Contents:
There’s no doubt in my mind that the threatscape has changed – new malicious strains rising to wreak havoc, traditional (and outdated) countermeasures failing, ML and AI stepping up to the plate to create actionable mediation (and remediation) strategies.
In this scenario, where everything moves faster than light to keep up with the challenges, it’s quite unlikely to find something hinting to “the old ways”, which in this case, broadly refers to the whole malware-riddance “Machinarium”, with the limelight, of course, falling on the antivirus.
Yet, there is hope for ‘traditional’ solutions, the firewall beings amongst them, or, better said, the only one that has aced the test of time.
In this article, we are going to take a closer look at firewalls – how they work, why they’re still in place, how many firewall types are there, and, of course, why they should be a part of your company’s cyber-resilience plan.
What exactly is a firewall? Some tips on how to choose the best one for your company
Going back to the basics, a firewall is a network security device that monitors outgoing and incoming traffic. Basically, it’s the IT equivalent of a TSA officer (no disrespect intended, of course), checking the passengers as they pass through the airport’s security gates.
Firewalls can be physical devices (i.e. hardware firewall), but also be deployed in software form (i.e. Microsoft Windows’ Defender Firewall). Firewalls, regardless of form, do more than checking inbound/outgoing traffic – they also ensure that user-defined rules are observed.
Here’s an example of how a firewall works: in keeping with the airport controller metaphor, let’s imagine a random person going through the checkpoint. It’s the officer’s job to check that person’s ID and inquire about the destination. On the IT side, this translates to the firewall inquiring about the IP and source of the transmission.
At this point, I should introduce two concepts called whitelist and blacklist. Simple enough to understand – what’s on the whitelist is good and what’s on the blacklist is bad. Now, after the ‘inquiry’ stage, the officer will check the person’s credentials against the two lists. If he’s on the whitelist, he can go through. If not, well, he will have some explaining to do.
The same thing happens on the traffic level – incoming packages get checked. If the transmission comes from a safe source (on the white list), they will be allowed to pass. If not, the connection will be severed.
Although the term “firewall” appears to be universal, there are, in fact, several types of firewalls, each designed to address (and overcome) a certain network security challenge. Let’s take a close look at the various firewall types.
Personal firewall
Endpoint-centric traffic monitoring and management solution. Protects a single endpoint (i.e. desktop computer, laptop, tablet or smartphone) and is usually a part of a larger cybersecurity software package. For all-purpose and intent, the Windows Defender Firewall can be considered a personal firewall, interposing itself between the machine and the Internet. Software-wise, there are a lot of choices.
Packet-filtering firewall
Moving further down the list, we have yet another basic firewall type – the packet or package-filtering firewall. A little more secure compared to the personal firewall, the packet-filtering variety adds more muscle to a multi-device network, such as the ones run by small businesses.
This type of firewall has pre-determined rules and policies, which allows it to generate various types of filtering criteria: allowed IP addresses, packet protocol headers, port numbers, and the types of data-bearing packets.
Packet-filtering firewalls are what we call “in-line defenses”, meaning that they are placed at junction points such as routers or switches.
This type of firewall has but only one caveat: it simply compares the transmitted packages against a predetermined list, meaning that there’s no way to route some that get flagged are suspicious. Packet-filtering firewalls simply discard the packets that do not match the criteria. Discarded packets cease to exist. Daunting perspective, don’t you agree?
Circuit-level gateway (firewall)
The methods enumerated so far, are architecture-centric, meaning that they do not factor in the context nor the content of the data packages. Circuit-level gateways are cheap and somewhat efficient ways of providing some insight into what is being relayed during the communication.
To identify potentially malicious data packets, circuit-level gateways inspect any (and all) network protocols used during the data transmission.
This includes TCP handshakes and subsequent encryption keys. Again, this is just one of the many instruments employed to verify the context and some content. Unfortunately, it’s a blunt one, since circuit-level gateways cannot perform in-depth analyses on the packets’ content.
Stateful inspection firewall
Since the entire malware industry is focused on creating variants that circumvent detection grids, there is, indeed, a need for a firewall capable of inspecting the contents of each package. Enter the stateful inspection firewall, which is, more or less, the IT equivalent of a customs officer, in charge of checking every parcel and suitcase before the owner can retrieve it and go about his business.
Stateful inspection firewalls, albeit more expensive and difficult to deploy compared to the other items on our list, can inspect the contents of each data packet. More than that, it can ascertain whether or not that packet or ‘bundle’ is part of or has been requested during an active network session.
Another caveat that comes to mind is that stateful inspection firewalls can take quite a toll on your network’s performance, by increasing the latency. Of course, it does tend to make up for this with the extra ‘muscle’ it brings.
Proxy firewall
In every aspect, the proxy firewall can be considered the love-child of the packet-filtering firewall and the circuit-level gateway. In more technical terms, this packet-inspection technique interposes a firewall-enabled proxy server between the client (your machine) and the rest of the Internet.
Often called application-level gateways, these types of firewalls have dynamic filtering capabilities – capable of filtering packets according to the service they are attempting to access. Additionally, they can call up additional criteria, such as the HTTPS request string.
Since it’s phenotypical, the proxy firewall also has the same packet-inspection capabilities as the gateway. On the other hand, just like in the case of the stateful inspection firewall, the proxy firewall can impact your network’s performance.
Hybrid firewall
The epitome of firewall technology, hybrids combine advanced packet-scanning techniques, such as deep-packet inspection, with antivirus antimalware software. A hybrid firewall will inspect every aspect of a web browsing session, right down to the content of each transmitted packet.
More than that, hybrids have the capability of performing deep packet analyses. For instance, they can ‘figure out’ if the packets came from a legitimate source by piecing together the entire server reply, which is made of many more data packets.
As you would imagine, hybrid firewalls are the go-to solutions if you want to ensure that no malicious packets slip through. With the built-in AV\AM, it can provide HIDS and HIPS.
However, just like the other types of deep packet inspection firewalls, hybrids can also impact your network’s performance. More than that, hybrids can impact your organization’s resources as well, since they require front-end maintenance.

- Next-gen Antivirus & Firewall which stops known threats;
- DNS traffic filter which stops unknown threats;
- Automatic patches for your software and apps with no interruptions;
- Privileged Access Management and Application Control, all in one unified dashboard
Forensic Analysis of Brute-Force Attack: Pre- and Post-Pandemic Patternization
Regardless of their nature and functionality, firewalls should offer some degree of protection against malicious connection attempts. Of course, a firewall alone cannot protect the machine against advanced, second-generation e-threats, but they can prevent less ‘sophisticated’ malicious attempts such as brute-force attacks. Despite having a lesser degree of success compared to other cyber-attacks (i.e. keyloggers) BF-type malware can become very effective if unleashed upon unsecured or poorly secured networks and/or machines.
Heimdal™ Security’s internal data has revealed that the number of brute-force attacks have increased exponentially in the wake of the ‘remote work exodus’. Our company’s data points out that there has been a 5% increase in BF attacks after employees were ordered to observe self-quarantine conditions.
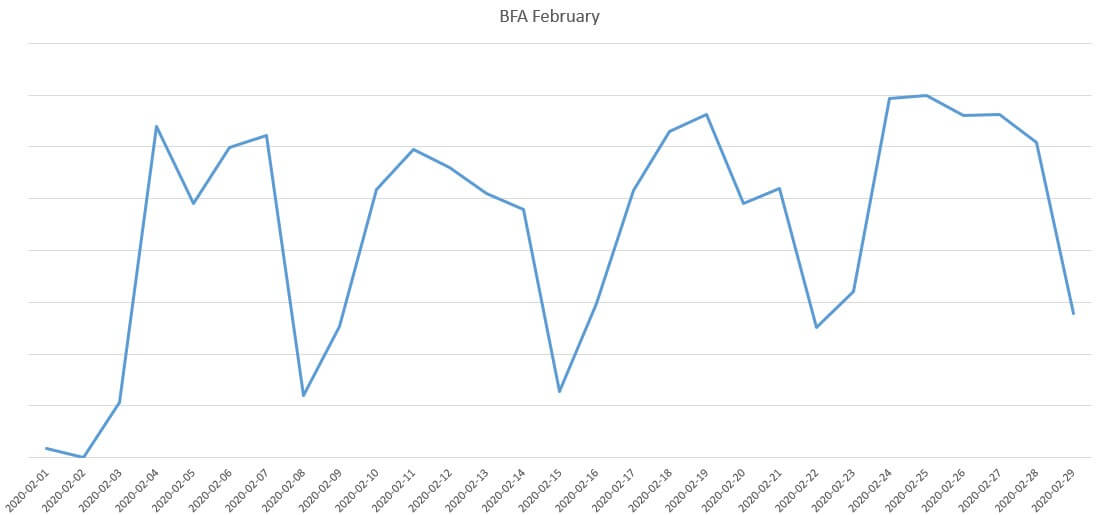
Chronologically, a spike in BF-type aggressions has been detected in or around the 2nd of February, coinciding with WHO’s statements regarding the coronavirus situation blowing out of proportion. Until the beginning of February, the network protection agent on a single machine would detect and block an average of 15 – 20 brute-force attempts per day.
However, moving further into February 2020, we see a significant increase in daily brute-force attacks; in some cases, our telemetry shows a 700 – 800% increase compared to the previous months (i.e. December and January).
A plausible explanation may be that the companies have had scaling trouble – infrastructure could not accommodate so many remote work requests. This, in turn, led to sysadmins focusing more on ways to solve related issues (i.e. post-transmission data-consistency, revoking super-user accounts, expanding/upgrading the hardware), while deprioritizing cybersecurity.
As mentioned, February come, the number of BF attacks has increased. Our telemetry shows a spike towards the end of the month; the ‘bulk’ (circa 10% of detected and blocked BF attacks) has been seen on the 25th of February, the lowest count being registered on the second of the month. Below, you will find a graphical representation of how the brute-force attack phenomenon evolved throughout the month of February.
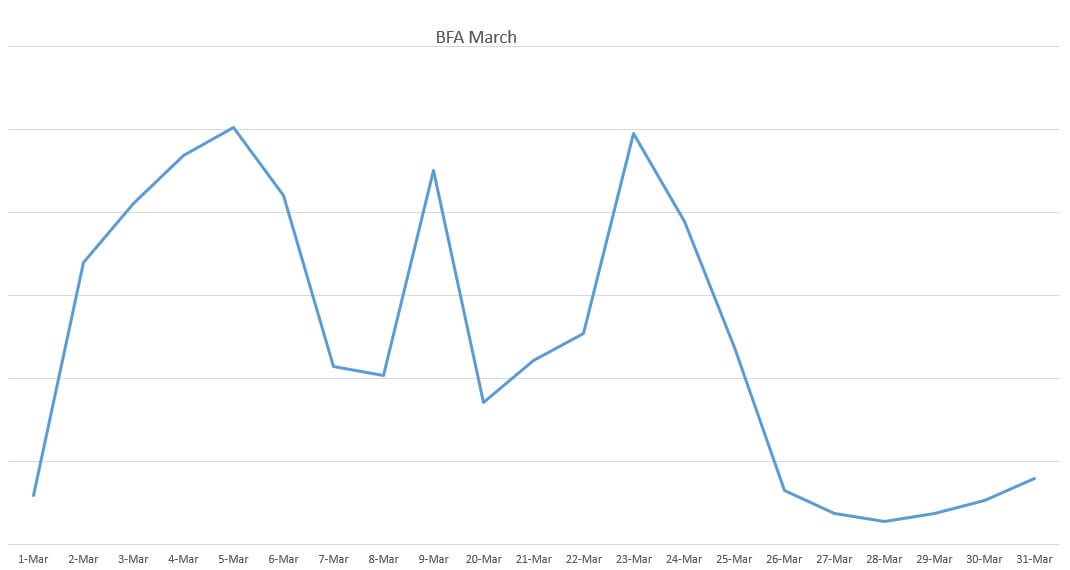
In March, WHO declares the coronavirus outbreak a pandemic. Companies around the world were either forced to shut down their operation or send their employee to work remotely. With an increase in telecommuters, both ISPs and infrastructure are under tremendous stress. Concomitantly, a rise in brute-force attack numbers is also observed.
On the average, around 5,000 brute-force attempts have been detected in May, compared to 3,500 in February (42,72% increase for the February-March timeframe). Furthermore, our telemetry shows a massive brute-force attacks spike (circa 10% of March attacks) in or around the 5th of March, coinciding with the beginning of the work-from-home migration. See the graph below to review the March brute-force attack evolution.
Outlook
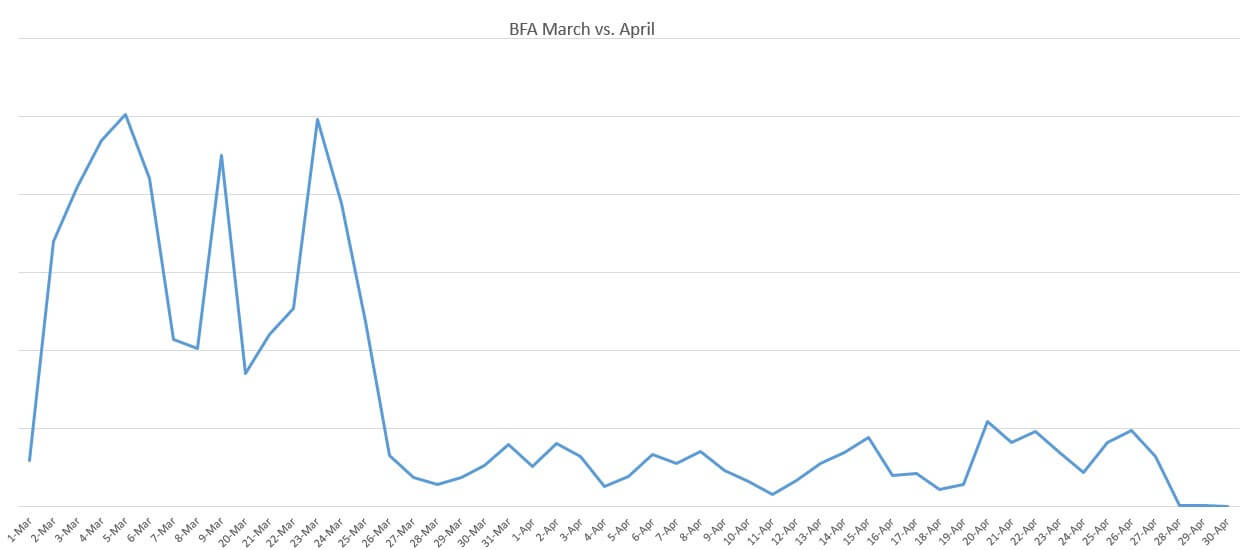
According to Heimdal™ Security’s data, in April, we have registered a 200% decrease of brute-force attack cases (compared to March). This dramatic drop in cases can be attributed to Heimdal’s advanced firewall brute-force attack blocking feature, which actively monitors the incoming traffic in search for data packets that match the BFA profile.
The feature is available as part of our company’s Endpoint Security Suite. Outlook-wise, our forecasts show that brute-force attacks will effectively decrease both in number and strength. Please see the graph below to review the April vs. March trend of the BFA phenomenon.
Wrap-up
In my (most humble) opinion, firewalls aren’t going anywhere. Of course, we shouldn’t rely solely on the firewall to keep e-threats at bay. That being said, a complete cybersecurity solution is the way to go forward, especially during these trying times. Stay safe!










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security