Contents:
This piece is authored by Michael Coffer, Heimdal’s resident sales expert for the education sector. Michael speaks to hundreds of IT admins a year, so there are few people who understand the challenges of this sector better than him. Here, he explains why Heimdal is an increasingly popular choice for IT admins everywhere.
In the last year, some 71% of secondary schools have experienced a cyber breach or cyber attack. On its own, that’s cause enough for concern. But here’s another stat that really puts things into context: Only 52% of schools have actually identified breaches or attacks in the last year.
These alarming figures underscore why cybersecurity in schools and education data protection must be top priorities for IT administrators. A shocking number of educational institutions are targeted by hackers each year. Of those, many don’t even know they’ve been infiltrated.
As Heimdal’s sales representative for the education sector, I spend my working life talking to IT admins who want to avoid becoming one of these statistics. In this blog, I explain how the most proactive and effective teams are using modern tools and techniques to keep their IT environments safe and prevent a cyber-attack.
Why educational institutions are a prime cyber attack target for hackers
For a school IT admin, there are few things more important than protecting the sensitive information of students and teachers. But even the most effective teams find themselves working against a complex cocktail of different challenges:
1. Sensitive information
Schools and educational institutions collect large amounts of sensitive personal information. Generally, you’ll have information on personal details, addresses, financial information, and medical information for staff, employees, and students. This can be incredibly lucrative for hackers who successfully get their hands on it.
2. Complexity
In education, IT networks are large and complex, generally combining legacy systems with more modern devices and apps. This means the average IT administrator in a school manages a complex spaghetti-like network, with countless entry points for hackers to exploit. These networks are very difficult to effectively secure – a fact that malicious actors are very aware of.
3. Scale and scope
If a school experiences an outage, the effects will be huge. Most importantly, the valuable education of hundreds of young people will likely be disrupted until the situation has been resolved. Crucially, the reputational damage of that outage will be immediate and substantial. Cyber attackers therefore have a huge incentive to extort schools with tactics like ransomware.
4. Small budgets, smaller IT teams
The average IT team in a school, university, or trust consists of just one or two people. Generally, budgets are limited – particularly in the public sector. This lack of resources means IT teams rarely have the time and resources to think proactively. Against an increasingly sophisticated threat landscape, keeping your school safe can often feel like bringing a slingshot to a swordfight.
5. Intellectual property
This point is most relevant for universities and institutions that conduct exclusive research, which can be a huge potential target for hackers. For example, a university recently announced they’d discovered exclusive research in the quantum computing space, creating a huge headache for the IT team that had to keep that research safe.
How top schools protect themselves from hackers and cyber attacks
The issues we discussed in the last section are tough, but not insurmountable. Each day, I speak to proactive IT administrators finding solutions to these problems. Of course, much of that involves using the right technology – and tools like Heimdal have a huge role to play here. But it’s also about having the right mindset and approach.
Of course, every school and educational institution is different. But when I think of schools and IT admins that are leading the pack in security terms, there are a few methods and approaches that most of them have in common:
A layered approach
No single cybersecurity tool or policy can give you a 100% safety guarantee. Instead, the best approach is to combine multiple different tactics and strategies to create a multi-pronged defense.
This is because no cyber incident happens in a vacuum. A hacker’s end goal might be to install ransomware or exfiltrate data – but they’ve got a lot of steps to get through before they can achieve it. That might involve gaining access to the environment via phishing, escalating privileges, disabling security features, and more.
Effective security requires a defense to each of these tactics. Of course, you need a ransomware encryption protection (REP) tool to protect the IT network from encryption-based attacks. But the best approach is to combine this with DNS security, phishing protection, privileged access management, and more. The more layers of protection you have, the better your chance of keeping the hackers out.
Read more: How to Defend Against the Three Most Dangerous Cybersecurity Attacks
See the results in action: Park Community School
Heimdal has been crucial for our school’s cybersecurity. Its DNS Security feature blocks harmful websites effectively, enhancing our defenses against phishing and malware.
Additionally, the Ransomware Encryption Protection module ensures our sensitive data is secure, providing realtime detection and preventing potential ransomware attacks.
– Chris Maddocks, IT Manager, Park Community School
Schools like Park Community School instinctively understand the importance of this layered approach. As well as ransomware encryption protection, the team also invests in email and DNS network security. This helps defend against ransomware at every stage of the attacker’s journey, creating a much more effective defense.
Consolidating cybersecurity tools
Today, cybersecurity is getting increasingly complex. That’s particularly the case if you want to create the layered approach we discussed in the last section. Now, IT admins need an increasingly vast set of tools and products to help manage their growing IT networks. Doing that amidst small budgets and limited resources only makes the job harder.
To avoid these issues, the most proactive IT admins are increasingly turning to tools like Heimdal that offer the broadest possible package of features under a single license.
Let’s consider an example to see why this is so effective. Let’s imagine that, in a year’s time, Cyber Essentials introduces a new requirement for accredited organizations to have privileged elevation and delegation management (PEDM) functionality. With the traditional approach, this would mean you have to research the market, engage a sales rep, do your due diligence, choose the right vendor, and roll out the product.
And every time you need a new security tool, the process starts all over again.
But with a tool like Heimdal, you would simply activate the PEDM module in your Heimdal dashboard. Then, the additional functionality can be added to your solution, and alerts can be seamlessly integrated into your existing dashboard. This significantly reduces the time you spend researching and installing new security products.
Read more: Consolidating Your Security Operations with Automated Threat Hunting
See the results in action: The Education Alliance
The Education Alliance decided that Heimdal was the perfect fit for our organization. Having multiple products within the suite meant it was scalable and easy to add additional schools onto the system.
If you’re looking for an antivirus product nowadays, it’s not just about the AV engine: It’s about the wraparound of third-party patching, updates, and isolating devices when a threat appears. For me, Heimdal ticks all those boxes.
– Matt Wadsworth, Director of IT, The Education Alliance
When The Education Alliance first engaged Heimdal in 2018, the team specifically needed a product that would easily scale across new schools and security requirements. The team rolled Heimdal out across their largest secondary school, with over 1,000 devices to protect. Now, the platform makes it much easier to manage large scale cybersecurity across multiple tenants, devices, and organizations.
Getting on the front foot with a proactive approach
Traditional cybersecurity tools generally take a reactive approach. The goal is generally to detect and prevent a particular attack as it’s happening – rather than closing down the initial entry points. Investing in proactive tools as well can therefore make a huge difference to the success of your security coverage.
But what does proactive cybersecurity look like? Generally, this involves DNS network filtering, email security, and automated vulnerability management. This can significantly reduce the risk of hackers gaining entry to your environment via insecure connections, phishing, or exploits.
Compliance frameworks like Cyber Essentials generally focus on reactive tools. But if you’re only implementing the minimum security required by compliance, you’ll end up with a largely reactive approach. Increasingly, the most effective IT teams know that a mixture of proactive and reactive tools is by far the best way to keep their sensitive data safe.
Read more: Stay Ahead of Cyberthreats with Proactive Threat Hunting
See the results in action: SAU 67
Over the years, we’ve tried various endpoint solutions, but they often posed challenges in terms of management or simply didn’t get the job done effectively. Microsoft’s WSUS server also left us frustrated when it came to handling Windows patching, and we lacked a solid solution for third-party applications. That’s when we discovered Heimdal.
Trust me, it’s a game-changer for your IT department – saving you a ton of time.
– Roy D. Bailey Jr., Chief Technology Director, SAU 67
SAU 67 is an education company that works with primary and secondary schools across New Hampshire, US. When the team first came to Heimdal, they needed to get on the front foot of vulnerability management and threat detection to create a more effective and proactive approach.
Now, they have a single solution to manage all their vulnerabilities. At the same time, the proactive threat detection tools have been praised by an independent security company.
Improving response with managed support
Given the increasingly complex nature of cybersecurity, it’s no surprise that IT admins are looking to managed security service providers (MSSPs) to help manage their IT networks. With small teams and tight resources, many simply don’t have the bandwidth to monitor their many cybersecurity dashboards.
Even if you can keep on top of the alerts, you definitely can’t respond to a significant incident when you’re not at work. The best approach, therefore, is to engage a team of security experts to monitor and manage your IT network 24/7. This means, when the worst happens, a trained security professional will be on hand to respond in minutes – whatever time of day or night it is.
But it’s not just about the worst-case scenario. Having a fully managed security product significantly reduces the amount of the time you have to spend manually installing patches, customizing policies, and responding to alerts. This is increasingly becoming one of the best ways for small teams to achieve a genuinely robust level of security coverage.
Read more: What Is An MSP (Managed Service Provider)? A Vendor and Buyer Guide
Cybersecurity for Schools: Build a layered approach to security with Heimdal
There are many things that the most effective IT teams in education have in common. But if I were to sum it up in my own words, it’d be this: Successful IT admins are constantly thinking ahead. It’s not enough just to implement the smallest amount of tools you need to stay compliant. Instead, you need to build a proactive, layered approach that targets every possible entry point a hacker could seek to exploit.
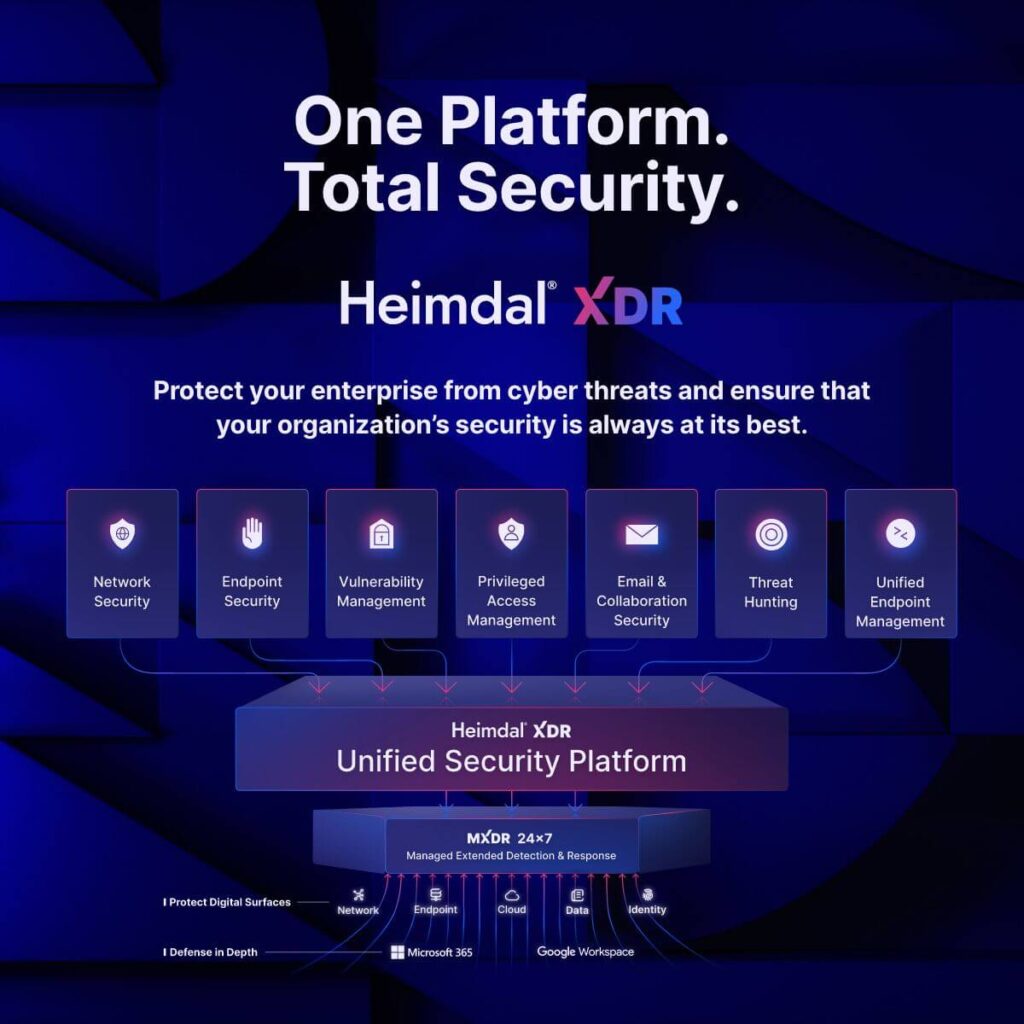
At Heimdal, we make it as easy as possible to build this layered approach, by combining the widest single suite of cybersecurity tools in one license. That includes:
1. Network security
Protect your environment from malicious connections with advanced DNS filtering.
2. Vulnerability management
Achieve fully automated patch management according to customized policies you create. This gives you full control of what patches are automatically installed and when.
3. Privileged access management
Protect your privileged accounts and credentials with PASM, PEDM, and Application Control products.
4. Endpoint security
Monitor activity and threats on end-user devices through advanced endpoint security.
5. Threat hunting
Our next-gen antivirus and ransomware encryption protection tools monitor user behavior to identify anomalous activity even after the hackers have infiltrated your IT environment.
6. Unified endpoint management
Manage traditional desktops, remote endpoints, and bring-your-own-devices through a single integrated interface.
7. Email and collaboration security
Protect students and teachers from phishing attacks through advanced email security and fraud prevention tools.
Using Heimdal isn’t the only way to overcome the challenges and difficulties we discussed in this piece. But in my experience, it’s by far the most effective cybersecurity solution for educational institutions.
If you want to find out more, book a demo today or get in touch with me directly at mic@heimdalsecurity.com










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security