Contents:
Ireland’s Health Service Executive, the country’s publicly funded healthcare system, had to shut down all of its IT systems after suffering a Conti ransomware attack.
“We have taken the precaution of shutting down all our IT systems in order to protect them from this attack and to allow us fully assess the situation with our own security partners,” the Irish national health service said.
There is a significant ransomware attack on the HSE IT systems. We have taken the precaution of shutting down all our our IT systems in order to protect them from this attack and to allow us fully assess the situation with our own security partners.
— HSE Ireland (@HSELive) May 14, 2021
The IT outage led to a massive disruption in the country’s healthcare, therefore causing limited access to diagnostics and medical records as well as transcription errors due to handwritten notes, and slow response times to healthcare visits.
The purpose of this memo is to provide clinical advice and guidance for clinical services during the HSE IT System CyberAttack. This memo will summarise the principles informing the response, note the risks inherent in the current situation, and provide general advice. It is noted that the risk is global, affecting all elements of services, and the breadth and depth of clinical practice. For the purposes of this document, diagnostics refers to the laboratory, radiology, cardiac catheterization labs and echocardiography, endoscopy, diagnosis of stroke type, amongst others.
Recently a cybersecurity researcher shared a screenshot of a chat between Conti and Ireland’s HSE with the journalists at BleepingComputer.
In the screenshot, we can see the Conti gang claiming to have had access to the HSE network for two weeks and allegedly have stolen 700 GB of unencrypted files, including patient info and employee info, contracts, financial statements, payroll, and more.
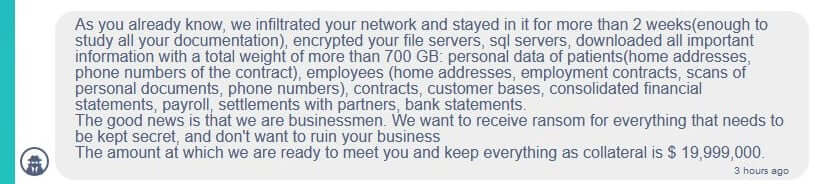
Conti said they would provide HSE with a decryptor and also delete the stolen data if a ransom of $19,999,000 is paid.
Taoiseach Micheál Martin, the Prime Minister of Ireland, said that no ransom will be paid.
‘We’re very clear we will not be paying any ransom or engaging in any of that sort of stuff’ Taoiseach @MichealMartinTD says of the ransomware attack on the HSE | Live blog: https://t.co/itscpwqdS7 pic.twitter.com/Pl4A4JNOST
— RTÉ News (@rtenews) May 14, 2021
In order to be able to understand the importance of the attack, we need to take a closer look at the Conti ransomware operation.
The ransomware operation is believed to be run by a Russia-based cybercrime group known as Wizard Spider, with the group using phishing attacks in order to install the TrickBot and BazarLoader trojans in order to obtain remote access to the infected machines.
Using this method, the threat actors are able to spread laterally through a network whilst stealing credentials and harvesting unencrypted data stored on workstations and servers.

Heimdal™ Ransomware Encryption Protection
- Blocks any unauthorized encryption attempts;
- Detects ransomware regardless of signature;
- Universal compatibility with any cybersecurity solution;
- Full audit trail with stunning graphics;
Once the hackers have stolen everything of value and gained access to Windows domain credentials, they will deploy the ransomware on the network and encrypt all of its devices. The ransomware gang will use the stolen data as leverage in order to force its victims into paying a ransom by threatening to release it on their ransom data leak site.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








