Contents:
The LockBit ransomware group has declared that it was behind the American software company Entrust incident that occurred in June.
At the beginning of June, the tech giant started informing its clients that it had been the victim of a cyberattack, during which sensitive data was taken from internal systems.
Here’s the message customers received from Entrust:
We have determined that some files were taken from our internal systems. As we continue to investigate the issue, we will contact you directly if we learn information that we believe would affect the security of the products and services we provide to your organization.
Entrust stated that they were looking into the incident but would not provide any information about the attack or clarify whether it was ransomware or not.
While our investigation is ongoing, we have found no indication to date that the issue has affected the operation or security of our products and services, which are run in separate, air-gapped environments from our internal systems and are fully operational.
Nevertheless, at the time, BleepingComputer was informed by AdvIntel CEO Vitali Kremez that a notorious ransomware organization had hit Entrust after acquiring access to the company network via “network access sellers.”
Entrust Allegedly a Victim of LockBit Ransomware Gang
As per BleepingComputer, LockBit had set up a customized data leak page for Entrust on their site, announcing that they would expose all of the stolen data tonight.
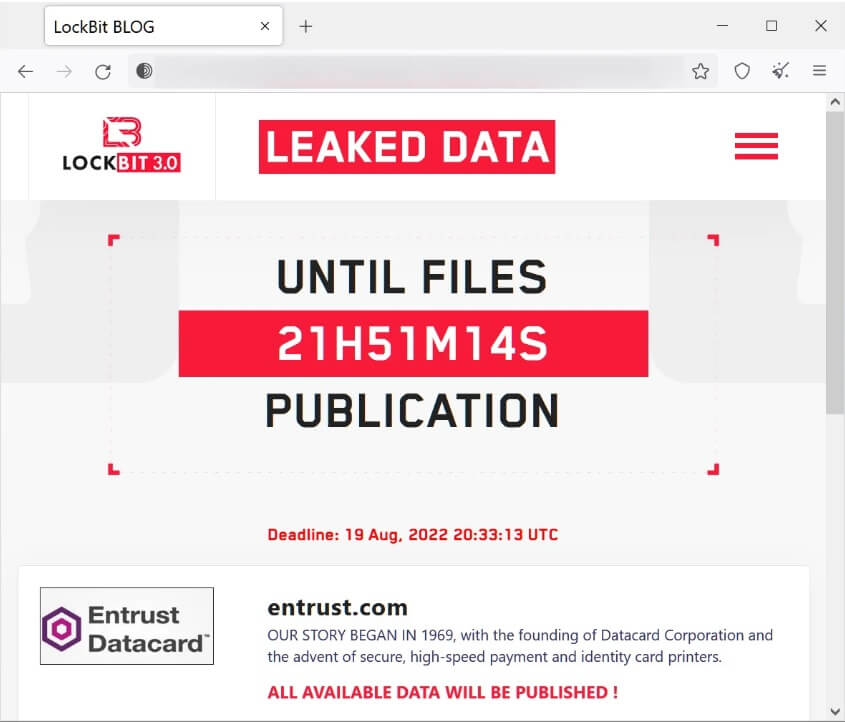
The purpose of ransomware gangs posting stolen information on their data leak sites is typically to intimidate the victim into starting the negotiations again.
Because the ransomware gang threatens to make all the data public, we can only guess that Entrust refused to negotiate with the threat actors or declined to pay the requested ransom.
More on LockBit Ransomware
LockBit ransomware, one of the most dangerous organizations at this time, started operating back in September 2019. The group works as a ransomware-as-a-service (RaaS) by recruiting threat actors to breach networks and encrypt devices.
Since it was launched, LockBit has been extremely active, as the gang representatives were promoting the RaaS and providing support on various Russian-language hacking forums.
LockBit launched the LockBit 2.0 RaaS back in June 2021, and 3.0 in June 2022. The new version includes new encryptors built on the BlackMatter source code, new payment methods, new extortion tactics, and the first ransomware bug bounty program.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








