Contents:
The rebranding to Grief ransomware comes following a period of little to no activity and it is still unclear if any of the original developers are still behind this ransomware-as-a-service (RaaS) operation.
The DoppelPaymer ransomware activity started to decline in mid-May, about a week after DarkSide ransomware’s attack on Colonial Pipeline.
When no updates were seen it seemed like DoppelPaymer was taking a step back, but recently security researchers pointed out that Grief and DoppelPaymer were names for the same threat.
Fabian Wosar of Emsisoft declared for BleepingComputer that the two ransomware operations are having the same encrypted file format and are using the same distribution channel, the Dridex botnet.
The Dridex malware, and its various iterations, are able to impact the confidentiality of customer data and the availability of data and systems for business processes.
It seems that the original version of Dridex first appeared in 2012 and by 2015 it had become one of the most prevalent financial Trojans.
Threat actors typically distribute the Dridex malware through phishing e-mail spam campaigns, by employing a combination of legitimate business names and domains, professional terminology, and language implying urgency to persuade victims to activate open attachments.
The similarities that Grief has to DoppelPaymer are so striking that a connection between the two is very hard to dismiss.
The researchers from Zscaler analyzed the early Grief ransomware sample discovered in June and observed that the ransom note dropped on infected systems pointed to the DoppelPaymer portal.
This suggests that the malware author may have still been in the process of developing the Grief ransom portal. Ransomware threat groups often rebrand the name of the malware as a diversion.
If the similarities discovered in M.O. of the ransomware operation were not enough to show the connection between the two operations, the connection extends even further, to their leak sites.
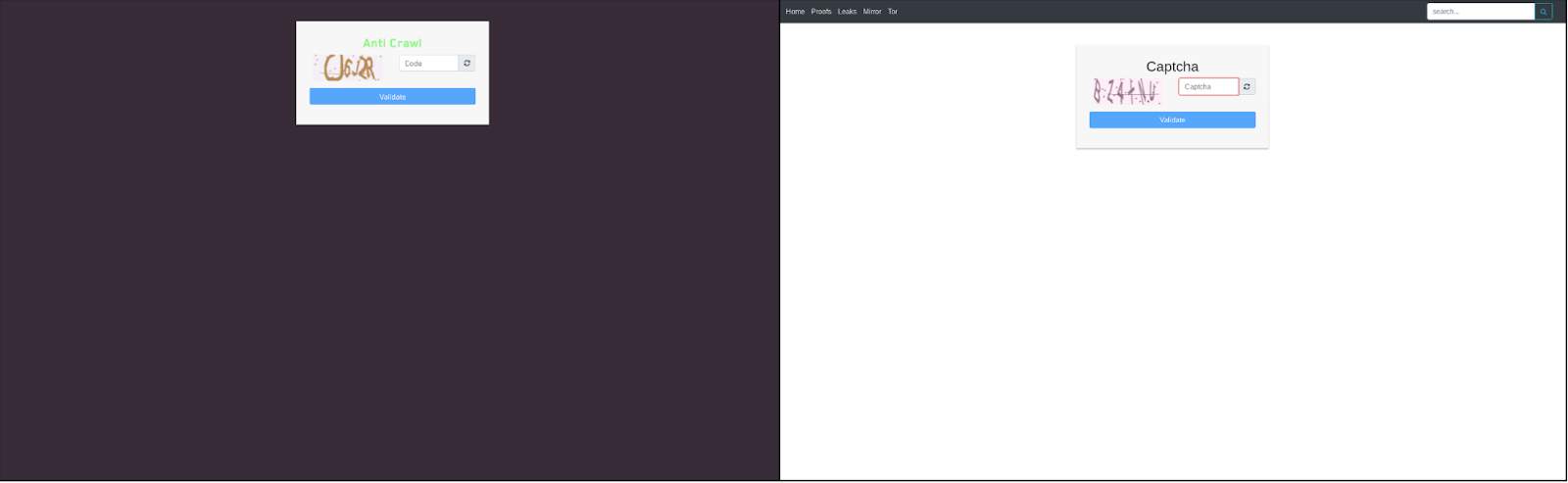
Although visually the two websites are very different, similarities like the captcha code that prevents automated crawling of the site make it look like a DoppelPaymer rebranded website.
Another similar thing that the two ransomware threats have in common is the fact they rely on highly similar code that implements “identical encryption algorithms (2048-bit RSA and 256-bit AES), import hashing, and entry point offset calculation”, and that Grief and DoppelPaymer use the European Union General Data Protection Regulation (GDPR) as a warning that non-paying victims would have to face legal penalties due to the breach.
The Differences Seem to be Mostly Cosmetic
Grief ransomware switched to Monero cryptocurrency and uses the term “griefs” for the victim data leaked on their site either as proof of the compromise (“griefs in progress”) or as punishment for not paying the ransom (“complete griefs”).
Right now there are more than two dozen victims listed on the Grief leak site, this proving that the threat actor has been busy working under the new name, with one of the most recent attacks being the one on the Greek city Thessaloniki.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security