Contents:
The Cuba ransomware gang has been seen launching attacks on critical infrastructure organizations in the U.S. and IT firms in Latin America, employing a mix of older and newer hacking tools.
The latest campaign, identified by BlackBerry’s Threat Research and Intelligence team in early June 2023, reveals that Cuba is using CVE-2023-27532 to extract credentials from configuration files.
This specific vulnerability affects Veeam Backup & Replication (VBR) products, and an exploit has been publicly available since March 2023.
Details of the Attack
According to BlackBerry, the Cuba gang’s initial access seems to come from compromised admin credentials via RDP, without brute-forcing involved.
Subsequently, Cuba’s signature custom downloader, “BugHatch,” establishes communication with the C2 server to download DLL files or execute commands.
Cuba gains an initial foothold in the target environment using a Metasploit DNS stager that decrypts and runs shellcode directly in memory.
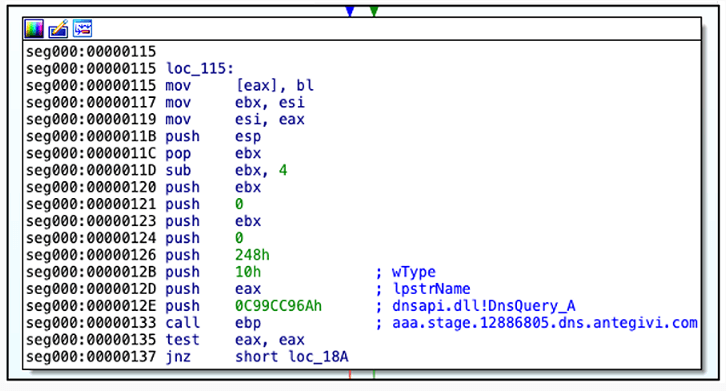
DNS Stager Query (Source)
Cuba also employs the increasingly popular BYOVD (Bring Your Own Vulnerable Driver) technique to disable endpoint protection tools and uses the “BurntCigar” tool to terminate kernel processes linked to security products.
Alongside the recent Veeam flaw, Cuba exploits the CVE-2020-1472 (“Zerologon”) vulnerability in Microsoft’s NetLogon protocol, allowing privilege escalation against AD domain controllers.
In the post-exploitation phase, Cuba was observed using Cobalt Strike beacons and various “lolbins.”
Cuba’s Likely Origin and Motivation
BlackBerry points to a likely financial motivation behind Cuba’s actions and suggests that the gang is probably Russian, a hypothesis supported by other cyber-intelligence reports.
This assessment is based on the exclusion of computers with Russian keyboard layouts from infections, Russian 404 pages on parts of the gang’s infrastructure, linguistic hints, and the group’s targeting of Western entities, explains Bleeping Computer.
Cuba’s Continued Threat
Cuba ransomware continues to pose a significant threat four years after its emergence, a rarity in the ransomware world.
The gang’s adoption of CVE-2023-27532 emphasizes the urgency of installing Veeam security updates and highlights the dangers of postponing updates when publicly accessible PoC (proof-of-concept) exploits are available.
BlackBerry Research’s full report is available here.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and Youtube, for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








