Contents:
Marketo data theft marketplace is pressuring its victims by using specific extorsion tactics as emailing the competitors and offering sample packs of the stolen data.
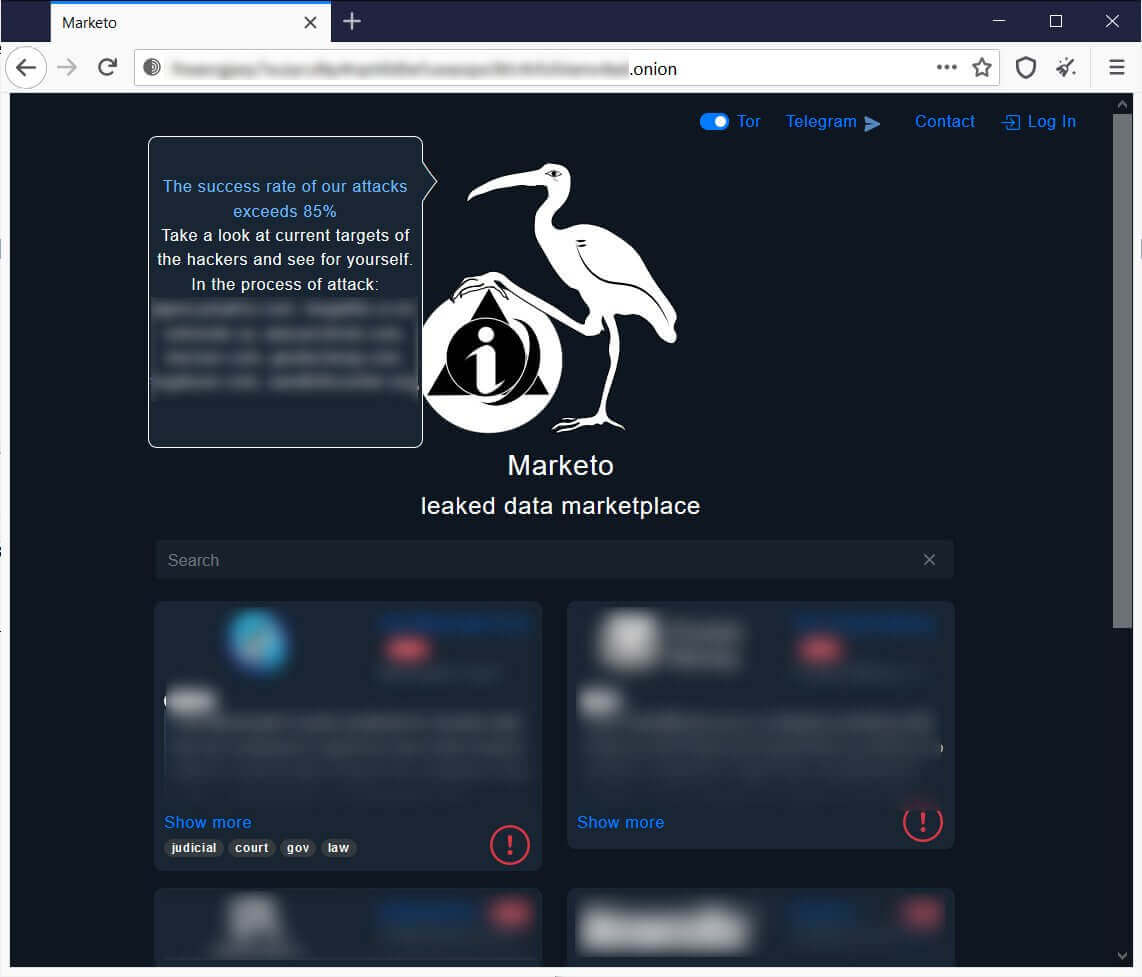
It looks like the cybercriminals have started to create dedicated data-theft extortion marketplaces that exist solely to sell stolen data, with the data sold on these sites being obtained through the marketplace’s own attacks, from other threat actors, or even by collecting data released in other attacks, such as ransomware or website data breaches.
The data that gets stolen is then sold for as low as $100 to tens of thousands of dollars depending on the marketplace.
Marketo is one of these marketplaces and is taking this tactic a step further and is emailing the victims’ competitors in an attempt to offer samples of the stolen data and entice them into purchasing it.
Back in April Marketo data theft marketplace claimed that they’ve breached a large, heavy machinery and defense technology company with the purpose of selling their stolen data.
The latest developments in the situation can make us assume that they could not find any buyers as Marketo proceeded to send emails to communication managers for the victims’ competitors in order to offer a “demo pack” of the stolen data.
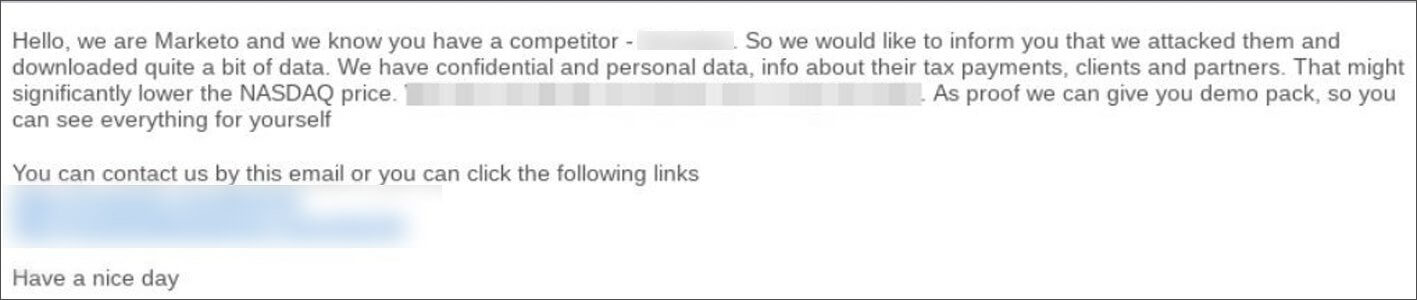
Hello, we are Marketo and we know you have a competitor – [redacted]. So we would like to inform you that we attacked them and downloaded quite a bit of data.
We have confidential and personal data, info about their tax payments, clients, and partners. That might significantly lower the NASDAQ price.
At this time it remains unclear if the Marketo data theft marketplace was hoping that the competitors would purchase the data for the reason to learn corporate secrets or to pay to damage the reputation of their competitors.
Multi-national billion-dollar companies whose names would be immediately recognizable to everyone are present on the list of competitors that received this email.
This type of extorsion tactic is not new with the victims’ competitors being pressured to make a ransom payment or even encourage other companies to purchase the stolen data.
This is happening after the Clop ransomware gang’s hacking spree that targeted Accellion FTA secure file transfer devices to steal their hosted data, also used a similar tactic as Marketo, and after not being the malicious actors started to email the competitors and journalists with information about the attacks in order to pressure the victim.
It seems like the attackers are becoming more creative with the way in which they are trying to extort their victims, therefore a good ransomware encryption product can be what your company needs in order to remain safe.

Heimdal™ Ransomware Encryption Protection
- Blocks any unauthorized encryption attempts;
- Detects ransomware regardless of signature;
- Universal compatibility with any cybersecurity solution;
- Full audit trail with stunning graphics;
The Ransomware Encryption Protection offered by Heimdal™ is a revolutionary 100% signature-free component, that is ensuring market-leading detection and remediation of any type of ransomware, whether fileless or file-based, as it’s able to detect any encryption attempts without signatures or behavioral patterns and was engineered to be universally compatible with any antivirus.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










