Contents:
Mint Sandstorm, an Iranian government-backed actor, has been linked to attacks on critical infrastructure in the United States between late 2021 and mid-2022.
The entities that were targeted include seaports, energy companies, transit systems, and a major U.S. utility and gas company. The activity is believed to be a response to attacks on its maritime, railway, and gas station payment systems that occurred between May 2020 and late 2021.
Iran made a statement accusing Israel and the U.S. of being behind the attacks on the gas stations, claiming that it was an attempt to cause instability in the country.
The threat actor previously known as Phosphorus is now being referred to as Mint Sandstorm. Other cybersecurity vendors also monitor this actor under different names, such as APT35, Charming Kitten, ITG18, TA453, and Yellow Garuda, according to The Hacker News.
This Mint Sandstorm subgroup is technically and operationally mature, capable of developing bespoke tooling and quickly weaponizing N-day vulnerabilities, and has demonstrated agility in its operational focus, which appears to align with Iran’s national priorities.
Attack Chain
Mint Sandstorm is said to be associated with the Islamic Revolutionary Guard Corps (IRGC), in contrast to MuddyWater (also known as Mercury or Mango Sandstorm), which is believed to work on behalf of Iran’s Ministry of Intelligence and Security (MOIS).
Redmond’s description of attacks exemplifies the adversary’s capacity to develop and deploy ever-more-sophisticated phishing campaigns designed to breach specific systems.
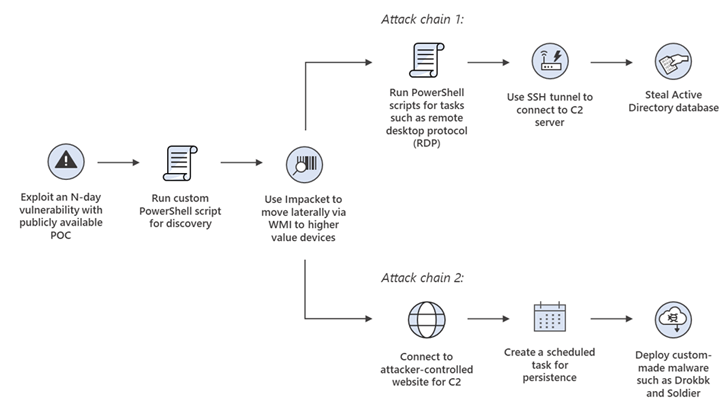
For example, they quickly incorporated publicly disclosed PoCs for exploiting vulnerabilities in internet-facing applications (like CVE-2022-47966 and CVE-2022-47986) into their playbook for gaining initial access and maintaining it.
Even in opportunistic and non-targeted attacks, the threat actor has been known to rely on previously disclosed vulnerabilities, especially in Log4Shell, to gain access to unpatched systems.
A custom PowerShell script is then deployed after a successful breach, and one of two attack chains is initiated. The first attack chain uses more PowerShell scripts to connect to a remote server and steal Active Directory databases.
The second chain involves downloading and installing a bespoke implant called Drokbk and Soldier from an actor-controlled server using Impacket. Soldier is a multistage .NET backdoor that can download and run tools and remove itself.
In December 2022, Secureworks’ Counter Threat Unit (CTU) detailed Drokbk, attributing it to the Nemesis Kitten threat actor group (also known as Cobalt Mirage, TunnelVision, and UNC2448).
Microsoft also identified a threat actor who has been carrying out low-volume phishing campaigns. The actor uses a custom and modular backdoor called CharmPower, which is a PowerShell-based malware capable of reading files, collecting host information, and exfiltrating data.
Check out the following to learn more about: zero-day vulnerabilities, command and control servers, and how to protect your systems against malware.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and YouTube for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








