Contents:
A new malware sample was detected outside of the Play Store, on sites where people end up after receiving smishing (SMS) messages. The researchers at IBM Trusteer discovered that the HTTPS sites used would notify potential victims that their Android version is obsolete and provide an APK that would reportedly upgrade them to the most recent version.
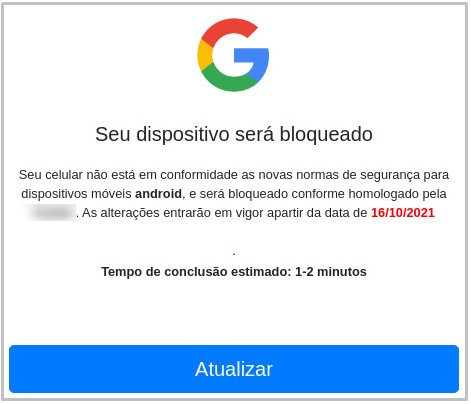
BrazKing M.O.
As thoroughly explained by BleepingComputer, the virus is planted on the device and seeks access to the ‘Accessibility Service’ if the user allows “downloads from unknown sources.”
This permission is being exploited to record screenshots and keystrokes without seeking any other permissions that would raise concerns.
The accessibility service is primarily utilized by BrazKing for a malicious activity like Keylogger capabilities, RAT capabilities, SMS, and contact list access.
BrazKing no longer utilizes the ‘getinstalledpackages’ API call to see what applications are installed on the infected device; instead, it leverages the screen dissection capability.
BrazKing now overlays without the ‘System Alert Window’ permission, therefore it is possible for it to overlay a phony screen on top of the real program as other trojans can.
Instead, it uses a webview window opened from within the accessibility service to load the bogus screen as a URL from the attacker’s server. This protects the program and all of its windows, but it does not require you to quit it.
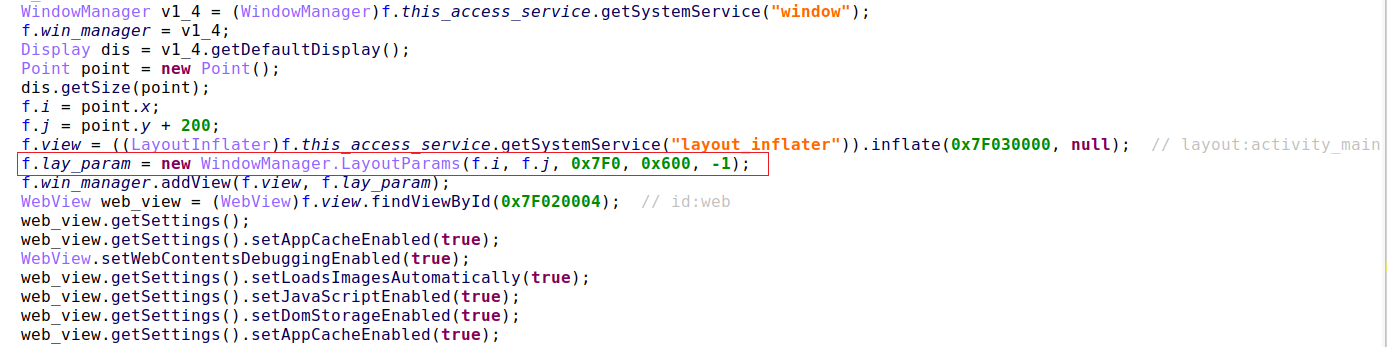
Instead of showing built-in overlays when detecting an online bank login, the malware will now connect to the command and control server to get the necessary login overlay to display.
Threat actors will be able to steal credentials for a wider range of banks using this dynamic overlay approach. The attacker may also update the login screens as needed to match with updates to genuine banking applications or sites or add support for additional banks, by serving the overlays from their servers.
Internal resources are protected in the latest version of BrazKing by performing an XOR operation using a hardcoded key and then encoding them with Base64.
The trojan’s ability to steal 2FA codes, passwords, and screenshots without hoarding permissions makes it a lot more dangerous than it used to be, so use caution when downloading APKs from sources other than the Play Store.
BrazKing looks to be controlled by local threat organizations, according to the IBM assessment, because it is propagating on Portuguese-language websites.
If you liked this article follow us on LinkedIn, Twitter, YouTube, Facebook, and Instagram to keep up to date with everything cybersecurity.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








