Contents:
This service allows users to search for compromised passwords, therefore by using this service, a visitor is able to input a password and see how many times that specific password was discovered in a breach.
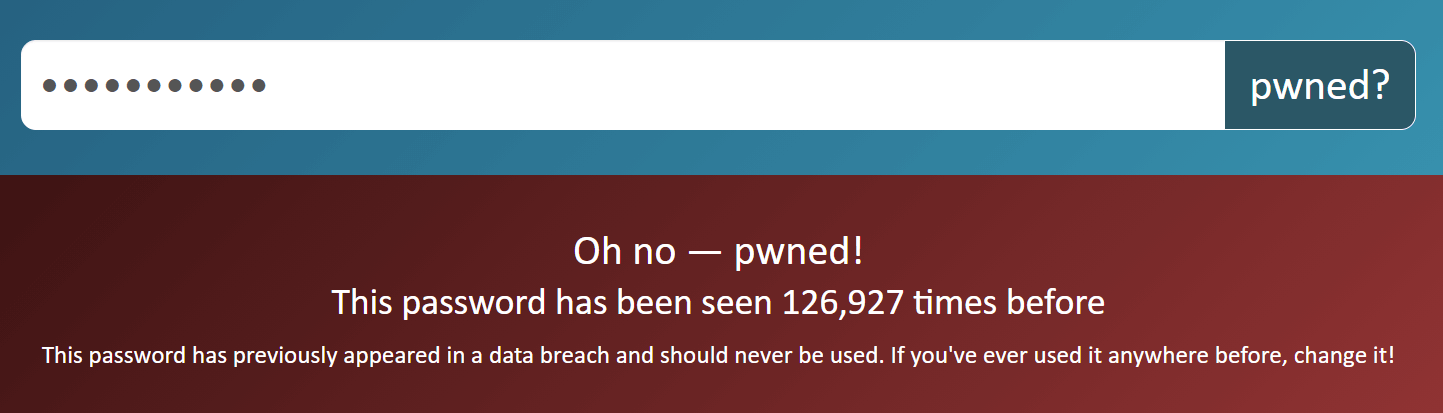
Let’s choose randomly a password from my colleague’s article about the funniest passwords and try our luck with Password123, which the service shows being used 123.927 times in data breaches.
Troy Hunt, the Have I Been Pwned creator announced that the FBI would be feeding compromised passwords found during law enforcement investigations into the Pwned Password service.
By providing this feed, the FBI will let administrators and users check for passwords known to be used for malicious purposes, thus letting admins change the passwords before they could be used in credential attacks and network breaches.
We are excited to be partnering with HIBP on this important project to protect victims of online credential theft. It is another example of how important public/private partnerships are in the fight against cybercrime.
The FBI is going to share the passwords as SHA-1 and NTLM hash pairs that can then be searched using the service or downloaded as part of Pwned Password’s offline list of passwords.
Password Pwned is also allowing its users to download the compromised passwords as lists of SHA-1 or NTLM hashed passwords that can be used offline by Windows administrators to check if they are being used on their network.
You can download these lists with the hashes sorted alphabetically or by their prevalence.
In order to help facilitate this new partnership, Hunt has made Password Pwned open source via the .NET Foundation and is asking other developers to help create a ‘Password Ingestion’ API.
This is something I’ve given a lot of thought to for a long time now. The concept of open sourcing HIBP has been floated over and over again and it’s taken a failed M&A process to help me realize that this was the best path forward, but now here we are.
I’ve used the word “community” a lot throughout this post and I can’t understate the importance of the role other people have played in the project’s success. Just to really drive that point home, look at how many breaches have gone into HIBP in the last two weeks. At the time of writing, that’s 16 breaches encompassing 95,850,490 records and every single one of those has been a community contribution; someone selflessly standing up and trusting me to handle the data in the best interest of others. I focus on that short time frame in particular here because it also demonstrates the constant flood of data and the need to scale myself more efficiently.
So that’s where HIBP is heading. I know this blog post will be met with much enthusiasm because that’s what many of you have been telling me to do for a long time. I’ve listened, now it’s time to make it a reality ?.
The FBI and other law enforcement agencies can use this API to feed compromised passwords into the Password Pwned database.

Heimdal® Network DNS Security
- No need to deploy it on your endpoints;
- Protects any entry point into the organization, including BYODs;
- Stops even hidden threats using AI and your network traffic log;
- Complete DNS, HTTP and HTTPs protection, HIPS and HIDS;


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










