Contents:
New GrimResource technique exploits a 2018-old, unpatched, Windows XSS flaw and crafted MSC files to deploy malware via the Microsoft Management Console (MMC).
Researchers detected the new exploitation technique in the wild on June 6th, 2024. Exploiting the Microsoft Management Console could enable hackers to evade security measures and gain initial access.
Although researchers reported finding the vulnerability in October 2018, the flaw still affects the latest Windows 11 version and didn’t receive a patch.
The GrimResource code execution technique explained
The first step in this complex process is the hackers tricking their target to click on a forged MSC file. Reportedly, researchers observed how the attackers contact their victim on Facebook and have them downloading a Word document.
The document is actually an MSC file that mimics a Word document. The hackers forged the file’s icon so that it looks like a Word, not an MSC document. They also changed the “Run” button to “Open”, to avoid raising suspicion.
When the victim clicks “Open”, the GrimResource technique exploits a cross-site scripting (XSS) vulnerability in the apds.dll library. By using it along with crafted MSC files, hackers can execute arbitrary JavaScript in the context of mmc.exe.
Further on, they use DotNetToJScript to execute a .NET loader dubbed PASTALOADER. The loader retrieves the payload from environment variables and injects it into a new dllhost.exe instance. One of the final payloads the researchers observed was Cobalt Strike.
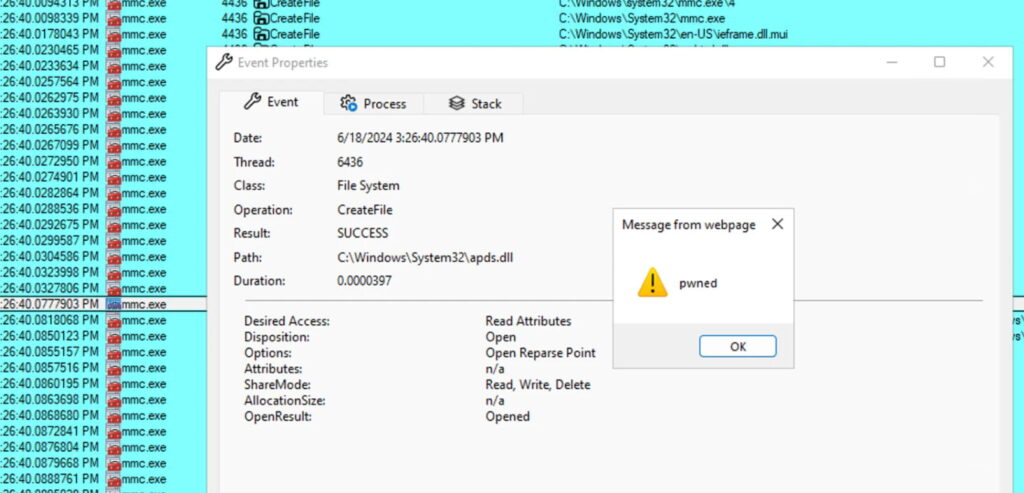
Source – Cyberinsider.com
How to detect a GrimResource operation
To detect a potential GrimResource attack, System Administrators should check:
- File operations that involve apds.dll invoked by mmc.exe.
- Suspicious executions via MCC, like processes spawned by mmc.exe with .msc file arguments.
- RWX memory allocations by mmc.exe that originate from script engines or .NET components.
- Unusual .NET COM object creation within non-standard script interpreters like JScript or VBScript.
- Temporary HTML files created in the INetCache folder as a result of APDS XSS redirection.
Threat detection helps keeping safe your environment, but preventing the threat works better. Just like many other attacks, the GrimResource also relies on online malicious communication.
Using a DNS filtering tool helps spot and block harmful connections before the hackers get to enter your system. Heimdal’s predictive DNS has a 96% accuracy rate in detecting malicious domains even if they weren’t yet listed as such.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and Youtube, for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security







