Contents:
Cybersecurity researchers have recently disclosed details of the Chinese-based threat actor GhostEmperor who allegedly targeted several south-east Asian countries for more than a year.
According to Kaspersky specialists Mark Lechtik, Aseel Kayal, Paul Rascagneres, and Vasily Berdnikov, all this time, the threat actors attacked governmental entities and telecommunication firms from South Asia using a rootkit which acts as a backdoor to maintain persistence on vulnerable servers.
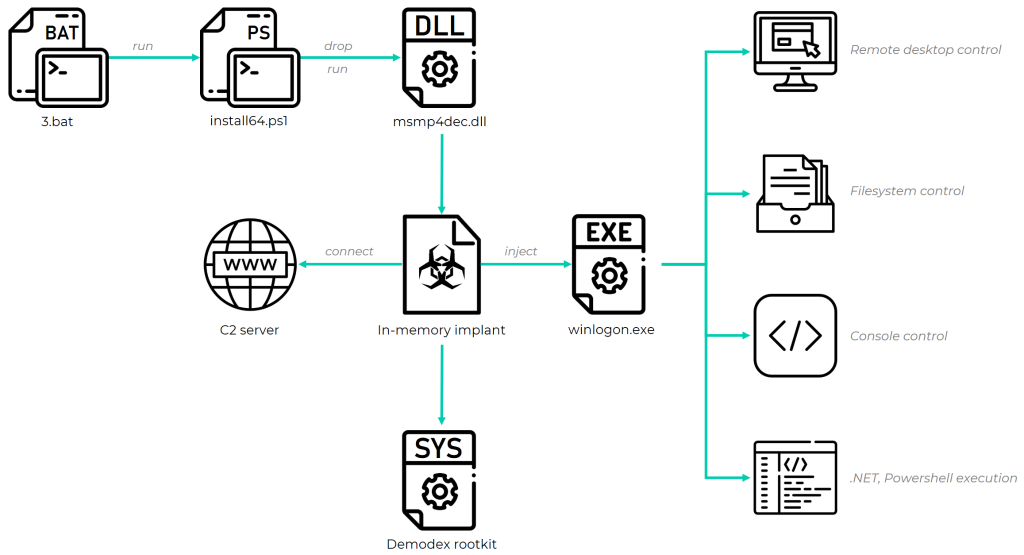
The rootkit dubbed Demodex had been adapted to work on Windows 10.
The main objective of this backdoor is to conceal malware artifacts such as documents, registry keys, and network traffic in order to avoid being noticed by forensic experts and prevention systems.
To bypass the Windows Driver Signature Enforcement mechanism, GhostEmperor uses a loading scheme involving a component of an open-source project named ‘Cheat Engine.
This advanced toolset is unique and Kaspersky researchers see no similarity to already known threat actors. Kaspersky experts have surmised that the toolset has been in use since at least July 2020.
The hackers used known flaws in Internet-facing server software, such as Apache, Windows IIS, Oracle, and Microsoft Exchange, to compromise their targets’ systems.
According to BeleepingComputer, the Chinese-speaking hacking group also uses a “sophisticated multi-stage malware framework” that enables the cybercriminals having remote control over the impacted machines to provide remote control over the affected systems.
[8/n] We assess that the common infection vectors were exploitation of public facing web servers and ProxyLogon, which we saw being used as early as March 4, two days after the CVE was released. pic.twitter.com/rtMk6WPPAt
— Mark Lechtik (@_marklech_) September 30, 2021
GhostEmperor’s Victims
Among the countries targeted by the GhostEmperor group were Vietnam, Malaysia, Thailand, and Indonesia. In addition, according to the researchers, countries such as Egypt, Ethiopia, and Afghanistan were also on the threat actors’ list.
They noticed that the last three had strong connections to south-east Asian countries.
We observed that the underlying actor managed to remain under the radar for months, all the while demonstrating a finesse when it came to developing the malicious toolkit, a profound understanding of an investigator’s mindset, and the ability to counter forensic analysis in various ways.
The attackers conducted the required level of research to make the Demodex rootkit fully functional on Windows 10, allowing it to load through documented features of a third-party signed and benign driver.
This suggests that rootkits still need to be taken into account as a TTP during investigations and that advanced threat actors, such as the one behind GhostEmperor, are willing to continue making use of them in future campaigns.
In Kaspersky’s analysis and article, you can find more information about the techniques used by GhostEmperor and the newly discovered rootkit Demodex.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










