Contents:
Security researchers in South Korea have discovered a malware distribution operation on YouTube that uses Valorant cheat baits to fool gamers into downloading RedLine, malicious software that can steal information and infect operating systems with malware.
It seems that it’s easy for cybercriminals to get around YouTube’s new content submission reviews or create new accounts when reported and blocked, hence this sort of abuse is quite prevalent.
The campaign, discovered by South Korean security software provider AhnLab, is aimed at the gaming community of Valorant, a free-to-play first-person hero shooter developed and published by Riot Games for Microsoft Windows.
According to BleepingComputer, the operation provides a link to download an auto-aiming bot on the description of the video.
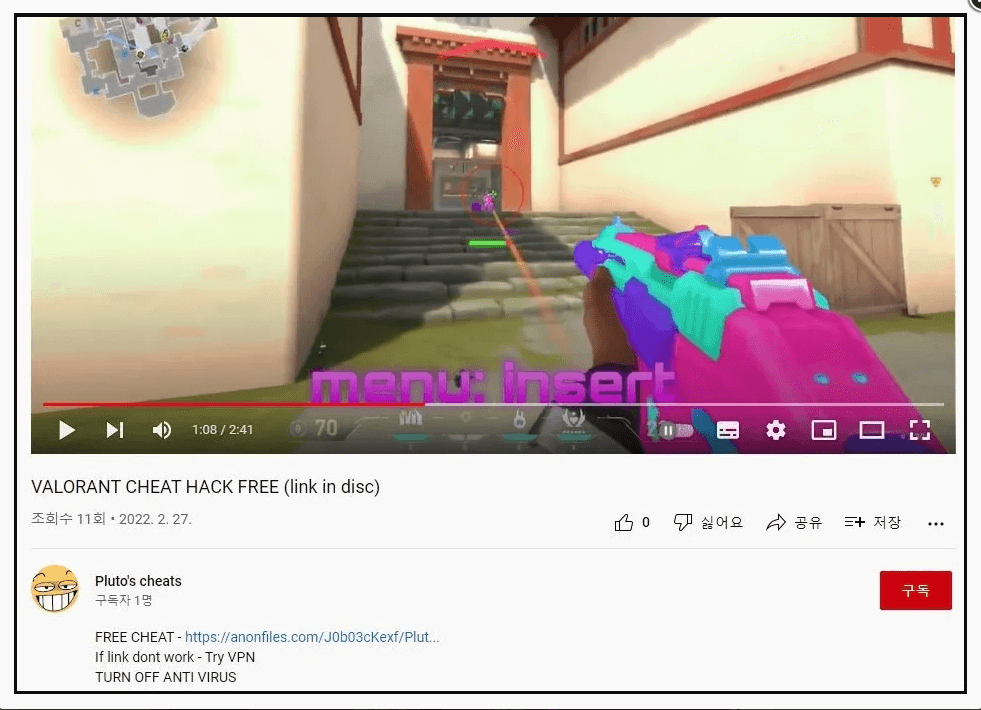
How Does It Work?
These cheat lures are supposedly game add-ons that allow players to aim at adversaries quickly and precisely, enabling them to win headshots without showing any expertise.
As explained by BleepingComputer, for popular multiplayer games such as Valorant, auto-aiming bots are in high demand as they allow for easy ranking progression.
How Is the Redline Info Stealer Dropped?
Players who try to download the file in the video’s description will be directed to an anonfiles website, where they will be given a RAR archive containing the “Cheat installer.exe” executable.
This file is actually a copy of RedLine stealer, one of the most commonly used password-stealing malware infections, and according to BleepingComputer, grabs information from compromised systems, including:
- Basic information: Computer name, user name, IP address, Windows version, system information (CPU, GPU, RAM, etc.), and list of processes
- Web browsers: Passwords, credit card numbers, AutoFill forms, bookmarks, and cookies, from Chrome, Chrome-based browsers, and Firefox
- Cryptocurrency wallets: Armory, AtomicWallet, BitcoinCore, Bytecoin, DashCore, Electrum, Ethereum, LitecoinCore, Monero, Exodus, Zcash, and Jaxx
- VPN clients: ProtonVPN, OpenVPN, and NordVPN
- Others: FileZilla (host address, port number, user name, and passwords), Minecraft (account credentials, level, ranking), Steam (client session), Discord (token information)
After gathering this data, RedLine cleverly bundles it in a ZIP archive called “().zip” and exfiltrates the files via a WebHook API POST request to a Discord server.
Links in YouTube Videos Are Dangerous
Aside from the fact that using various tools to create an advantage beyond normal gameplay is unfun and ruins the game for others, it is almost always a potentially severe security threat.
None of these cheat methods are created by reputable companies, none of them are digitally signed (so antivirus warnings are likely to be ignored), and many of them are malware. The videos that advertise these tools are frequently stolen from other sources and re-posted on new channels by malicious users as lures.
Even if the uploader is praised in the comments section and the tool is said to work as advertised, remember to not rely on them as these types of comments can be easily faked.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








