Contents:
This piece is authored by Michael Coffer, Heimdal’s resident sales expert for the education sector. Michael speaks to hundreds of IT admins a year, so there are few people who understand the challenges of this sector better than him. Here, he explains why Cyber Essentials alone isn’t enough to keep you safe – and how to achieve a genuinely proactive cybersecurity approach with Heimdal.
As an IT admin in education, there’s a lot on your to-do list.
Sometimes, it can feel like a mad rush just to sort out the most urgent issues and requirements, giving you precious little time to think proactively. And when it comes to cybersecurity, staying compliant with frameworks like Cyber Essentials can easily just become another job-to-be-done on an ever-growing list.
As a sales representative in the education space, I recognize this picture as an increasingly common backdrop for school IT teams. Often, simply understanding what you need to do is a task in itself.
But here’s the challenge: Even being compliant with Cyber Essentials isn’t enough to guarantee safety. By definition, it’s a baseline, not a comprehensive strategy. But if staying compliant is difficult enough, it’s easy to think that going beyond that simply isn’t an option.
In truth, it is possible to create a cybersecurity approach that’s both compliant and effective. Here, I explain how.
Cyber Essentials basics: Understanding your cyber compliance requirements
Read more: What Is Cyber Essentials and How Can Heimdal Help Your Organization Achieve CE Compliance?
Cyber Essentials is a government-backed cyber initiative that aims to create a baseline of effective cybersecurity defense. For colleges and specialist post-16 institutions (SPIs), certification is compulsory if you want to receive central government funding. While it’s not yet mandatory for secondary and primary schools, many IT admins think it’s only a matter of time before it is.
The requirements for Cyber Essentials fall into five main categories: Firewalls, malware protection, patch management, secure configuration, and user access control.
Realistically, schools, trusts, and education institutions will need more than just these five categories if they want to ensure a modern, layered defense. But ultimately, that conversation can’t start until you’ve fulfilled your cyber security compliance objectives. Here, we recap what the main requirements are and how Heimdal helps you meet them.
Firewall compliance
The first requirement is to ensure that a firewall is active between your own internal network and the wider internet. This creates a physical barrier which filters out incoming traffic to your router.
At the very least, this should block unauthenticated inbound connections by default. You should also have firewalls that can separate guest Wi-Fi networks from the internal network. Additionally, inbound ports must be closed by default and all firewalls must be properly configured and regularly maintained.
Read more: https://cyberessentials.online/cyber-essentials-firewalls-explained/
Malware protection compliance
Cyber Essentials requires you to have a malware protection system, with options including anti-malware software, application whitelisting, or application sandboxing.
Generally, installing anti-malware software is the easiest way to achieve these requirements, since it can be added to your existing IT environment, rather than requiring more fundamental changes to the network. This option also generally has a lower impact on the user experience, meaning fewer incoming support tickets from teachers and students who can’t access the files and apps they need.
Read more: https://cyberessentials.online/cyber-essentials-malware-explained/
Patch management compliance
Patches and updates must be installed promptly and regularly across hardware, operating systems, and software. This applies to all devices a school may use, including end-user devices (computers, laptops, smartphones, tablets), and network endpoints (firewalls, routers, servers).
Specifically, Cyber Essentials requires all critical or high severity patches to be installed within 14 days of release. It also suggests that updates should be installed automatically wherever possible.
Read more: https://cyberessentials.online/cyber-essentials-patch-management-explained/
Secure configuration compliance
This category involves a series of best practices and policies to ensure apps and systems are properly configured.
The goal is to create as small an attack surface as possible – which is particularly important for the complex and sprawling IT networks that most modern schools have. Therefore, it’s important to regularly disable all unnecessary user accounts and software, to reduce unnecessary attack vectors.
At the same time, Cyber Essentials includes several requirements around password security. These include having policies to regularly rotate passwords and change all default passwords, as well as rules governing password strength.
User access control compliance
The final requirement is to ensure a robust approach to identifying users and granting access. All individuals and accounts should be authenticated and the IT team must have control over the permissions available to each user. Where possible, you should use multi-factor authentication to secure user accounts.
It’s also important to ensure that admin privileges are only available from specific accounts, and that access to these is only given to those who absolutely need them. You should also proactively remove unnecessary accounts and privileges when they become disused or redundant.
Read more: https://cyberessentials.online/cyber-essentials-access-control-explained/
Beyond cyber compliance: How to take cybersecurity to the next level
On their own, the techniques we discussed in the last section aren’t enough to guarantee safety.
That’s because the most effective policy is to use a layered approach, combining both proactive and reactive tools to detect and repel hackers at every stage of their attack. To use malware as an example, this would involve both detecting the presence of malware as well as trying to stop it being installed in the first place.
Cyber Essentials requires several useful tools that play a crucial role in this layered approach. But there are several key gaps – and the focus is generally more on reactive than proactive tools.
For that reason, there are several additional tools and policies that you should also consider. While these aren’t compulsory, they can make a huge difference to the strength of your security posture, while significantly reducing the amount of manual work for the IT team.
1. Protect your environment 24/7
The worst nightmare for any school IT admin is waking up to discover a significant incident has occurred overnight and it’s too late to respond. But almost no educational institution has the resources for a 24/7 support team.
Of course, you can install threat detection tools and create automated response policies. But by far the best approach is to have a team of trained security experts on hand to deal with critical issues in realtime. The only way to do this is to use a managed security services provider.
Read more: What Are Managed Security Services: Benefits and Solutions
How Heimdal’s MXDR keeps you safe
At Heimdal, we offer an additional managed service to all customers, regardless of the technology being used. Unlike most enterprise-grade security providers, all this support is provided in-house, meaning we can guarantee a better quality of service than most providers. In fact, we respond to all requests in an average of 11 minutes.
2. An extra layer of network defense
The Education Alliance decided that Heimdal was the perfect fit for our organization. Having multiple products within the suite meant it was scalable and easy to add additional schools onto the system.
If you’re looking for an antivirus product nowadays, it’s not just about the AV engine: It’s about the wraparound of third-party patching, updates, and isolating devices when a threat appears. For me, Heimdal ticks all those boxes.
– Matt Wadsworth, Director of IT, The Education Alliance
Under Cyber Essentials, the minimum requirement around network security is to have a firewall governing all access to your network. This is obviously an important start, but it shouldn’t be the only tool in your arsenal, because traditional firewalls are only capable of filtering out known and recognizable threats.
Therefore, the most modern DNS filtering tools add another layer of defense to this: Behavioral analysis. This involves analyzing all user activity across an IT environment, using machine learning to detect particularly suspicious behavior. This can help to filter out malicious connections that would otherwise pass undetected through the firewall.
Read more: Why DNS Security Is Important: 3 Real-life Use Cases
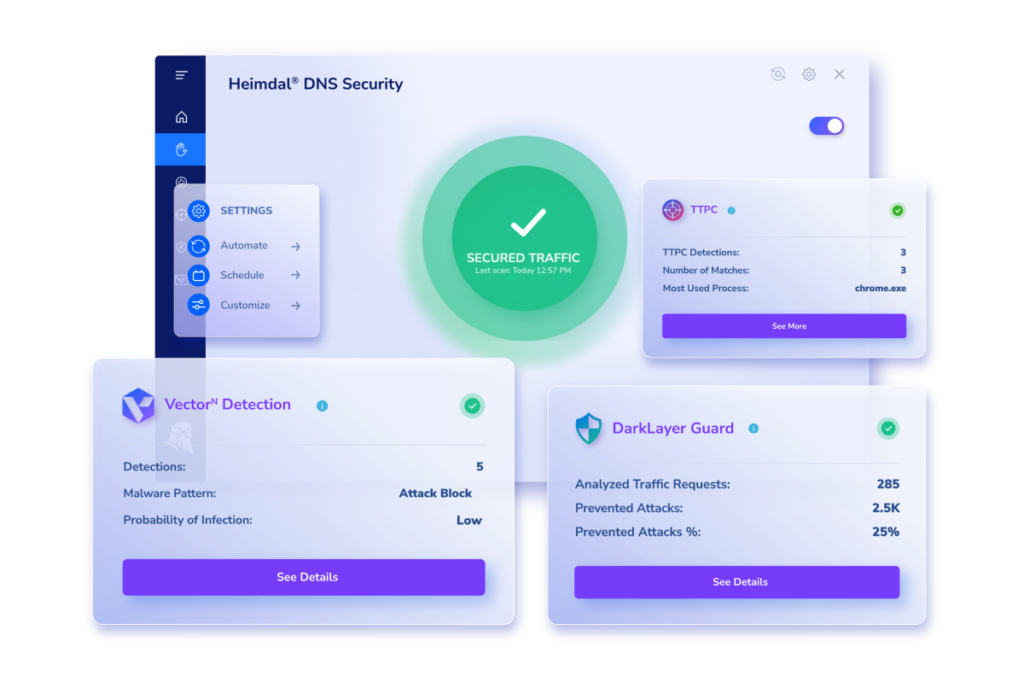
How Heimdal’s DNS Security module keeps you safe
At Heimdal, we’ve been a market leader in the DNS security space for several years now. We offer a mixture of traditional DNS filtering, AI-powered behavioral analysis, and customizable policies that help you build bespoke responses to common threats.
3. Patch management: Automation that puts you in control
Patch management is a non-negotiable requirement of a Cyber Essentials certification. But installing patches manually can be tedious, time-consuming, and ineffective. Therefore, many IT admins prefer to automate this to save time and ensure patches are reliably installed.
But at the same time, there are good reasons not to patch everything immediately: Updates can cause disruption, bugs, and downtime – so it’s often wiser to install them overnight. At the same time, lower-risk updates can be grouped together for scheduled maintenance periods. To get the best of both worlds, you need a tool that puts you in the driver’s seat, while still enabling automation.
Read more: How Do Hackers Exploit Your Vulnerabilities?
How Heimdal’s Patch & Asset Management keeps you safe
This is where a specialist cybersecurity tool like Heimdal comes in. Through our patch management module, we enable IT administrators to build automated policies to decide what patches are installed and when. High risk vulnerabilities can be scheduled within two weeks (or ideally, sooner) to comply with Cyber Essentials, while lower-risk patches can be scheduled for later.
This means you can get the benefits of an automated patch management approach while still being in charge of what patches are installed and when.
4. Threat detection: A multi-stage approach
Traditional anti-malware tools operate on a ‘signature-based’ model of threat detection. This means they compare software and network activity against a database of known malware threats. When a match is made, an alert is generated.
To be compliant with the malware section of Cyber Essentials, you only need a signature-based threat detection tool. Indeed, the requirements even specify that you should update the signatures daily. But even this isn’t a silver bullet.
Like with traditional DNS tools, the signature-based method struggles to effectively identify unknown and emerging threats. If the malware isn’t in the database, it’s not getting blocked. Therefore, another approach is needed.
Read more: How Do Hackers Exploit Your Vulnerabilities?
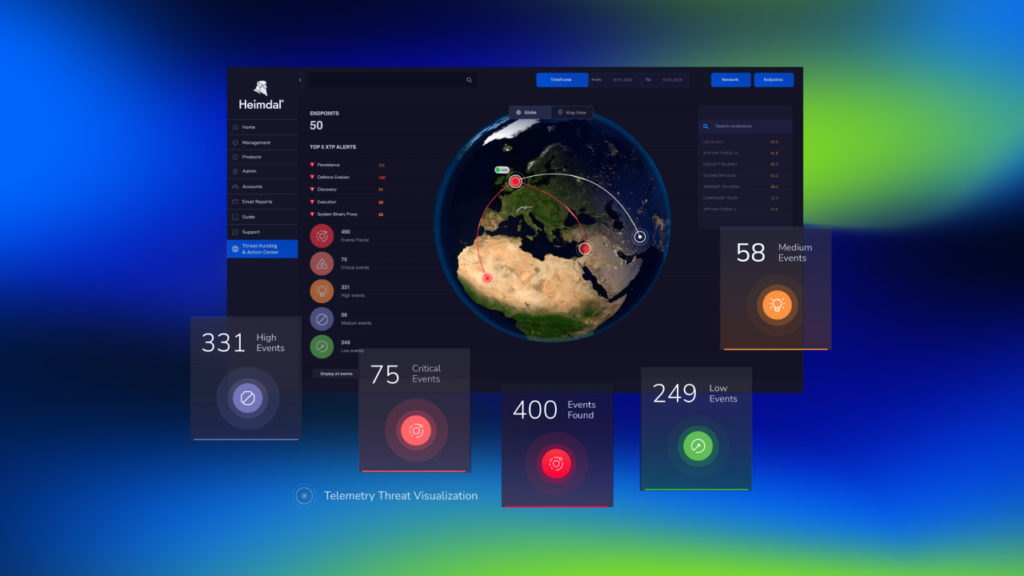
How Heimdal’s Threat-Hunting & Action Center keeps you safe
At Heimdal, our next-gen antivirus tool adds AI-powered behavioral analysis to the traditional signature-based approach. These tools use anomaly analysis to detect suspicious patterns of behavior in the IT network.
By analyzing the behavior of all software and events, Heimdal can identify and flag suspicious activity – even if the malware has already passed through the signature-based filter. This creates a much more proactive and effective defense against both known and unknown threats.
5. More security, fewer licenses, less hassle
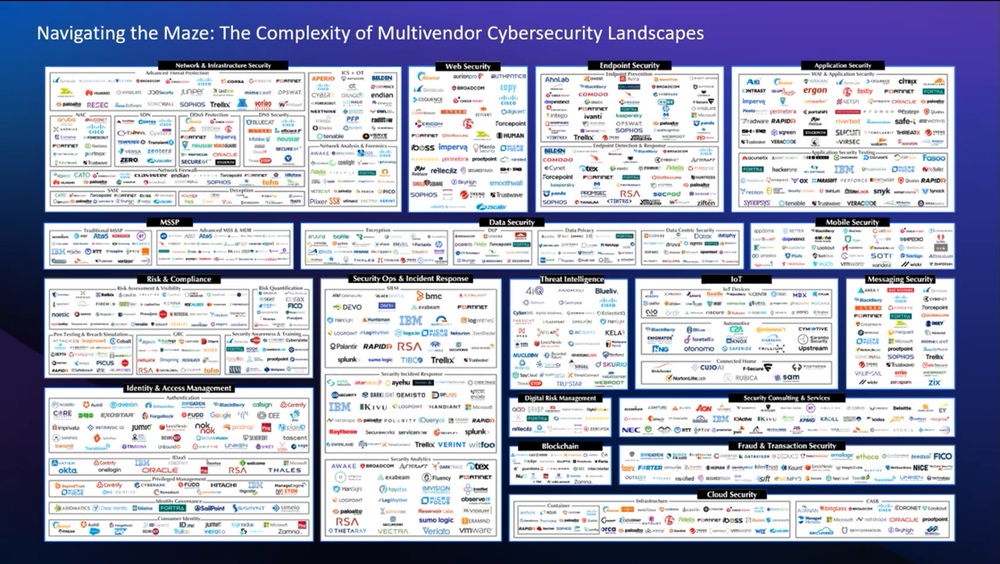
Once upon a time, effective cybersecurity required little more than installing an antivirus and setting up some password policies. As we’ve learned in this post, the situation today is much more complex.
Staying compliant with Cyber Essentials requires an increasing number of tools and licenses. This means IT teams are adding more and more cybersecurity products to their already sprawling IT environments. Each new license you purchase requires time, research, and additional costs. With limited resources and even tighter budgets, IT admins are quickly realizing that another approach is needed.
Read more: Consolidating Your Security Operations with Automated Threat Hunting
How Heimdal keeps you safe
At Heimdal, we offer the widest possible suite of cybersecurity features and functionality under a single license, including all the tools that we’ve discussed in this piece. Customers can choose which modules they need and receive a bespoke price based on the number of endpoints being monitored.
There are several benefits to this. With one license, vendor, and dashboard, you can reduce costs and complexity to an absolute minimum. But crucially, it also helps to improve security, because you can get the full picture of a potential threat in one place. This avoids a stunted and confused security coverage, with one tool searching for malware, another analyzing network connections, and another installing updates.
With Heimdal, cyber compliance is just the start
When I first get on the phone with an IT admin, I often encounter a similar story: A packed to do list and a schedule filled mostly with reactive firefighting. Against this backdrop, it’s easy to think that the bare minimum of cybersecurity defense is the best you can hope to achieve.
But as I’ve explained in this post, it is possible to get on the front foot and create a genuinely proactive and layered cyber defense. With the right tools and approach, it’s possible to both improve your security while reducing both the costs and time taken to manage it. Using a tool like Heimdal, compliance really is just the start.
So, when do you want to start?
If you want to find out more, book a demo today or get in touch with me directly at mic@heimdalsecurity.com










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security