Contents:
Exmatter, a well-known data exfiltration malware used by the BlackMatter ransomware group, has been spotted operating a new tactic.
The malware was upgraded with data corruption functionality which might show a switch in the field of ransomware attacks with hackers preferring deserting the encryption tactic.
How Data Corruption Works
The new data corruption tactic was identified in a new BlackCat ransomware attack and analyzed by the Cyderes Special Operations team and the Stairwell Threat Research team.
Exmatter malware was initially designed to extract files from the victim’s device and upload them to the attacker’s server before the ransomware was executed. But this time the malware corrupted the files on the compromised system.
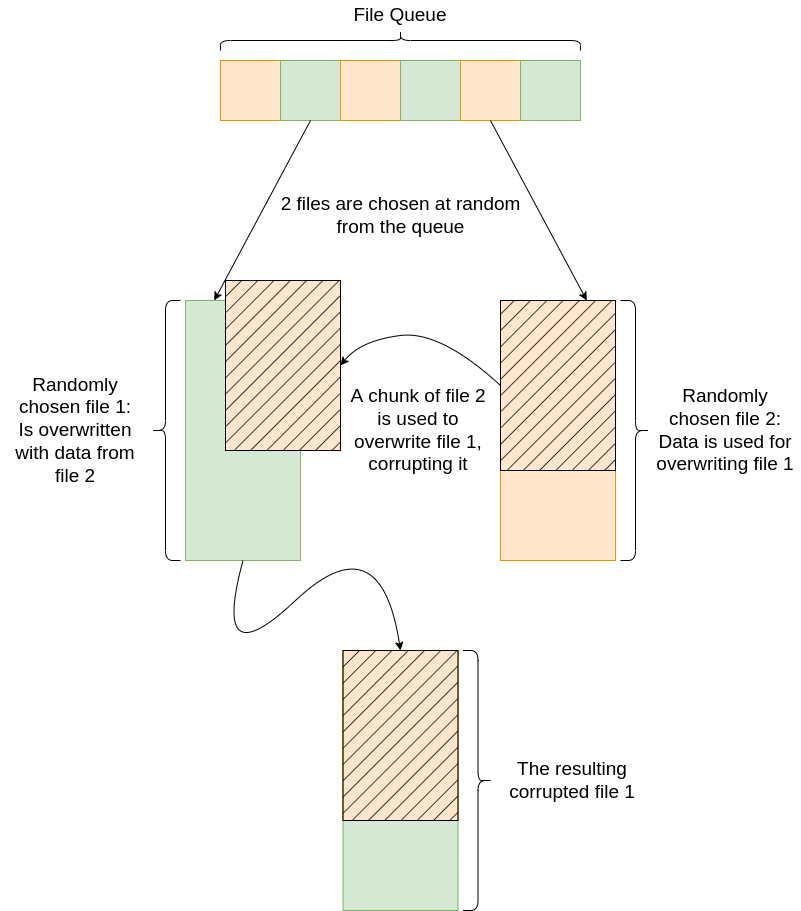
“First, the malware iterates over the drives of the victim machine, generating a queue of files that match a hardcoded list of designated extensions. Files matching those file extensions are added to the queue for exfiltration, which is then written to a folder with the same name as the victim machine’s hostname on the actor-controlled server.
As files upload to the actor-controlled server, the files that have been successfully copied to the remote server are queued to be processed by a class named Eraser. A randomly sized segment starting at the beginning of the second file is read into a buffer and then written into the beginning of the first file, overwriting it and corrupting the file.”
This version of Exmatter seems to be still developing giving to several reasons, as Stairwell shows:
- The chunk size of the second file is determined random and can be only one byte long. This file is being used to overwrite the first.
- Because files can’t be removed from the corruption queue, some files may be overwritten multiple times, while others may never have been chosen.
- The Erase function does not seem to be fully implemented and does not decompile properly.
Why This Change
There are some speculations about this shift in ransomware tactics.
Data corruption may help cyber criminals avoid security software. Heuristic-based detection for ransomware and wipers may be bypassed using data from the victim’s device – legitimate data – to corrupt other files.
But it may also be a strategy chosen by ransomware affiliates. With the new data corruption feature, affiliates don’t need an encryptor developer anymore to run an attack. They can steal and delete or corrupt data on their own and keep all the revenues gathered from the ransom.
“Many ransomware operations run as a Ransomware-as-a-Service, where operators/developers are in charge of developing the ransomware, payment site, and handling negotiations, while affiliates join to breach corporate networks, steal data, delete backups, and encrypt devices.
As part of this arrangement, the ransomware operators receive between 15-30% of any ransom payment, and the affiliates receive the rest”, according to BleepingComputer.
Besides, in the past, there have been ransomware attacks with bugs in the encryption code that enabled the victims to recover the data and made affiliates lose any potential payment.
Data corruption will function also as an additional pressure point for the target and will make the whole ransomware attack timeline faster as the encryption step is eliminated.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security









