Contents:
The hacker group going by the name of Everest claims to have hacked South Africa state-owned company ESKOM Hld SOC Ltd.
ESKOM describes its activity as transforming inputs from the natural environment – coal, nuclear, fuel, diesel, water, and wind – into more than 90% of the energy supplied to a wide range of customers in South Africa and the Southern African Development Community (SADC) region. Because of the company`s strategic importance, threat actors seem to have taken an interest and are now demanding a 200,000 $ in exchange for the data they claim to have stolen.
Another Attempt
Previously, in March 2022, the same ransomware operators published a notice announcing the sale of “South Africa Electricity company’s root access” for $125,000.
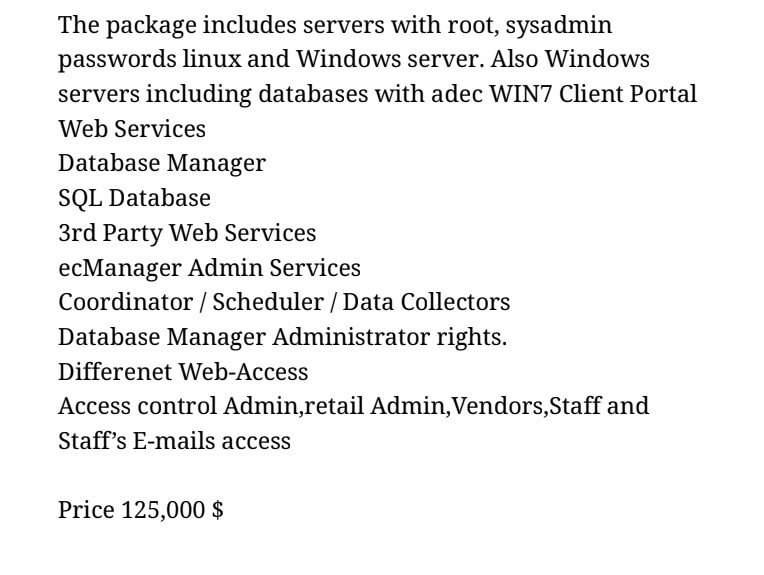
However, in a Twitter post, the company denied having suffered a security breach.
Whilst Eskom combats regular attempted attacks there is no evidence that we have suffered a ransomware attack. We have an information & cybersecurity team/tools that assist with combatting attempted attacks.
Last week, as ESKOM security experts were reporting some server issues, the Everest ransomware gang posted again about hacking the South African company. They claim to have gained access to all servers of the company, as well as root access to many of them.
The message posted by the Everest gang on their Tor leak site also promises “trust access of a well-known defense company from USA, which is a partner of this Electric Company.”
This time around, the requested price for the complete package of stolen data is $200,000. According to Security Affairs, the gang accepts both Bitcoin and Monero cryptocurrencies as forms of payment.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, YouTube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security









