Contents:
Altus Group, a leading provider of software, data solutions, and independent advisory services to the global commercial real estate industry announced on June 14th that it had suffered a security breach. A week later, they reported “no evidence of impact”.
One day before releasing the announcement below, the provider’s IT back-office and communications systems, such as email have been taken offline, due to a breach.
Altus Group Limited (“Altus Group”) (TSX: AIF), announced that on June 13, 2021 it determined it had experienced a cybersecurity incident impacting some of its information technology systems. The Company took immediate action activating its cybersecurity protocols, is notifying authorities, and has engaged with cybersecurity experts who are assisting to resolve the incident. A client business continuity protocol has been implemented and client products and services are accessible while as a precautionary measure all IT back-office systems were taken offline.
Throughout the further updates, the company refused to disclose whether any information was actually leaked. According to the CyberNews team, their data may have possibly been leaked by the Hive ransomware group.
Who is Hive?
Hive seems to be a new ransomware group with no prior history of breaches. The threat actors published a hidden service (darknet) website this week called HiveLeaks, which includes only one entry – the Altus Group.
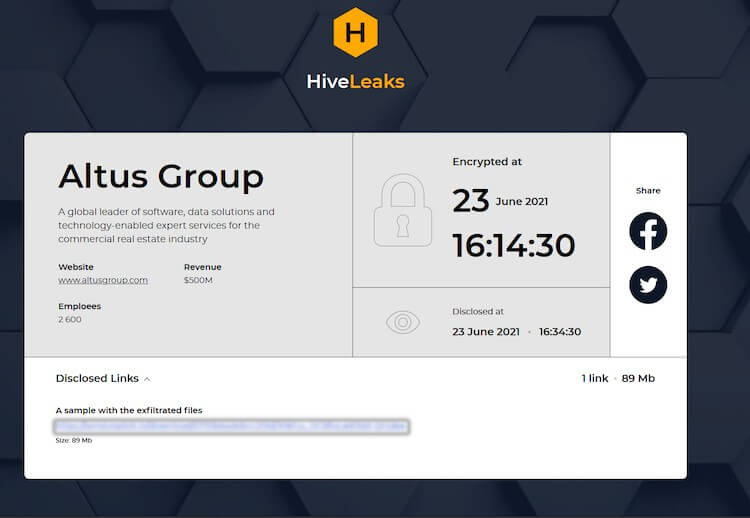
Image Source: CyberNews
Since Hive currently states the data to be “encrypted”, suggesting that Altus Group is given the chance to pay a ransom, it is safe to assume we’re dealing with a ransomware gang.
The sample of exfiltrated files includes business data and documents, as well as Argus certificates and several development files. Although the sample archive is password-protected, the file names and types are clearly visible.
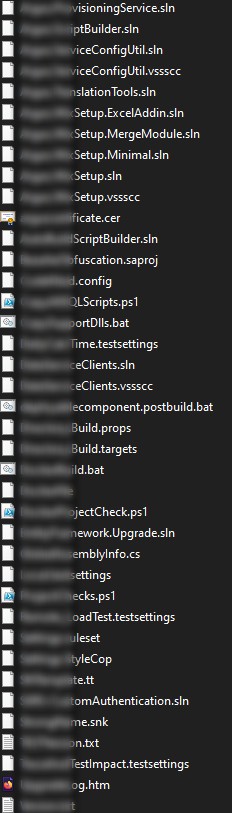
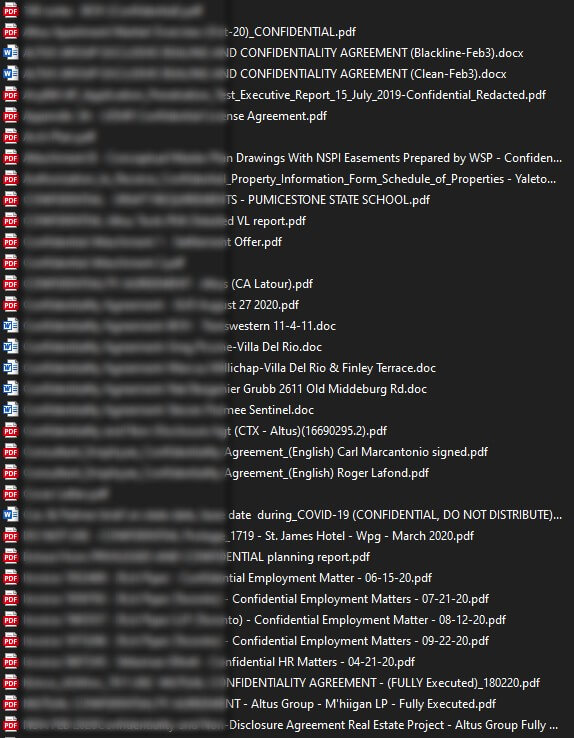
Images Source: CyberNews
Altus Group has been informed about the recent discoveries and is yet to respond or acknowledge the legitimacy of the leaked data, its connection to attack, or whether or not the ransomware group has requested payment to keep them out of trouble.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security