Contents:
Cybersecurity experts say that yes, deepfakes can be used for a variety of cybercrimes including political propaganda, disinformation, foreign influence activity, scams and fraud.
In fact, a team of Californian cybersecurity researchers identified a recent increase in underground services that allow cybercriminals to produce them.
Deepfakes Can Be Bought Via Telegram
‘RealDeepFake’ is a recently discovered underground service that allows threat actors to create a deepfake instance of their chosen character, apply a voiceover from a selected script, and even add effects and text for a small fee. The service is available through Telegram groups.
According to Security Affairs, these deepfakes were used to impersonate celebrities like Donald Trump, Elon Musk, The Rock and Snoop Dogg. Scammers also use them to convincingly impersonate C-Suite Executives in video chats or phone calls in order to give their staff false wire transfer instructions.
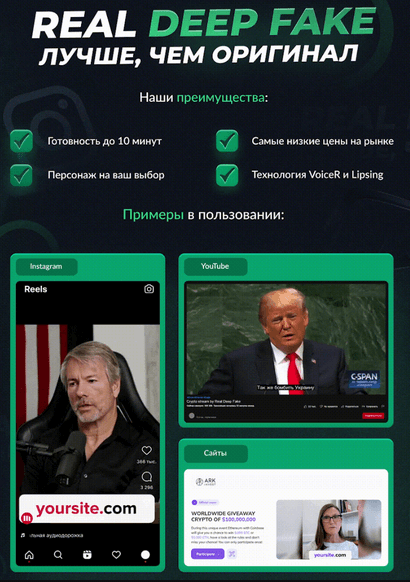
The Federal Trade Commission recently reported that since the beginning of 2021, American consumers have lost over $1 billion in cryptocurrency as a result of scams. Experts advise that cybercriminals will most likely use deepfakes to deliver misleading information about bitcoin as well as Initial Coin Offerings (ICOs) using celebrity profiles.
They also expect to see more hybrid attacks that will deceive both everyday consumers and crypto professionals. The attacks will likely combine persuasive email and social media blasts, fraudulent mints, and expertly rendered deepfakes of high-profile Web3 influencers.
Origins of Deepfakes
Firstly introduced by Canadian researchers in 2014, Generative Adversarial Networks (GANs) are generative models that create new data instances which resemble your training data. Because GANs can create images that look like pictures of human faces and can imitate people’s speech, unique facial features and gestures, the online communities gave them a name: ‘DeepFakes’.
My colleague Bianca analyzed them in detail in this article, where you can also learn how to spot a deepfake photo or video and how to protect yourself or your business from this clever social engineering trick.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








