Contents:
Four Android Applications listed on Google Play with over 1 million downloads were infected with the malware Android/Trojan.HiddenAds.BTGTHB, according to an analysis performed by cybersecurity researchers.
The apps are directing users to sites that steal credentials or generate pay-per-click income for the operators. Some of these websites encourage users to download phony security updates or tools in an effort to lure them into manually downloading malware.
The Four Apps with 1M+ Installs
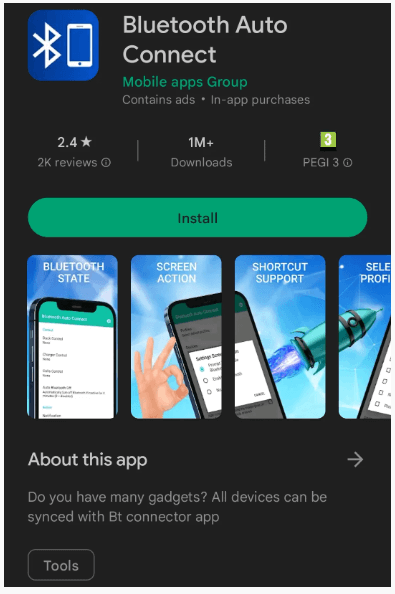
The apps have more than a million installs and are still available on Google Play through a developer account called ‘Mobile apps Group’.
The same developer was previously exposed twice for deploying adware on PlayStore, but after submitting cleaned-up versions, continued to publish apps, according to the Malwarebytes report.
The four malicious applications are:
- Bluetooth Auto Connect, with over 1,000,000 installs;
- Bluetooth App Sender, with over 50,000 installs;
- Driver: Bluetooth, Wi-Fi, USB, with over 10,000 installs;
- Mobile transfer: smart switch, with over 1,000 installs.
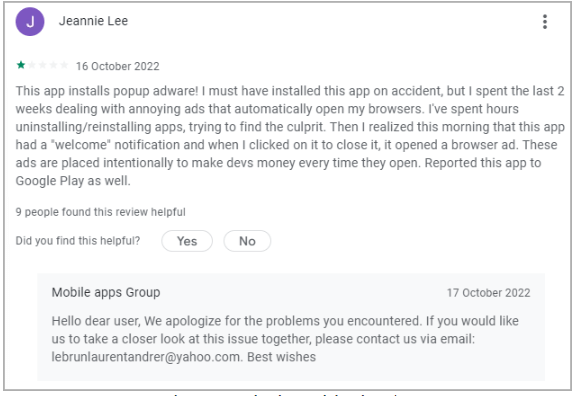
According to Bleeping Computer, on Google Play, the apps have negative reviews, and many users have complained about the intrusive ads that launch by themselves in new browser tabs. The developer moderated the reviews and answered some of the comments, offering to assist in fixing the ad issues.
The Malware’s Behavior
Malwarebytes observed the behavior of the software from Mobile Apps Group and noticed that the apps have a delay of 72 hours before displaying the first ad or opening a phishing link in the web browser. Then, every two hours, the apps open new tabs with similar content.
According to the researchers, new browser tabs continue to open even while the device is locked. As a result, when users return to their phones after being away from them for a while, they discover that many phishing and advertising websites have been launched.
The full research report is available here.
As a general rule, it is best to avoid installing suspicious apps from Android marketplaces or APK stashes. Reading user evaluations, as well as monitoring power usage and network data activity, might also be good practices to determine whether the device is running malicious software.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










