Contents:
A new report shows that the number of malicious aged domains is growing and represents a risk to cybersecurity. Out of them, almost 22.3% of strategically aged domains are to some extent dangerous.
Researchers discovered this based on the SolarWinds case, as the threat actors behind this famous attack used domains created years before starting their malicious activity.
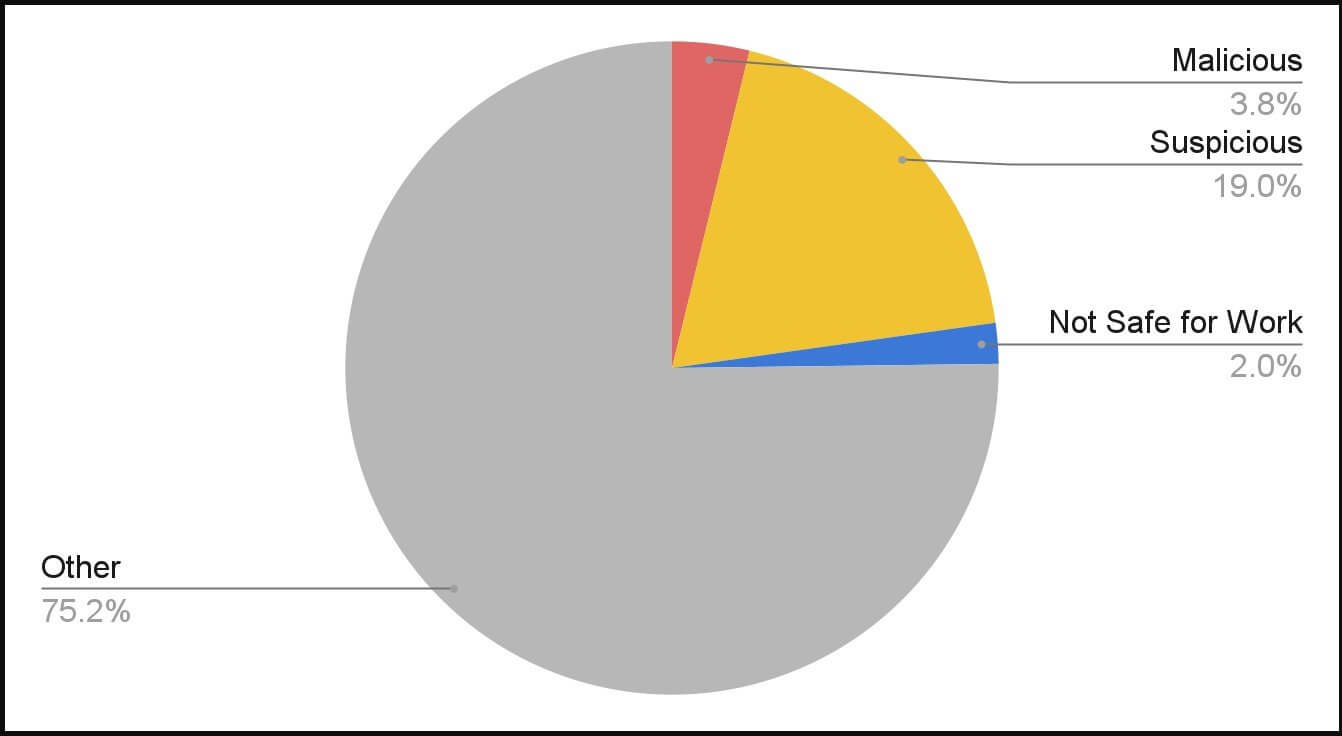
Experts from Palo Alto Networks’ Unit42 published a report after they investigated every day of the month of September 2021 tens of thousands of domains. One of the findings revealed in the paper shows that they identified almost 3.8% malicious domains, 19% potentially malicious domains, and 2% posing a risk to work environments.
The statistics of the analyzed domains were also depicted in a diagram:
The Reason Behind the Aged Domains Trend
Researchers explain that
Threat actors may register domains long before launching attacking campaigns on them. There are various motivations for this strategy. First of all, the longer life of aged domains can help them evade some reputation-based detectors. Secondly, C2 domains belonging to APTs can sometimes be inactive for years. During the dormant period, APT trojans only send limited “heartbeat” traffic to their C2 servers. Once the attackers decide which targets are valuable to them and start active exploits, the C2 domain will receive significantly more penetration traffic. (…) Therefore, it’s essential to keep monitoring domains’ activities and digging for threats behind aged domains associated with abnormal traffic increases.
Usually, newly registered domains, also met under the acronym NRD, are more prone to be malicious and that’s why security solutions focus on them and consider these as being suspicious. Nevertheless, the experts underline the fact that the danger posed by aged domains exceeds by far the danger of newly registered ones.
In some of the cases, these domains remained dormant for a period of 2 years before their DNS traffic met a rapid growth by 165 times, this fact pointing out that a cyberattack would happen.
How to Identify a Malicious Domain?
According to BleepingComputer, the sudden spike in a domain’s traffic indicates with no doubt its malicious nature, as the traffic for legitimate services that had their domains registered months or years before grows gradually.
On the other hand, the content of illegitimate domains is normally not complete, controversial, or cloned and they also lack WHOIS registrant details.
The DGA (domain generation algorithm) subdomain generation, that mechanism with the role of generating unique domain names and IP addresses, can also indicate an aged domain that was particularly created to serve malicious purposes.
The Pegasus Spying Campaign
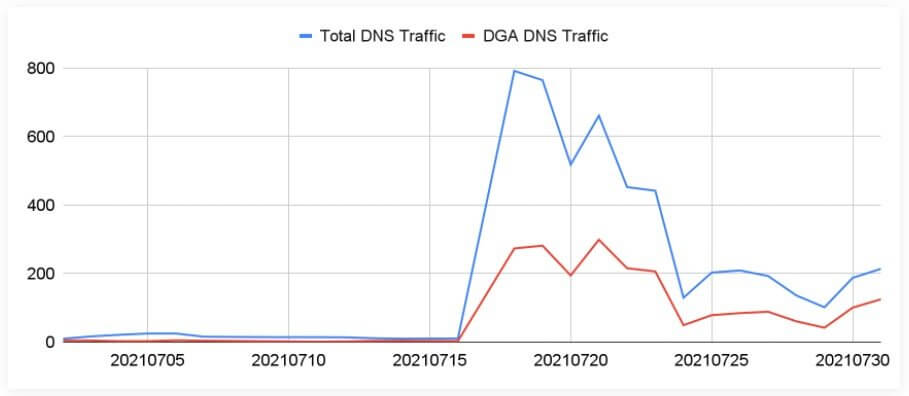
Unit42 has identified a real case in September discovering the Pegasus spying campaign. This used two C2 domains. They were both registered back in 2019 and left dormant until July 2021.
The researchers discovered this fact by means of the DGA subdomain detector which identified the growth in DNS traffic volumes as 56 times higher than normal.
How Can Heimdal™ Help?
Threats at the domain level are more frequent nowadays, that is why an efficient DNS traffic filtering like our Threat Prevention becomes indispensable for any company that wants to keep its critical assets well safeguarded. Our solution encompasses applied neural network modelling that helps in predicting future threats with a 96% accuracy. The product is based on code-autonomous endpoint DNS, and spots malicious URLs or processes, keeping cyberattacks away and closing off data leaking venues.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








