Contents:
Cybersecurity analysts are warning of ongoing cyberattacks conducted by a suspected Chinese-speaking threat actor. IndigoZebra is now targeting the Afghanistan government as part of an espionage campaign that may date as far back as 2014.
As reported by The Hacker News, “The threat actors behind the espionage leveraged Dropbox, the popular cloud-storage service, to infiltrate the Afghan National Security Council (NSC)”, orchestrating a ministry-to-ministry style deception, where an email is sent to a high-profile target from the mailboxes of another high-profile victim.
The email asked the recipient to review the modifications in the document related to the upcoming NSC press conference.
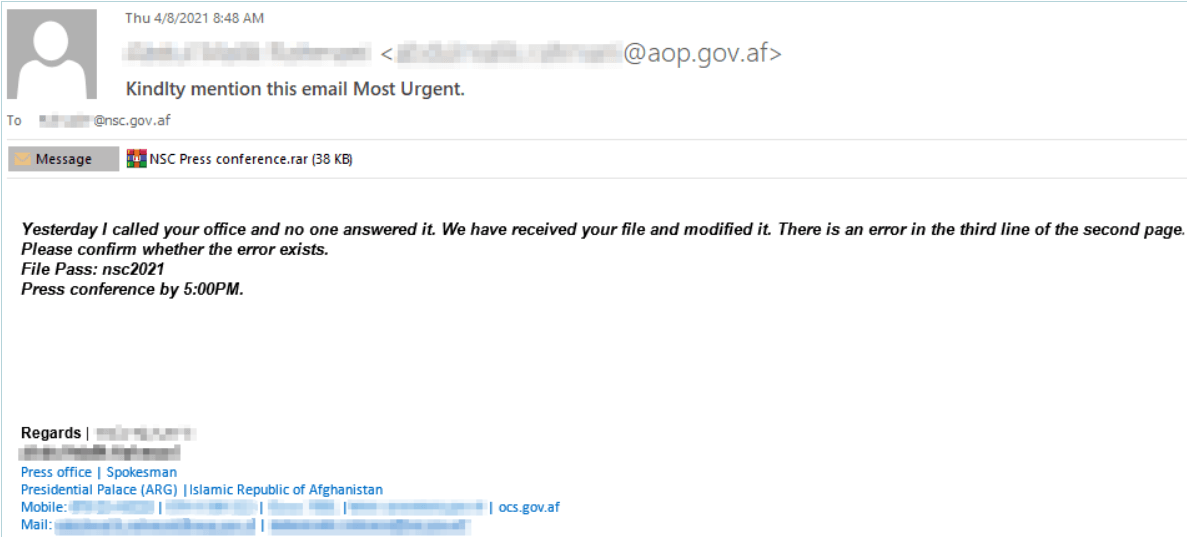
Image Source: CheckPoint
In reality, the email contained a password-protected RAR archive named NSC Press conference.rar. Since extracting the archive with the password provided in the email requires user interaction, it provides a challenge for some sandbox security solutions.
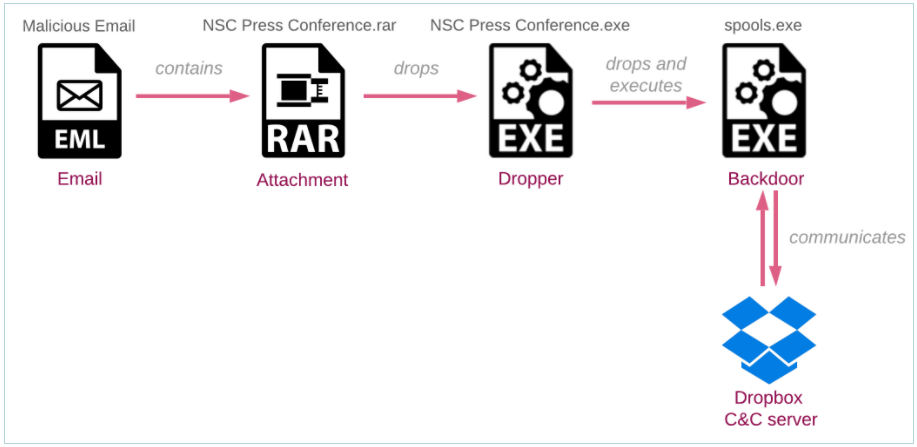
Image Source: CheckPoint
What’s more, the attacks funneled malicious commands into the victim machine that were hidden using the Dropbox API, with the implant creating a unique folder for the victim in an attacker-controlled Dropbox account.
Dubbed “BoxCaon”, the backdoor is capable of stealing confidential data stored on the device, running arbitrary commands, and exfiltrating the results back to the Dropbox folder.
When the attackers need to send a file or command to the victim machine, they place them to the folder named d in the victim’s Dropbox folder. The malware retrieves this folder and downloads all its contents to the working folder. Finally, if the file named c.txt – that contains the attacker command, exists in this working folder, the backdoor executes it using the ComSpec environment variable, which normally points to the command line interpreter (like cmd.exe), and uploads the results back to the Dropbox drive while deleting the command from the server.
The researchers discovered that while the BoxCaon variant was targeting Afghan government officials, the HTTP variants are mainly focused on political entities in Kyrgyzstan and Uzbekistan.
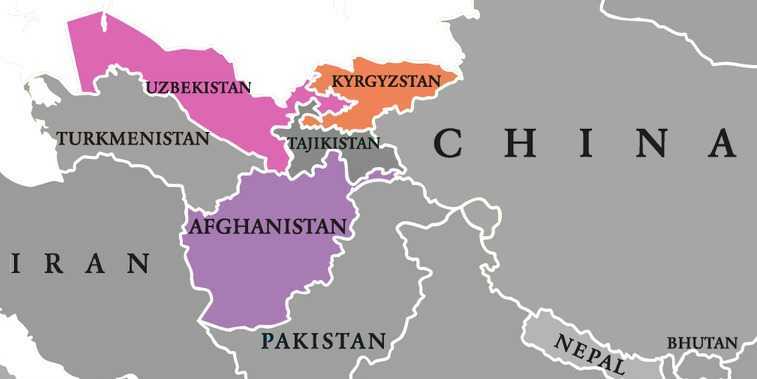
Image Source: CheckPoint
According to Lotem Finkelsteen, head of threat intelligence at Check Point, “What is remarkable here is how the threat actors utilized the tactic of ministry-to-ministry deception.”
While the IndigoZebra actor was initially observed targeting former Soviet republics such as Uzbekistan and Kyrgyzstan, we have now witnessed that its campaigns do not dial down, but on the contrary – they expand to the new targets in the region, with a new toolset.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








