Contents:
A privilege escalation vulnerability in Huawei’s USB LTE dongles has recently been disclosed by Trustwave cybersecurity researcher Martin Rakhmanov.
The Chinese multinational technology company also confirmed the flaw in a security advisory on their website.
Huawei LTE USB Dongle products have an improper permission assignment vulnerability. An attacker can locally access and log in to a PC to induce a user to install a specially crafted application. After successfully exploiting this vulnerability, the attacker can perform unauthenticated operations.
Usually referred to as a Wi-Fi dongle, USB modem, internet stick, USB network adapter, or USB mobile broadband stick, a USB dongle is a small USB device that allows you to access the internet, offering greater flexibility than fixed-line connections.
Rakhmanov revealed improper permissions while analyzing Huawei’s LTE device drivers. The researcher came across the /Library/StartupItems/MobileBrServ/mbbserviceopen.app/Contents/MacOS/mbbserviceopen file which would auto-run every time the USB dongle was plugged in, while browsing through the driver files installed by the dongle on his Mac OSX machine. The file would open up a web browser with Huawei’s device management interface.
Rakhmanov noticed the “mbbserviceopen” file ran with full permissions (777), as seen below:
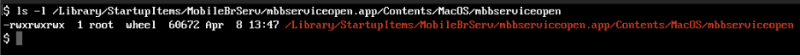
Image Source: Trustwave
According to the researcher,
This file has a special purpose: when a user logs on to the computer and inserts the dongle, that file is automatically executed to open up a web browser with the device management interface. All a malicious user needs to do is to replace the file with their own desired code and wait for a legitimate user to start using the cellular data service via Huawei device.
Privilege escalation attacks occur when a threat actor gains access to a user’s account, bypasses the proper authorization channel, and successfully grants themselves access to sensitive data. When deploying these attacks, threat actors are typically attempting to exfiltrate data, disrupt business functions, or create backdoors.
According to BleepingComputer, since this flaw tampers with the Huawei driver software installed on a computer, local or physical access to the computer is required, making this a case of local privilege escalation.
The issue affects multiuser environments where one user account can execute code as another user without the latter one knowing about it. Malicious actors can take advantage of vulnerabilities like this by getting an initial foothold that triggers the installation of more robust malware.
Huawei issued an advisory with the remediation instructions and has advised users of its USB LTE dongle (E3372) to obtain the “Hi Link” driver files from their website to fix the vulnerability.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










