Contents:
Up to 300 WordPress websites have been targeted by a number of fake ransomware attacks starting Friday last week. It was noticed that they have been displaying false encryption notices with the goal to determine website owners to pay a ransom of 0.1 bitcoin for recovery. A countdown timer was also introduced in this process for urgency sense purposes.
WordPress Sites, the Targets of Fake Ransomware Attacks: Details
Experts from Sucuri discovered this wave of attacks and they wrote a report about this on the 15th of November. One of the attack victims contacted them to ask for support on incident response.
According to the researchers’ report, the website encryption was actually just an illusion to make victims fall into the trap. Here are some details from the report:
- The hackers targeted an installed WordPress plugin and altered it in order to make it show a ransom note, as well as a countdown.
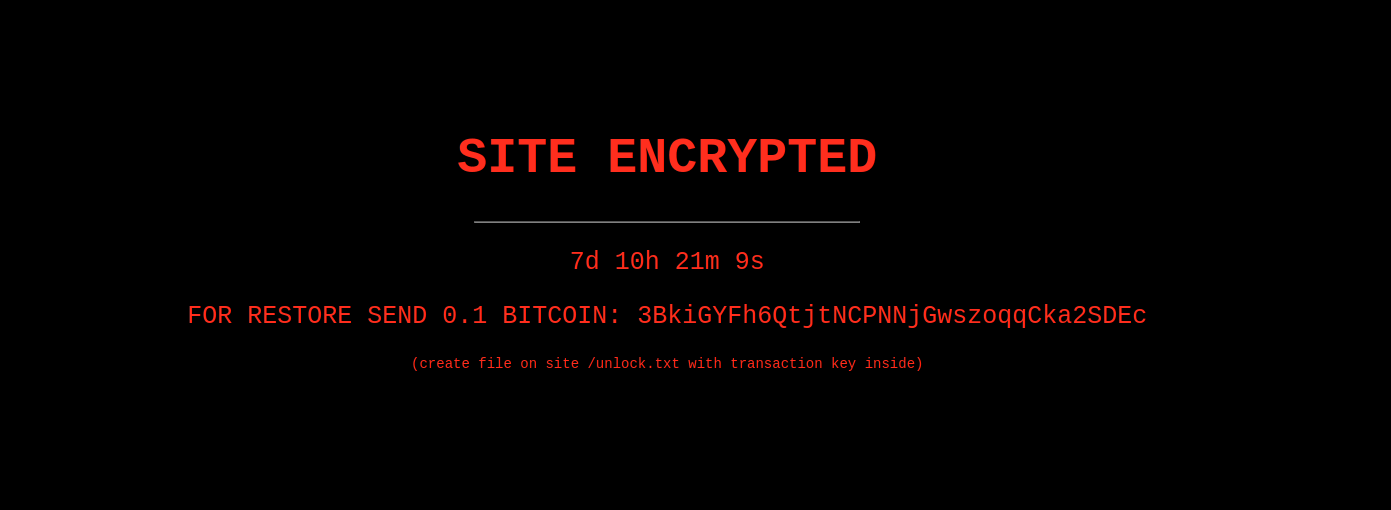
- The plugin would also change the posts’ status by modifying them and setting their ‘post_status’ to ‘null, this action would determine to show their state as unpublished.
- Directorist was the plugin noticed by the experts, Directorist being basically a tool used on websites for online business directory listings creation purposes.

- This method made it look like the website was encrypted.
- This could be resolved with the plugin removal, as the website got its usual status back after plugin removal, and a command to publish again pages and posts had been enforced.
Researchers dived deep into the network traffic logs analysis and found out that the wp-admin panel was the first place where the hackers’ IP address could be noticed. This fact only indicates that threat actors logged to the website as administrators. How? There might have been 2 possibilities: either they performed brute force attacks to discover the password or they obtained the credentials from the dark web market.
According to the same researchers, 291 compromised websites were identified.
Mitigation Measures
The experts under discussion also provided some mitigation measures suggestions in their report.
So after, the plugin is removed and the website content restored, the next steps would be to perform an assessment on what websites admin users exist, then perform a bogus accounts removal. Next, all admin passwords should be changed. The wp-admin administrator page securing is also a practice that needs to be implemented. Access point passwords for example for FTP or database should be also modified.
Do not forget about firewall and backup implementation.
How Can Heimdal™ Help?
To prevent a real ransomware attack you need to have the best tools at your disposal. Meaning that a Ransomware Encryption Protection tool can help you with this. What does this tool do? Being compatible with any antivirus, it keeps malicious encryptions away and protects you from being a victim of data loss and data exfiltration.
Combine it with our powerful and awarded traffic filtering, Threat Prevention, to prevent with a 96% accuracy future threats that might occur at the domain level.
Did you enjoy this article? Follow us on LinkedIn, Twitter, Facebook, Youtube, or Instagram to keep up to date with everything we post!


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










