Contents:
A critical RCE flaw discovered in the open-source Internet forum Discourse tracked as CVE-2021-41163, has been addressed in an urgent update on Friday.
What Is Discourse?
Discourse, which was founded in 2013, is an open-source Internet forum and mailing list management platform. According to Wikipedia, the application is written with Ember.js and Ruby on Rails. PostgreSQL serves as its back-end database management system.
Discourse deviates from existing forum software in terms of usability by incorporating features recently popularized by large social networks including:
- infinite scrolling;
- live updates;
- expanding links;
- drag and drop attachments.
Versions 2.7.8 and earlier are exposed, and the best approach to mitigate the risk is to update to 2.7.9 or later, which was released last week. The issue has also been addressed in the most recent beta and test versions.
As per official figures, the open-source platform for community discussion was used to publish 3.5 million posts in September 2021, which were seen by 405 million users.
Due to its popularity, Cybersecurity and Infrastructure Security Agency (CISA) issued an alert about the vulnerability, encouraging forum administrators to update to the most recent available version or implement the necessary steps for overcoming future attacks.
According to BleepingComputer, the researcher who detected the vulnerability reported it as soon as he became aware of it, on October 10, 2021.
In impacted versions, maliciously crafted requests could result in remote code execution. This was caused by a lack of validation in subscribe url values.
Calls to `open()` with user supplied input allows to invoke OS commands with whatever rights the web app runs on, which is typically ‘www-data’ (admin).
The implications of a CVE-2021-41163 exploit and the ease of leveraging it (sending an unauthenticated POST) result in a CVSS v3 score of 10.0 (critical), so patching it should be treated as an emergency.
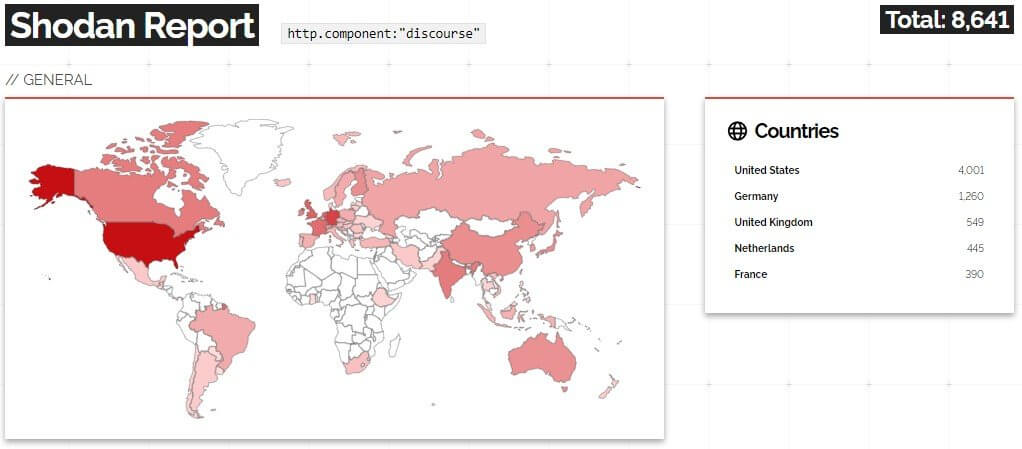
Even though all the Software-as-a-Service (SaaS) variants of Discourse were patched against the flaw as of Wednesday, many vulnerable deployments may still exist. On Monday morning, a Shodan search returned 8,640 Discourse deployments.
Admins who can’t update to the most recent version are recommended to restrict requests starting with ‘/webhooks/aws’ at an upstream proxy.
The issue is still being investigated, but the security expert who identified it has provided extensive technical information about it.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










