Contents:
Yesterday we looked into the biggest cryptocurrency hack that ever happened, today we talk about how the attackers decided to give back the money they have stolen during it.
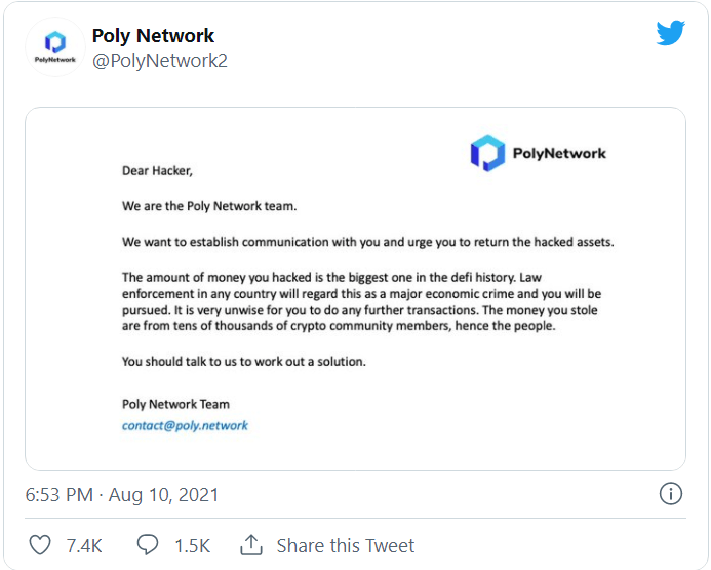
Yes, you heard it right! The cybercriminals behind the Chinese Internet protocol Poly Network attack who have stolen approximately $600 million worth of cryptocurrency assets began to return it, as shared by the organization on Twitter.
— Poly Network (@PolyNetwork2) August 11, 2021
So far, the hacker has reimbursed $256 million Binance Smart Chain (BSC) tokens, $3.3 million in Ethereum tokens, and $1 million in USD Coin (USDC) on the Polygon network, but decided to keep the rest of it for the negotiations with the cross-chain DeFi protocol.
In order to have back in its account all the assets that have been stolen, Poly still needs to receive the difference of $269 million on Ethereum and $84 million on Polygon.
Why Did the Attackers Return the Money to Poly Network?
It’s not the first time the hackers said they are willing to return the stolen assets, which made many believe that the attack may have been meant to show the Chinese company it needs better protection against cybercriminals, just like a white-hat hacker would do.
A white-hat hacker (a good hacker) is a computer security expert whose job is to breach secured networks in order to test their security.
On the other side, chief scientist at blockchain analytics firm Elliptic Tom Robinson thinks that giving back the stolen cryptocurrency shows that even if you can steal it, laundering and converting them might be an inconvenience “due to the transparency of the blockchain.”
It could also be the blockchain security company SlowMist announcement that they have identified the cybercriminal’s ID, email address, IP information, and device fingerprint.
The firm also stated that the hacker’s resources were initially in monero (XMR), but were swapped for BNB, ETH and MATIC, and other tokens that were used to sponsor the cyberattack.
Or maybe it was Poly Network’s message?
In an AMA (Ask Me Anything) session the attackers declared they have attacked the Poly Network platform for fun and because “cross-chain hacking is hot.”
We can make assumptions, but we don’t know for sure the real reason why the hackers have returned the crypto-assets they have stolen two days ago.
How Did the Attack Happen in the First Place?
The hackers behind the Poly Network hack took advantage of a flaw between contract calls which enabled them to obtain ownership of crypto-assets and move them to attacker-controlled wallets:
- Ethereum: 0xC8a65Fadf0e0dDAf421F28FEAb69Bf6E2E589963
- Binance Smart Chain: 0x0D6e286A7cfD25E0c01fEe9756765D8033B32C71
- Polygon: 0x5dc3603C9D42Ff184153a8a9094a73d461663214
After preliminary investigation, we located the cause of the vulnerability. The hacker exploited a vulnerability between contract calls, exploit was not caused by the single keeper as rumored.
— Poly Network (@PolyNetwork2) August 10, 2021
This attack is mainly because the keeper of the EthCrossChainData contract can be modified by the EthCrossChainManager contract, and the verifyHeaderAndExecuteTx function of the EthCrossChainManager contract can execute the data passed in by the user through the _executeCrossChainTx function.
Therefore, the attacker uses this function to pass in carefully constructed data to modify the keeper of the EthCrossChainData contract.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










