Contents:
A critical WordPress plugin RCE (remote code execution) vulnerability has been identified in version 5.0.4 and older of Essential Addons for Elementor, the well-known library.
How Does the WordPress Plugin RCE Work?
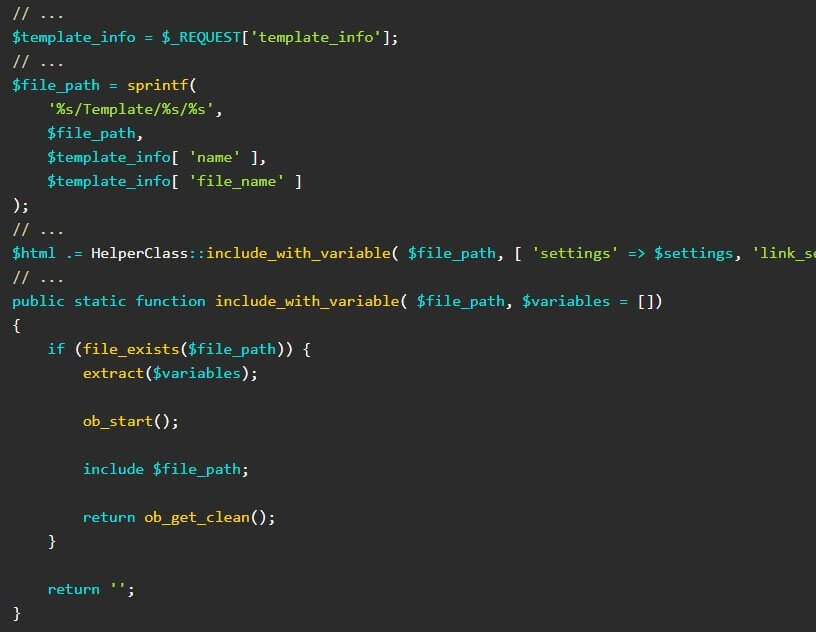
The WordPress plugin RCE works by letting an unauthenticated user initiate an inclusion attack on a local file, like, for instance, a PHP file. This is done for code execution purposes on the website.
The ones who discovered this flaw in the WordPress popular plugin are the researchers from PatchStack.
They further explained the reason for the existence of this flaw and the conditions under which it occurs.
The local file inclusion vulnerability exists due to the way user input data is used inside of PHP’s include function that are part of the ajax_load_more and ajax_eael_product_gallery functions. (…) It should be noted that the vulnerability only exists if widgets (dynamic gallery, product gallery) are used which utilize these functions due to the fact that a nonce token check is present. This nonce token is only visible when these widgets are enabled.
The experts also provided some examples of code snippets that trigger the plugin remote code execution flaw in WordPress.
Twice Patched, Twice Failed
According to BleepingComputer, the developer of the plugin was aware of the issue at the time of its discovery by researcher Wai Yan Muo on January 25. He then proceeded with releasing version 5.0.3 to address it. The solution was to implement to the user input data a function dubbed “sanitize_text_field”. In this case, however, even with the sanitization put in place, local payloads inclusion would not have been prevented.
What followed next was another patching attempt with the release of version 5.0.4. This new update came with the “sanitize_file_name” function and would have worked on sanitization overriding prevention. In other words, it was designed to remove characters like special ones, dots, or slashes that could have overridden the sanitization phase.
At that moment, Patchstack found version 5.0.4 vulnerable as they tested it and they let the developer know about their discovery and the fact that the latest patch was not addressing the issue entirely.
Eventually, the plugin author released version 5.0.5. This is designed to work on malicious pathname resolutions prevention by means of PHP’s “realpath” function.
Recommended Mitigation for the Current Critical WordPress Plugin RCE
Users are recommended to upgrade to the last Essential Addons for Elementor version (5.0.5.) immediately, an update released on the 28th of January 2022.
According to some WordPress statistics, almost 380,000 times the new plugin version has been installed until now and since this library is used by over 1 million WordPress sites, this indicates that over 600K sites are still exposed currently and require immediate patching.
You can apply the patch either by clicking here or going to your WP dashboard and applying it from there.
What Does the Essential Addons for Elementor Represent?
The Essential Addons for Elementor plugin is an extension that provides a set of tools to help you with your design process. These are all the tools that you need, in order to create beautiful layouts and designs.
The plugin includes a wide variety of modules that can be used to create different types of content. This includes modules for text, images, videos, sliders, and more.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










