Contents:
Moses Staff, a new cybercrime organization, has recently taken credit for multiple attacks targeting Israeli companies, which appear to be politically motivated since no ransom requests are made.
In the last few months, cybercriminals have frequently impacted Israeli companies by infiltrating systems, encrypting files, and then making the stolen information public.
Yesterday, Check Point security specialists issued a comprehensive report on Moses Staff, delving into the gangs’ methods, infection chain, and toolkit.
As explained by BleepingComputer, the newly formed political hacker group seems to be employing publicly available exploits for known security issues that remain unfixed on public-facing infrastructure.
How Does It Work?
After breaching the enterprise servers and gaining initial access, the hackers will employ PsExec, WMIC, and Powershell to move laterally through the network, avoiding the usage of backdoors.
The hacker finally encrypts machines with a custom PyDCrypt virus that uses DiskCryptor, a free and open-source full disk encryption system for Microsoft Windows that allows for the encryption of a PC’s entire hard drive or individual partitions. This tool is available on GitHub.
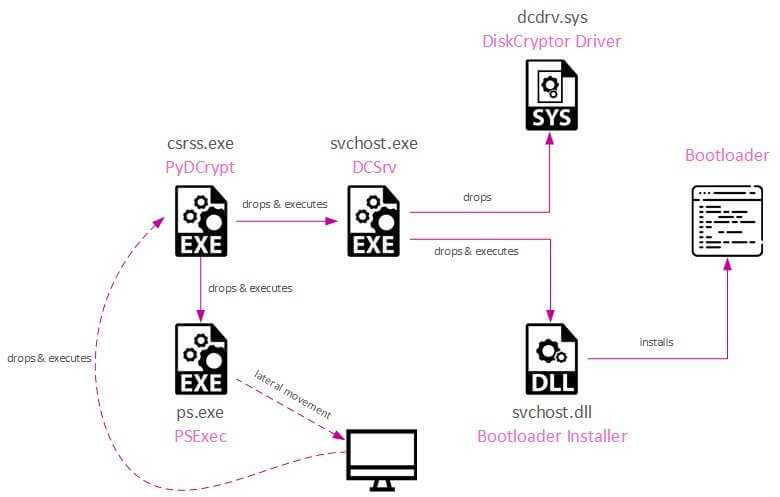
According to CheckPoint researchers, the encrypted files can be recovered under certain conditions because the encryption strategy encrypts devices using symmetric key generation.
PyDCrypt uses an MD5 hash and a crafted salt to create unique keys for each hostname. The hashing function may be obtained by retrieving and reversing the PyDCrypt copy utilized in the operation.
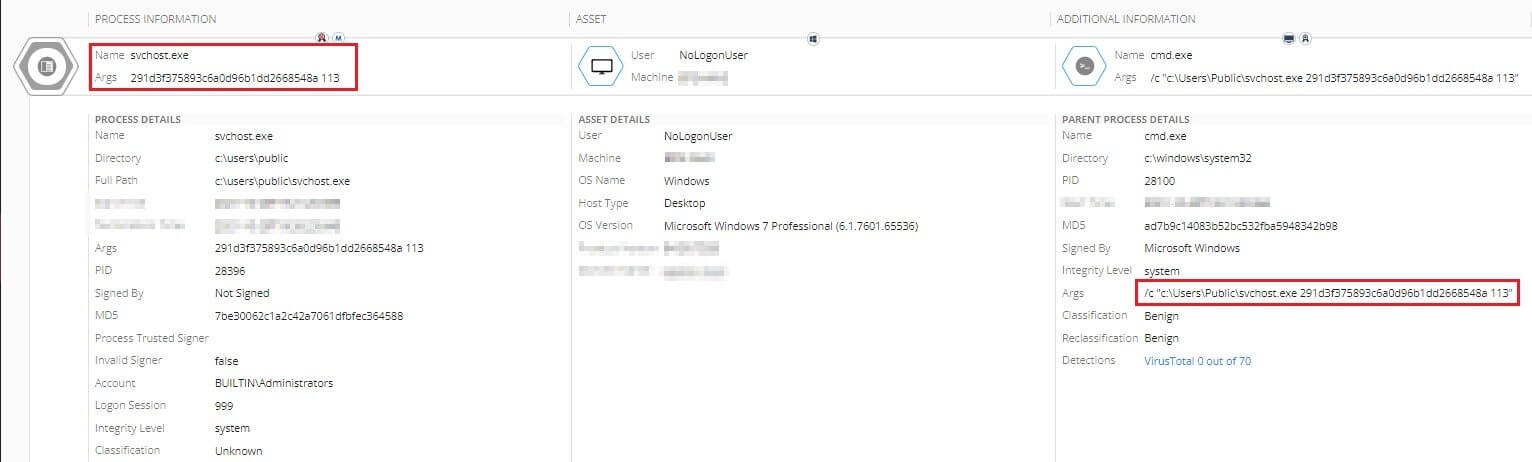
This is possible in many instances where the ransomware’s self-destruct feature has failed or has been disabled in the configuration.
Normally, the Moses Staff hacking group does not pay much attention to this aspect of their campaign because their primary goal is to create disruption in the targeted Israeli organizations, not to make sure that the encrypted files are unrecoverable.
Moses Staff’s Motivation
Despite the fact that the hacker’s name is new, it may be connected to ‘Pay2Key’ or ‘BlackShadow,’ who share the same political motivation and target extent.
In September 2021, the hacker group Moses Staff began targeting Israeli organizations, joining a wave of attacks which was started about a year ago by the Pay2Key and BlackShadow attack groups.
Those actors operated mainly for political reasons in an attempt to create noise in the media and damage the country’s image, demanding money and conducting lengthy and public negotiations with the victims.
The gang has a strong social media presence, as well as a Tor data leak site and a Telegram channel, all of which are utilized to leak stolen information across as many channels as possible to maximize impact.
Up to this point, experts have been unable to link Moses Staff to a specific physical location or determine whether they are a state-sponsored organization.
Nevertheless, a few months before the attacks, one of the malware samples used in the Moses Staff operations was submitted to VirusTotal from Palestine.
Although this is not a strong indication, it might betray the attackers’ origins; sometimes they test the tools in public services like VT to make sure they are stealthy enough.
Check Point urges all Israeli organizations to fix their software in order to prevent future attacks because Moses Staff attacks employ old weaknesses for which updates are accessible.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










