Contents:
Apparently, the LockBit ransomware gang’s new technique of “hiring” employees and other insiders in order to help them breach and encrypt corporate networks more easily has opened a whole new world of opportunities for hackers.
On August 12, 2021, cloud email security platform Abnormal Security noticed certain emails received by their customers where they were being asked to be a part of an insider threat plan.
According to the company, a Nigerian hacker attempted to convince an employee to infect the company’s network with ransomware by offering him $1 million in Bitcoin, or 40% of the presumed $2.5 million ransom.
The cybercriminal sending these emails is allegedly connected to the DemonWare ransomware gang as the employer received the following message:
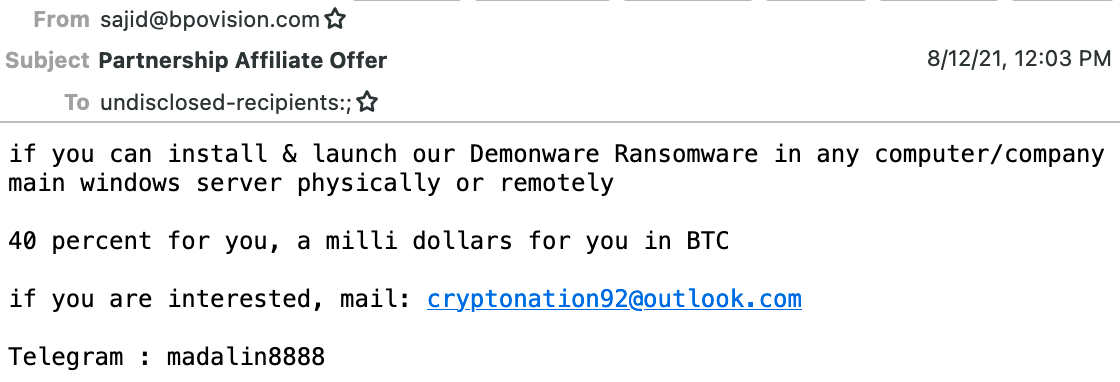
If the employee agrees to deploy the ransomware he can contact the sender via an Outlook email account and a Telegram username.
What is DemonWare?
DemonDemonware or Black Kingdom ransomware strain is the most recent malware caught within networks that is leveraging the Microsoft Exchange vulnerabilities as an initial entry point to push ransomware.
The malware has been around for quite some years and can be found on GitHub for free.
Security Researchers Posing as an Employee to Get Inside the Hacker’s Mind
The researchers have seen a great opportunity to get inside the head of the attacker and better understand the used technique. Because he provided an address where he can be contacted, the Abnormal Security researchers decided to create a fake persona and get in touch with the hacker.
They constructed an employee that wanted to gain some easy money and used the Telegram account to contact the Nigerian man.
The researchers received from the hacker two links for an executable file they could download on WeTransfer or Mega.nz, two file sharing sites.
The file was named “Walletconnect (1).exe” and after a careful investigation, the security specialists could confirm that it was actual ransomware.
Not Every Ransomware Attacker Can Handle a Ransomware Attack
Even though the attacker initially said it would ask for a $2.5 million ransom he quickly changed his mind and told to the “employee” that he hoped to get at least $250,000. After the researchers told him that the fake company’s annual income is $50 million, the actor concluded that he would only ask for $120,000.
The attacker’s behavior showed to the researchers that he had no idea what he’s doing.
When asked if he is the creator of the ransomware, the man said that he “programmed the software using python language” but as we already said, DemonWare is available for free on GitHub. In reality, all the hacker had to do is to get the ransomware and convince someone to do the ”dirty work” of deploying it.
Who Orchestrated the Plan?
The man behind this ransomware attack failed attempt confirmed that he is from Nigeria. He also told the researchers that he is the next Mark Zuckerberg as he currently tries to create an African social networking platform called Sociogram. He even shared a link to his LinkedIn profile that exposed his full name.
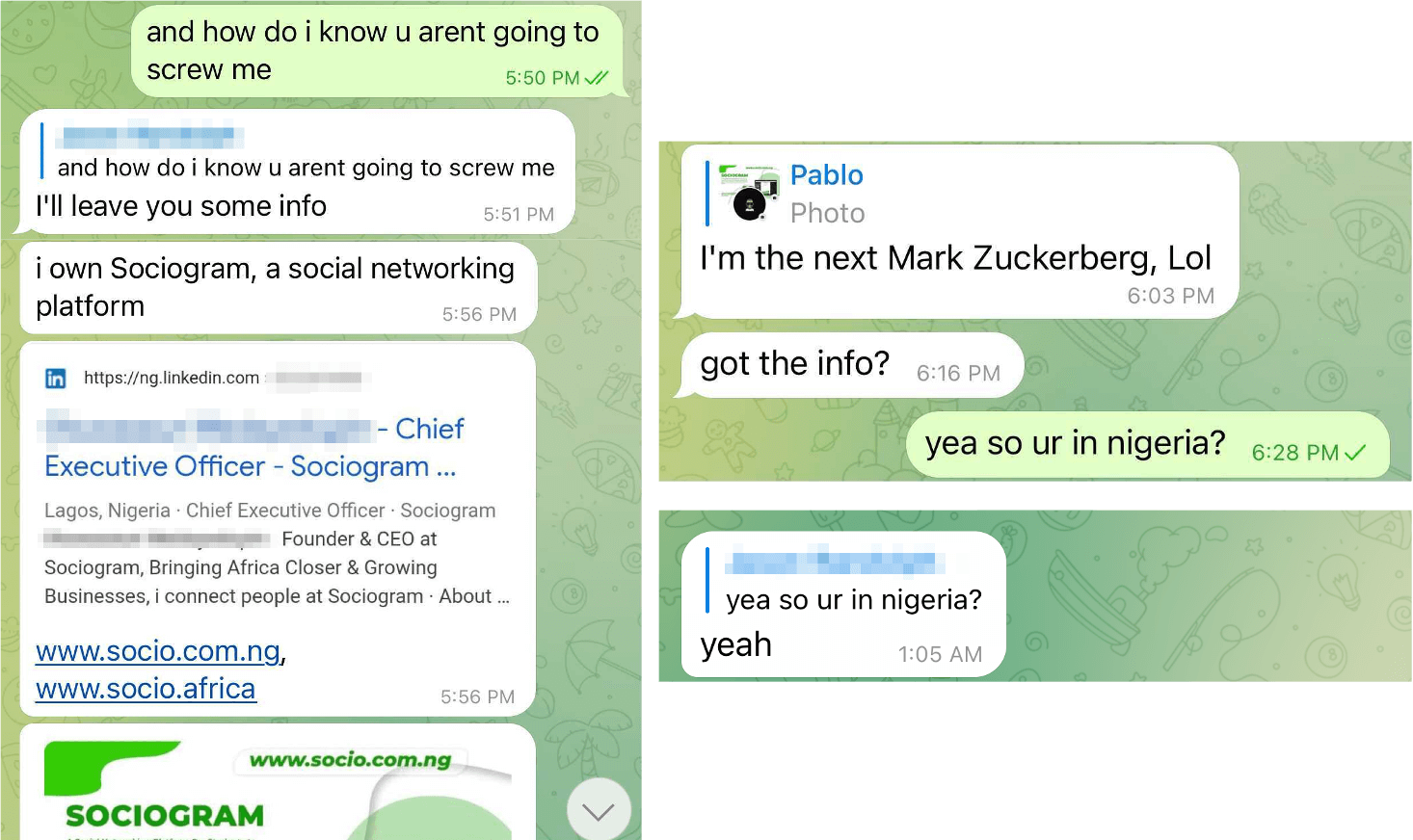
Knowing the actor is Nigerian really brings the entire story full circle and provides some notable context to the tactics used in the initial email we identified. For decades, West African scammers, primarily located in Nigeria, have perfected the use of social engineering in cybercrime activity.
While the most common cyberattack we see from Nigerian actors (and most damaging attack globally) is business email compromise (BEC), it makes sense that a Nigerian actor would fall back on using similar social engineering techniques, even when attempting to successfully deploy a more technically sophisticated attack like ransomware.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










