Contents:
A surge of malspam campaigns has been recently attributed to Emotet botnet. Taking advantage of password-protected archive files, the notorious trojan drops CoinMiner and Quasar RAT on the systems it takes over.
In an attack chain detected by Trustwave SpiderLabs researchers, an invoice-themed ZIP file lure was found to contain a nested self-extracting (SFX) archive, with the first archive having the purpose to launch the second.
Deeper Dive
Emotet is known to primarily spread through malspam and, while phishing attacks usually rely on persuasion techniques in order to trick the victims into opening the attachment, this time researchers claim the campaign bypassed this by making use of a batch file to automatically supply the password to unlock the payload. The first archive is a RARsfx, only meant to execute a second RARsfx contained within itself. The second archive is password-protected but no user input is necessary to extract and execute its content.
The self-extracting archive has been around for a long time and eases file distribution among end users. However, it poses a security risk since the file contents are not easily verifiable, and it can run commands and executables silently.
Once inside, the infection proceeds with the execution of CoinMiner, a cryptocurrency miner that can also double up as a credential stealer, or Quasar RAT, an open-source remote access trojan, depending on the payload packed in the archive.
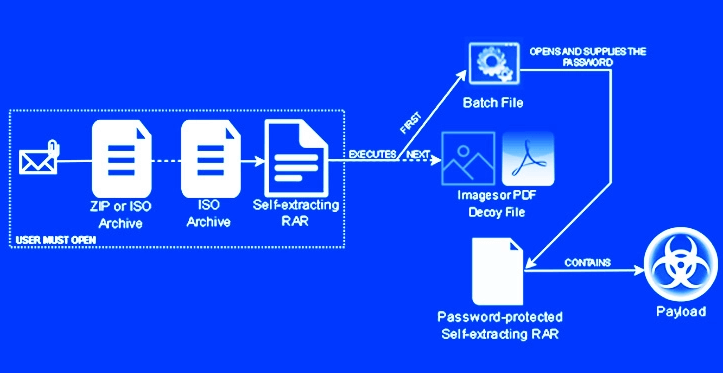
This attack technique enables threat actors to bypass the password barrier, making it easier for them to carry out attacks such as cryptojacking, data exfiltration, and even ransomware.
Trustwave researchers claim there has been a noticeable increase in threats packaged in password-protected archives, 96% of them being spammed by the Emotet botnet.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security







