Contents:
JPCERT/CC, Japan’s first CSIRT (Computer Security Incident Response Team), has released a new version of their open-source tool EmoCheck to identify new 64-bit variants of the Emotet malware, which started infecting users earlier this month.
Emotet belongs to the malware strain known as banking Trojans. It primarily spreads through malspam, which are spam emails that contain malware (hence the term). These messages often contain familiar branding, mimicking the email format of well-known and trusted companies such as PayPal or DHL to convince users.
Through this medium, the infection may be delivered in several ways:
- malicious scripts,
- phishing links,
- or macro-enabled document files.
Once a device has been compromised, Emotet will steal users’ emails in order to use them in potential reply-chain phishing attacks, as well as download additional malware payloads on the machine.
Because further malware infections frequently result in data theft and ransomware attacks, it’s critical to discover the Emotet malware as soon as possible.
EmoCheck 2.2 Now Detects 64-bit Versions of Emotet Malware
In 2020, Japan Computer Emergency Response Team Coordination Center (CERT/CC) released a free system utility program called EmoCheck that enables users to check their computers for any signs of the Emotet malware. If one is found, the full path to the malware infection will be displayed so that it can be removed.
Nevertheless, the Emotet group shifted to 64-bit versions of their loader and stealers earlier this month, rendering existing detections obsolete. Furthermore, the EmoCheck utility was not able to detect the new 64-bit Emotet versions after this switch anymore.
JPCERT has recently launched EmoCheck 2.2, which now supports and identifies the new 64-bit versions.
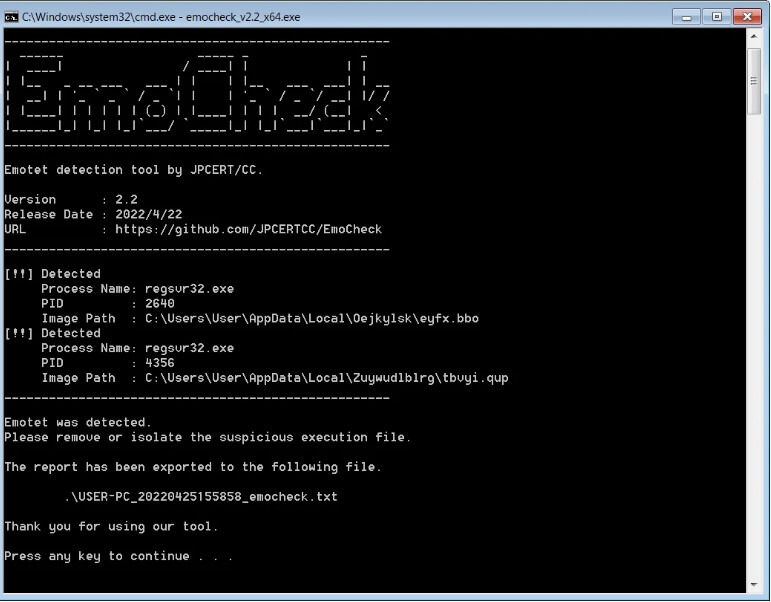
You can use the EmoCheck tool from Japan CERT’s GitHub repository to see if Emotet malware compromised your computer. After downloading, double-click emocheck x64.exe (64-bit version) or emocheck x86.exe (32-bit version), depending on which version you downloaded.
EmoCheck will proceed to look for the malware and, if Emotet Trojan is found, will show the process ID it is operating under as well as the malware DLL’s location.
At the moment, the trojan is being installed in a random folder under C:Users[username]AppDataLocal.While Emotet is a DLL, it will not have the DLL extension but rather a random three-letter extension, like .bbo or .qvp.
If EmoCheck detects an infection, immediately open Task Manager and kill the listed process, which is usually regsvr32.exe.
Following this action, use a reputable antivirus solution to scan your PC to make sure other malware has not already been installed.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










