Contents:
Colonial Pipeline was recently the victim of a ransomware attack having to temporarily stop pipeline operations and several IT systems as a result.
The new phishing campaign is using emails that are targeted and written just as urgent notifications asking to download and install a system update that is able to defend against the latest ransomware strains.
The threat actors made good use of the time they had since the Colonial Pipeline incident and used it as a theme in a new phishing campaign deployed a couple of weeks later.
The researchers at INKY analyzed the attack that attempted to compromise computer systems using the Cobalt Strike penetration testing tool, with the fake emails using the Colonial Pipeline attack as an example of the devastating consequences of a ransomware incident like that can have on an organization.
The emails are urging the recipients to install a system update from an external link and therefore enable the system to “detect and prevent the latest strains of ransomware”, whilst offering a deadline for applying the update in order to increase urgency.
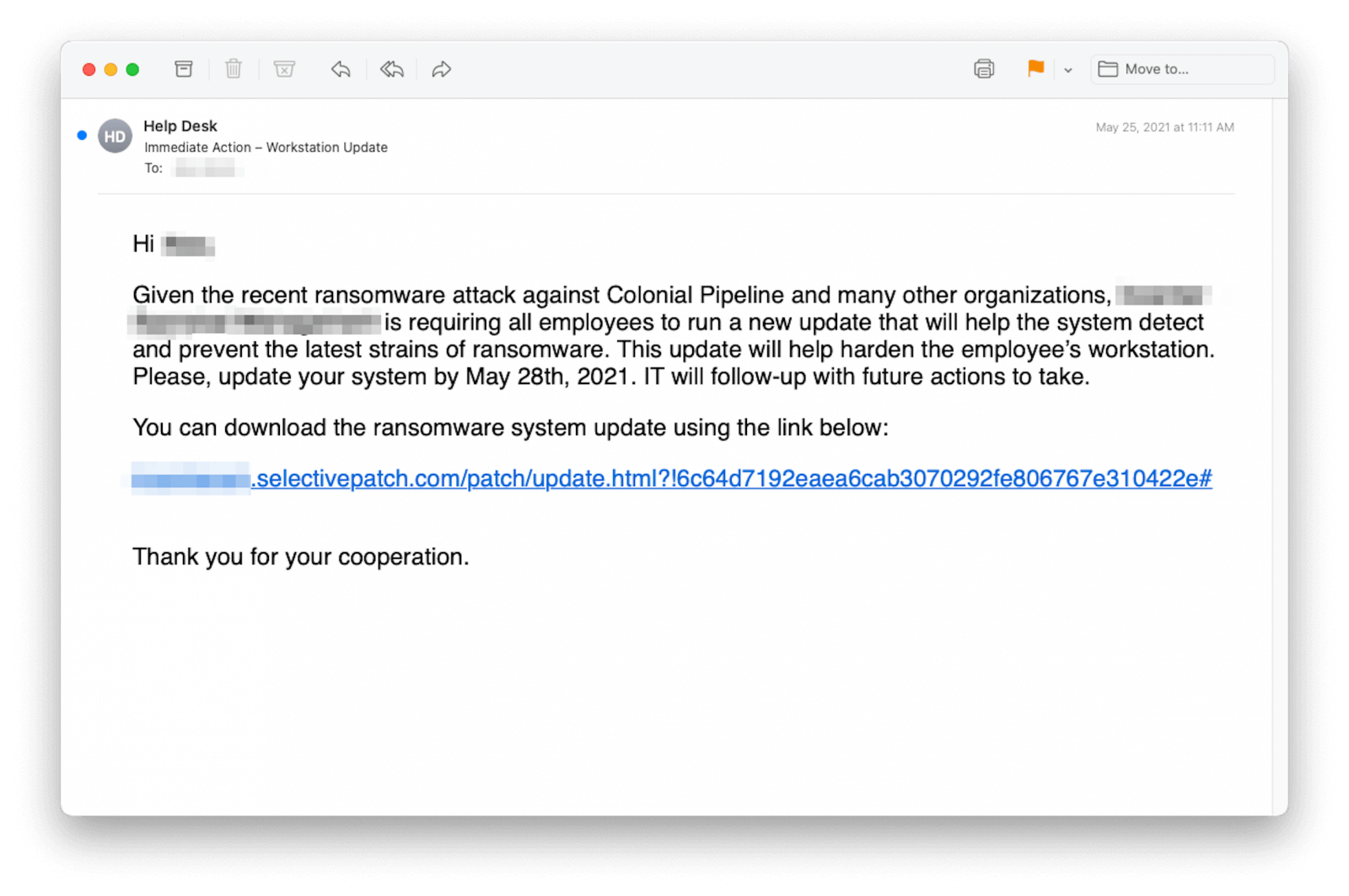
The threat actor is using domains that can be easily mistaken with legitimate ones (ms-sysupdate[.]com and selectivepatch[.]com), registered towards the end of May through Namecheap.
The researchers at INKY also note that the domains were not used only for sending the malicious emails, but also for hosting the so-called “ransomware update” executables.
In both cases, the download pages were customized with the target company’s logo and imagery in order to make them appear trustworthy.
The researchers believe that the payload was Cobalt Strike, a software developed for penetration testing purposes that are unfortunately often used by malicious actors, especially in ransomware attacks.
Unfortunately, the source code for Cobalt Strike was leaked in 2020, thus making it accessible to a wider variety of adversaries, but on the bright side, the payload used in this phishing campaign can be easily detected by a large number of antivirus solutions.
It’s worth noting that attackers in the phishing business are keeping an eye on the news in order to be able to create new and relevant lures to increase the success of their campaigns, as users are more receptive to messages that are containing familiar information.

Heimdal™ Ransomware Encryption Protection
- Blocks any unauthorized encryption attempts;
- Detects ransomware regardless of signature;
- Universal compatibility with any cybersecurity solution;
- Full audit trail with stunning graphics;
In this specific situation, the attack on Colonial Pipelines brought attention to the ransomware threat and the way in which it happened to affect sensitive organizations.
In this environment, phishers tried to exploit people’s anxiety, offering them a software update that would “fix” the problem via a highly targeted email that used design language that could plausibly be the recipient’s company’s own. All the recipient had to do was click the big blue button, and the malware would be injected.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










