Contents:
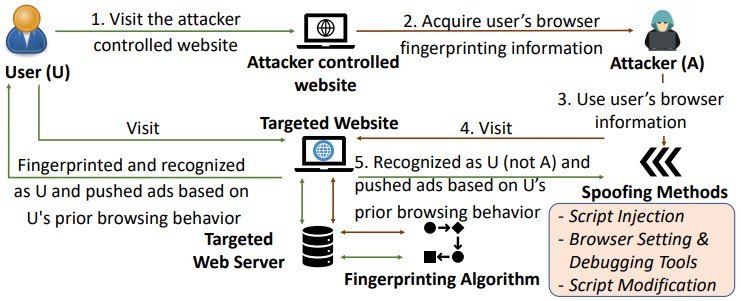
Academic experts from a U.S. university designed a new type of cyberattack dubbed Gummy Browsers. Its main characteristics include the capturing of fingerprints and also tricking the browser.
Gummy Browsers Attack: How It Might Unfold
According to BleepingComputer, the method of the Gummy Browsers attack follows a pattern where a victim is determined to access a malicious website, so this would be the moment when hackers could get their fingerprints. Having this, cybercriminals can go to a target platform in order to perform identity spoofing.
Experts generated by means of already existing scripts or customs ones a user fingerprint. Then they developed 3 methods to get the user spoofed on different websites.
Method 1 – Injecting script
With executing scripts like Selenium, for instance, that contains JavaScript API calls extracted values, a fingerprint can be spoofed.
Method 2 – Tool debugging and setting of the browser
These tactics are useful if browser attribute change is desired, the attribute can be modified into any customized value. These will have an impact firstly on the JavaScript API and secondly on the matching value from the HTTP header.
Method 3 – The altering of the script
The properties of the browser can be changed with spoofed values. This could be done if, before the website scripts are sent to the webserver they are modified.
Fingerprinting Systems Can Be Tricked
As the researchers mentioned in the paper they published, they managed to mislead fingerprinting systems such as FPStalker and Panopliclick after a one-time victims’ fingerprinting capturing.
Our results showed that Gummy Browsers can successfully impersonate the victim’s browser transparently almost all the time without affecting the tracking of legitimate users. (…) Since acquiring and spoofing the browser characteristics is oblivious to both the user and the remote web-server, Gummy Browsers can be launched easily while remaining hard to detect.
The Threat Is Real
The threat of a Gummy Browsers attack is real, the identity spoofing can determine a script to be confused to a human, making it seem like this is not a bot.
Authentication services normally have certain security features intended to check if a user is legitimate or not. Let’s take Oracle, Inauth, or SecureAuth IdP for instance. The Gummy Browser attack may be used as a means to avoid these kinds of security checks. On that score, SecureAuth IdP for example can be made not to use MFA if a legitimate fingerprint is detected.
The impact of Gummy Browsers can be devastating and lasting on the online security and privacy of the users, especially given that browser-fingerprinting is starting to get widely adopted in the real world. In light of this attack, our work raises the question of whether browser fingerprinting is safe to deploy on a large scale.
What Is a Digital Fingerprint and What Is It Used for?
A digital fingerprint stands for an online identifier that is unique belonging to a certain user and depending on some device features like the IP address, the operating system version, add-ons, cookies, and so on.
What’s its purpose then? A digital fingerprint is especially useful for advertisers and different websites can use this type of data to check if the user is a real human being or in targeted advertising scopes. Authentication systems use digital fingerprints too (like MFA). Also, they represent a security measure, part of banks’ fraud detection mechanisms.
Did you enjoy this article? Follow us on LinkedIn, Twitter, Facebook, Youtube, or Instagram to keep up to date with everything we post!










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








