Contents:
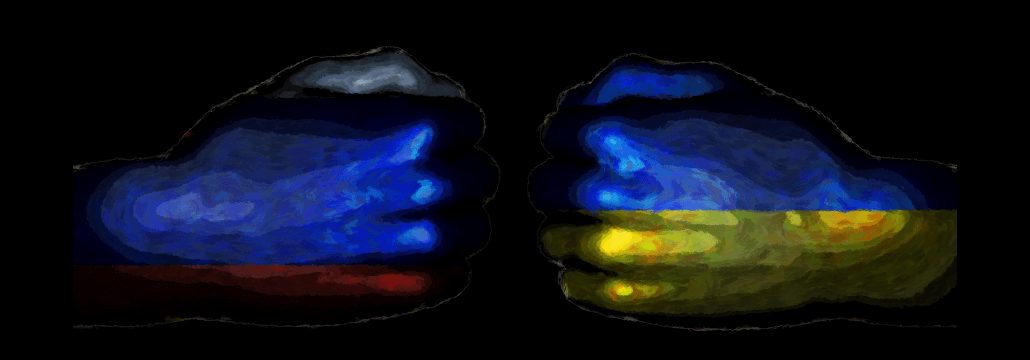
In the past days, we witnessed a long series of cyberattacks that seemingly are targeting Russia as a response to the latest military developments in Ukraine.
Some hackers like the Anonymous group, united against Russia and attacked its infrastructure whilst others decided to give their full support to the Russian Government.
What Is Happening?
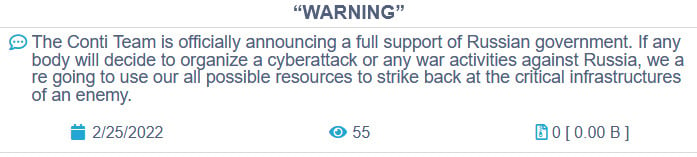
According to a recent threat from the Conti ransomware gang, the group would use all of its resources “to strike back against the important infrastructures of an adversary” if cyber action against Russia continues.
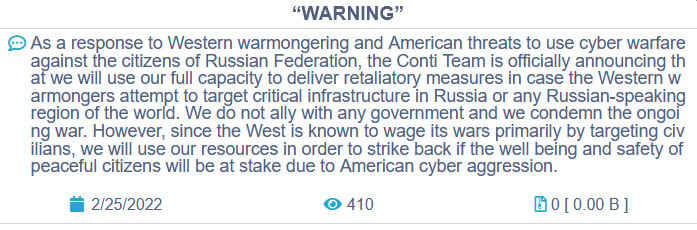
As reported by BleepingComputer, about an hour later, the gang modified their stance, stating that they “do not associate with any government and we condemn the continuing conflict,” but that they would retaliate to Western cyber-attacks against Russian key infrastructure.
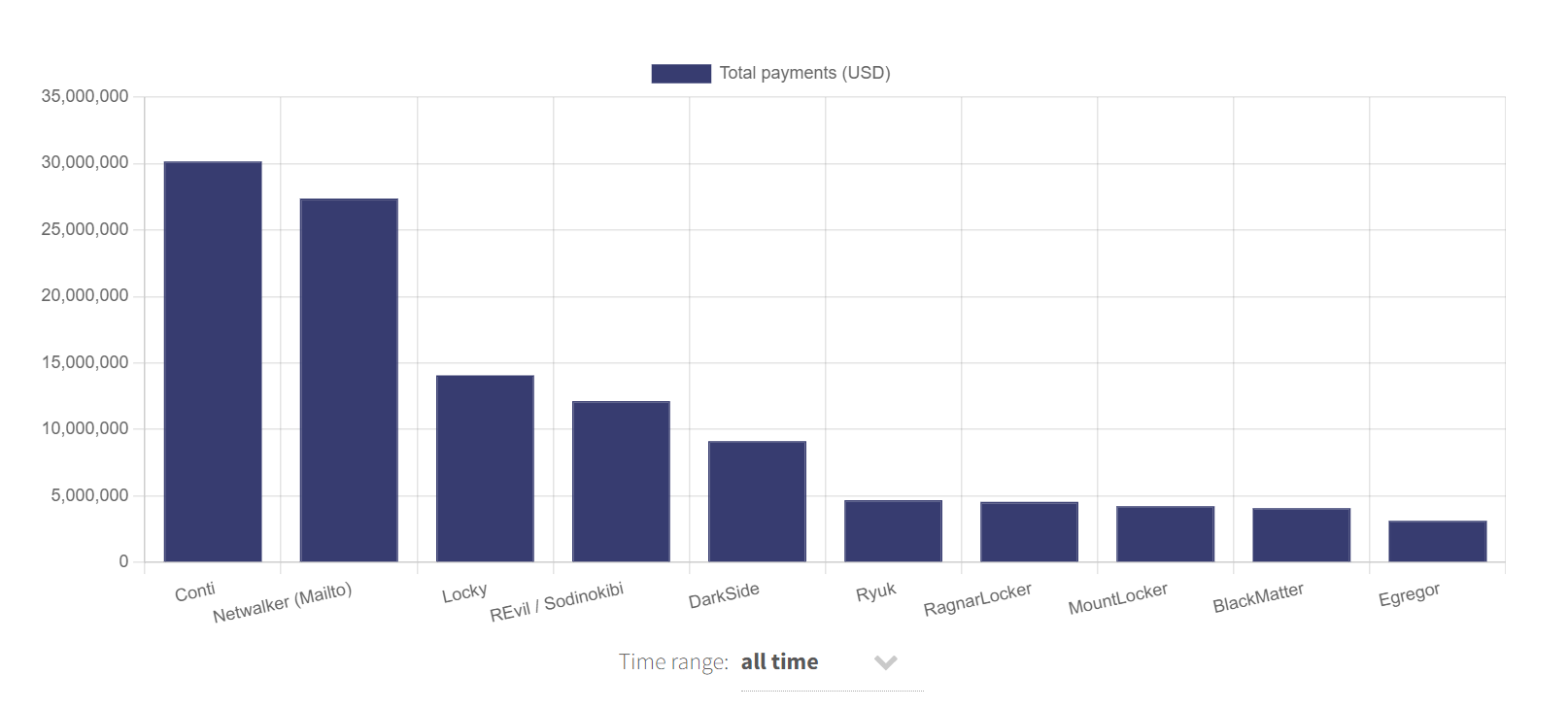
Conti is one of the most prolific ransomware perpetrators in the industrial sector, having been responsible for a total of 63 breaches of industrial control systems (ICS) in the past year, the majority of which occurred in the manufacturing industry.
Aside from that, Conti gained control of BazarBackdoor, a stealthy virus designed by the TrickBot gang for the purpose of infiltrating high-value targets.
Internal Communications of Conti Ransomware Released
Following Russia’s invasion of Ukraine, a member of the Conti ransomware group believed to be of Ukrainian origin, leaked the gang’s internal communications after the group’s leaders posted an aggressive pro-Russian message on their official website on Friday, in the aftermath of the Russian invasion of the country.
Internal records were disclosed via an email that was provided to a number of journalists and security experts, among other people.
Vitali Kremez, a researcher who gained access to the “ejabberd database,” disclosed that it served as the backbone for Conti’s XMPP chat server.
#Conti Leaks:
///
“ts”:”2022-02-14T19:16:39.154766″,
“from”:”m@//.onion”,
“to”:”d@/onion”,
“body”:”а по трику я писал же – он уже не работает, проект прикрыли”
///?#TrickBot does not work. The project is done.
As it is public – reported earlier ?https://t.co/E6cLDPuPrn https://t.co/Kmf7qYDg1l
— Vitali Kremez (@VK_Intel) February 28, 2022
Since January 21, 2021, a total of 393 JSON files holding a total of 60,694 messages have been leaked, and this number is expected to grow. Conti started their business in July 2020, therefore although it covers a significant portion of their internal dialogues, unfortunately it does not contain all of it.
There is a wealth of information included inside these talks concerning the gang’s actions, including information about previously unknown victims, private data breach URLs, bitcoin addresses, and discussions about their operations.
The leak is 339 JSON files of XMPP daily logs from Jan 29, 2021 to Feb 27, 2022 (today)
You can navigate it online here: https://t.co/91hHrzAuMO
Grab Google Chrome and enable Russian auto-translate and enjoy the [boring] chats. pic.twitter.com/RjnLQRqYqQ
— Catalin Cimpanu (@campuscodi) February 28, 2022
The disclosure of these communications is a devastating blow to the ransomware operation since it provides valuable information to researchers and law enforcement regarding the organization’s internal operations.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security