Contents:
Threat actors managed to get access to internal customer support and account management systems at MailChimp, the email marketing company reported on Sunday. The hackers’ goal was to perform audience data theft and lead phishing cyberattacks.
MailChimp Data Breach: What Happened
Owners of Trezor hardware cryptocurrency wallets who got phishing messages suggesting the business had suffered a data breach were all over Twitter on Sunday morning.
Trezor clients were invited through these phishing notifications to reset their hardware wallet PINs by downloading malicious software, that permitted hackers to steal stored cryptocurrency.
Trezor later revealed that the phishing assault was carried out by hackers targeting the crypto industry, who had hacked MailChimp.
Here is what that false MailChimp data breach notification looked like:
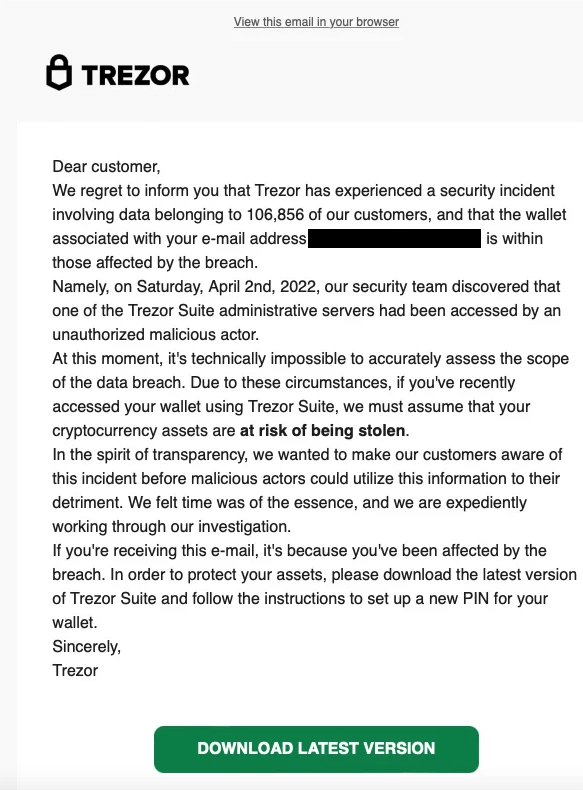
What MailChimp Said
According to the BleepingComputer publication, MailChimp acknowledged in a confirmation email that the severity of the data breach exceeded simply gaining access to Trezor’s accounts.
As MailChimp further tells, several of their employees were victims of a social engineering attack, which resulted in their credentials being stolen.
On March 26, our Security team became aware of a malicious actor accessing one of our internal tools used by customer-facing teams for customer support and account administration. (…) The incident was propagated by an external actor who conducted a successful social engineering attack on Mailchimp employees, resulting in employee credentials being compromised. (…) We acted swiftly to address the situation by terminating access for the compromised employee accounts and took steps to prevent additional employees from being affected.
Hackers employed these credentials to get into 319 MailChimp accounts and export “audience data” from 102 client accounts, most probably mailing lists.
According to the same publication, the threat actors also acquired access to API keys for an unspecified number of clients, which have since been removed and are no longer usable.
What Are API Keys and How Can Hackers Exploit Them?
API keys stand for access tokens that let MailChimp customers manage their accounts and run marketing campaigns straight out from their own websites or platforms.
Without accessing MailChimp’s customer interface, a hacker can develop custom email campaigns, such as phishing campaigns, and distribute them to mailing lists using these obtained API credentials.
It seems that the threat actors under discussion accessed consumers in the bitcoin and finance industries and that all of the compromised account holders had been alerted.
What Are MailChimp’s Recommendations?
MailChimp claims to have received reports of this access being used to execute phishing campaigns against stolen contacts, but no details about the attacks have been released.
For enhanced security, MailChimp recommends that two-factor authentication should be used on all customer accounts.
The Mailchimp’s CISO, Siobhan Smyth, also declared that
We sincerely apologize to our users for this incident and realize that it brings inconvenience and raises questions for our users and their customers. We take pride in our security culture, infrastructure, and the trust our customers place in us to safeguard their data. We’re confident in the security measures and robust processes we have in place to protect our users’ data and prevent future incidents.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








