Contents:
D-Link leading global networking equipment company admitted suffering a data breach. Threat actors gained access to the company`s system after an employee clicked on a phishing link.
The company discovered the data breach after the threat actors posted about it on a malicious forum. They immediately started an investigation and took additional security measures to contain the attack.
For the moment, the impact of the data breach remains unclear. While hackers claimed to steal source code from D-View software and customers and staff data, the company denied their allegation.
What is the real impact of the D-Link data breach?
On October 1st, threat actors posted online that they had breached D-Link`s internal network and gained access to “3 million lines of customer information” and “source code to D-View”.
Allegedly, the customer data included names, emails, addresses, phone numbers, company names, and more. Also, the message stated the database included information belonging to government officials in Taiwan and D-Link’s CEO and employees.
Threat actors only asked $500 for the whole stolen data package.
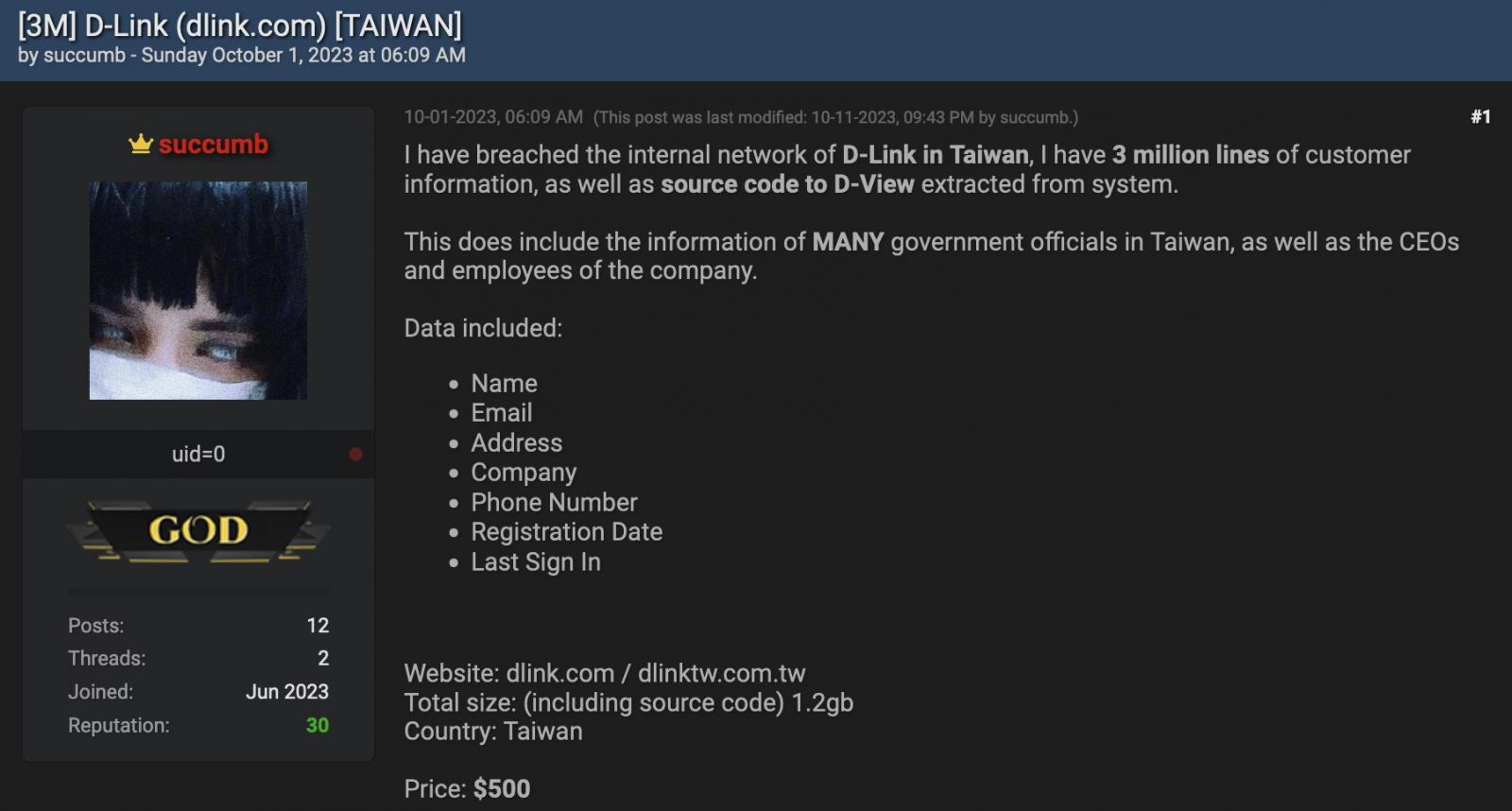
Image Source Bleeping Computer
D-Link denies the magnitude of the impact and says the breach only affected a D-View 6 system, which had been EOD since 2015. According to the networking equipment company hackers only got access to 700 old records, not millions as claimed.
Based on the investigations, however, it only contained approximately 700 outdated and fragmented records that had been inactive for at least seven years.
These records originated from a product registration system that reached its end of life in 2015. Furthermore, the majority of the data consisted of low-sensitivity and semi-public information.
Phishing vs outdated software. What caused the D-Link data breach?
D-Link said the attackers gained access to the company`s network after an employee clicked a phishing link by mistake. The intruder was then able to access a product registration system within an old “test lab environment”. The server was running on an outdated D-View 6 system that was End-of-Life (EOL) since 2015. So, D-Link`s system included an EOL server that remained exposed to Internet access for seven years.
For the moment, D-Link didn`t explain why they kept the outdated server operating.
Old equipment that runs on outdated software poses serious security risks. Since the software is not supported anymore, the newly discovered vulnerabilities remain unpatched. Thus, hackers can easily use them as an open gate to enter a company`s network. Removing all EOL devices and software is one of the best practices for network security.
The D-Link data breach is a reminder that keeping outdated endpoints online and running can jeopardize the whole system.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and Youtube, for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security







