Contents:
Fake ransomware that acts like a data wiper spreads through malicious adult websites.
The sites deploying the malware are insinuating that they were offering nude photos: nude-girlss.mywire[.]org, sexyphotos.kozow[.]com, and sexy-photo[.]online. Although it is unclear how these sites are promoted.
Malicious websites will automatically encourage the user to download an executable called SexyPhotos.JPG.exe that pretends to be a JPG image. After double-clicking on it in the Download folder, the victim will launch a wiper that will delete almost all the data on the machine.
How the Fake Ransomware Works
Cyble Research and Intelligence Labs (CRIL), who first reported the campaign, discovered that the fake ransomware runs four executables (del.exe, open.exe, windll.exe, and windowss.exe) and one batch file (avtstart.bat) in the user’s%temp% directory.
Persistence is assured by the batch file that copies all the executables to the Windows Startup folder.
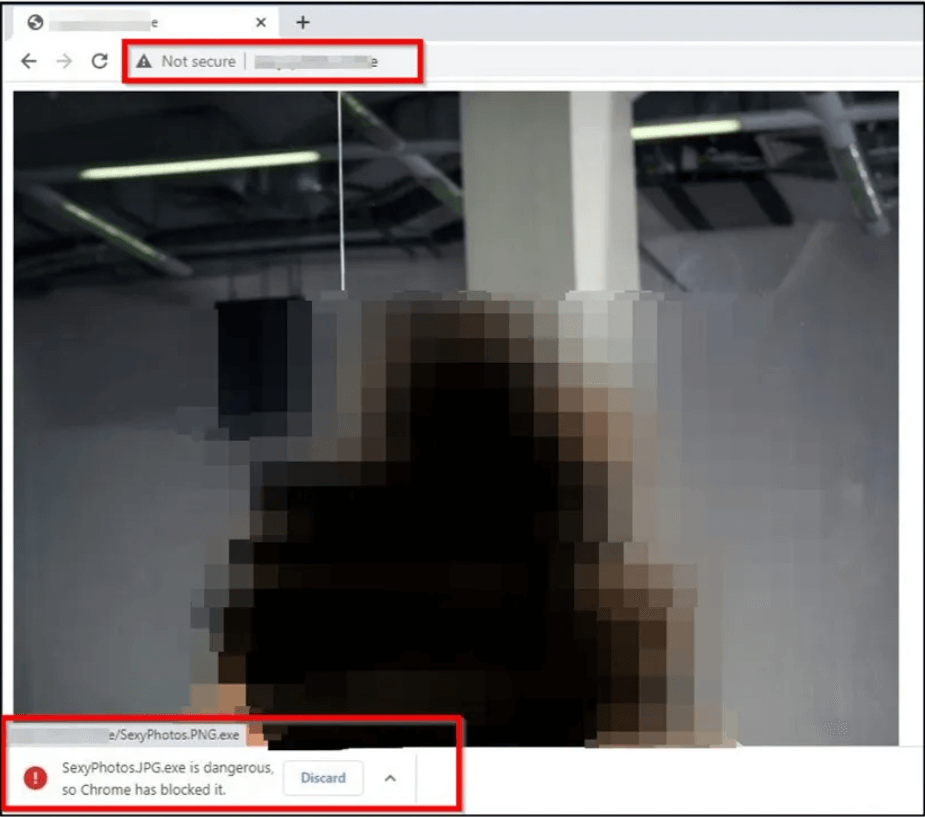
The “windowss.exe” file drops three additional files, among them is “windows.bat” which will rename all files with a generic name like “Lock_6.fille”. The targeted files are not modified or encrypted but the user has no way to know their original names.
The malware uses the following files and folders extensions to perform rename operations:
- File extensions: *.jpg *.bat *.lnk *.vbs *.css *.js *.apk *.GIF *.ico *.log *.py *.sys *.jar *.inf *.bin *.pdf *.JPEG *.png *.dll *.PSD *.BMP *.aac *.amr *.wav *.wave *.ogg *.wma *.3gp *.flv *.mkv *.mp4 *.mpeg *.mkw *.wmv *.7z *.bin *.gzip *.gz *.jar *.xar *.msi *.zip *.doc *.rar *.docm *.docx *.dotx *.epub *.pdf *.avi *.mht *.htm *.iso *.key *.pak *.svg *.csv *.tgz *.torrent *.xlsx *.xls *.php *.html *.HTML *.xml *aac *.mpeg *.flv *.mp3 *.mp4 *.exe
- Folder paths: C:\Users\Windows\Desktop\ C:\Users\Windows\Downloads\ C:\Users\Windows\Music\ C:\Users\Windows\Pictures\ C:\Users\Public\Documents\ C:\Users\Windows\Videos\ C:\users\%username%\downloads\ C:\Users\%username%\Documents\ C:\Users\%username%\Desktop\ C:\Users\%username%\Music\ C:\Users\%username%\Videos\ C:\Users\%username%\Pictures\ C:\DRIVERS C:\Games C:\NVIDIA
At this phase a ransomware note is discarded demanding payment so the data will not be destroyed.
The ransom notes are dropped by “windll.exe” in various locations under the name “Readme.txt.”
The note demands a payment of $300 in Bitcoin in three days, threatening to double it to $600 for an extended deadline of seven days, after which all files will be permanently deleted on the attacker’s server.
But the fake ransomware did not steal data and most probably there is no recovery tool to be exchanged for the money. The fake encryption seems to be only a distraction while the malware deletes data.
How to Mitigate the Fake Ransomware
The fake ransomware does not delete shadow copies, so one way to deal with it, once infected, is to restore your OS to a previous state.
Depending on the date of the last restore point, this could still result in data loss.
Overall, regular backups of your most sensitive files would be the best practice, as reinstalling your operating system should be the swiftest way out of this mess.
For extra safety keep your backup offline or in a separate network so it could not be corrupted in case of an attack.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, YouTube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security







