suggests that no assets have been tampered with, despite the fact that the unknown party managed to download and unpack a series of tools via an open terminal.
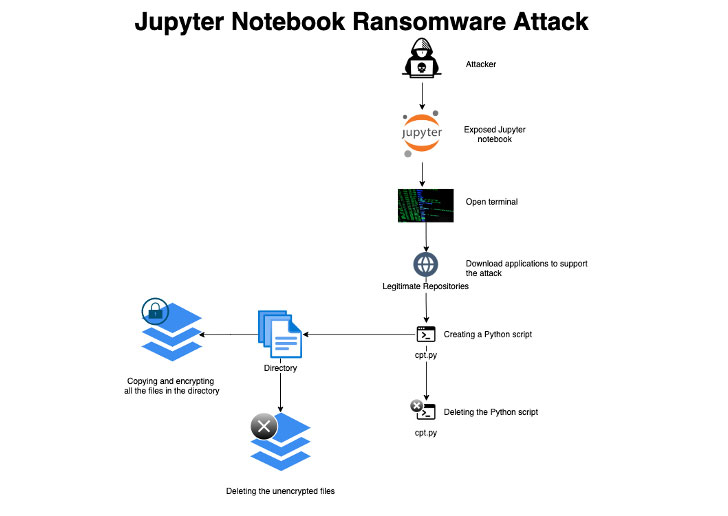
Photo courtesy of The Hacker News
Aqua Security managed to secure a sample from one of the honeypot servers. The subsequent analysis revealed that the ransomware was engineered to specifically target JupyterLab’s web platform. Once inside, it should have encrypted the files, delete the unencrypted ones, and destroy itself afterward. Failed attempt or the beginning of a new breed of malware? Time will tell.
The JupyterLab incident is not singular. Back in 2021, Computer Weekly reported that malware analysts have identified quick-acting, Python-based ransomware that targeted VMs and ESXi servers. No relations have been established between the two, but it goes to prove that threat actors may very abandon ‘traditional’ malware development programming language in favor of Python which was found to be very flexible and easy to master. On top of that, Python-spawned malware has increased propagation rates and is harder to detect (and evict) compared to those written in other programming languages.
What does the JupyterLab Incident Teach Us?
Apart from the age-long axiom that “nothing is secure”, this incident comes once again underlines the importance of threat-hunting and vulnerability management. Frequent pen-testing coupled with on-point vulnerability handling can prevent such occurrences.
Is malware written in Python more dangerous and more destructive compared to its peers? The available data may just point to that conclusion – Python-written evil code has greater obfuscation capabilities in addition to its flexibility. With readily available libraries, assembling malware takes less time, and the impact of the resulted evil code is no less destructive compared to its peers.
So, what can we do to protect our assets? Regular pen-testing, patching, and vulnerability management are only half of the answer. A more, hands-on approach is warranted – a way to stop ransomware at its roots. Heimdal™ Security’s Ransomware Encryption Protection and similar are the only reactive solutions capable of actively protecting machines and networks against ransomware through advanced behavioral analysis and beaconization.
What’s your take on the JupyterLabs incident? Leave a comment below.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security









