Contents:
Accenture, a global professional services company with leading capabilities in digital, cloud, and security, has recently confirmed they’ve been hit with a ransomware attack. Apparently, the threat actor behind the operation is none other than the LockBit 2.0 ransomware gang.
The Irish-based company reported revenues of $44.33 billion and had 569,000 employees in 2020. Its current clients include 91 of the Fortune Global 100 and over three-quarters of the Fortune Global 500.
What Happened?
Two months ago, the LockBit ransomware gang introduced their new LockBit 2.0 ransomware-as-a-service to the public. BleepingComputer reported that the threat actors announced they will publish the data if a $50 million ransom is not paid.
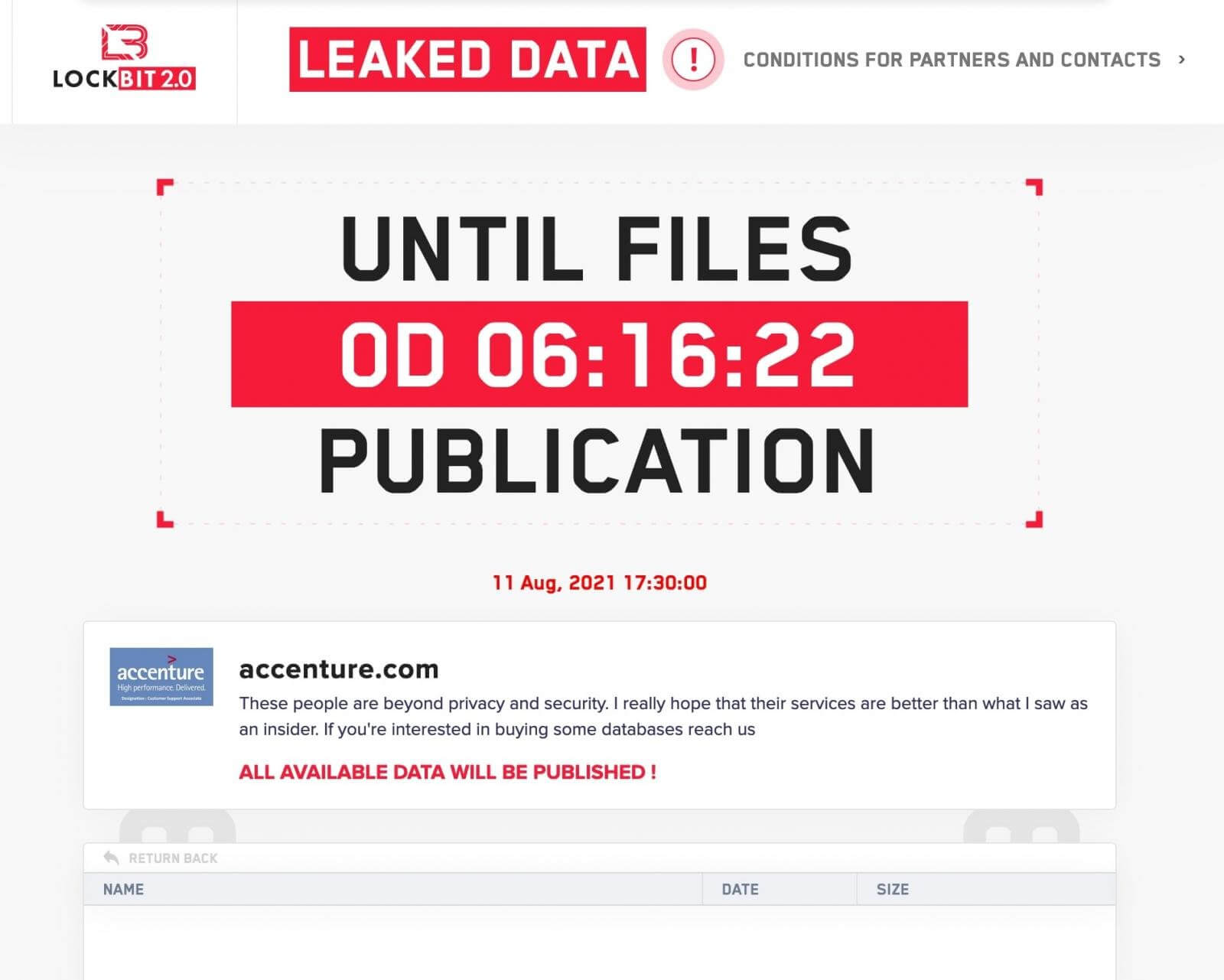
Although there is no proof of the stolen data, LockBit states on their data leak site that they’re willing to sell it to any interested parties.
These people are beyond privacy and security. I really hope that their services are better than what I saw as an insider. If you’re interested in buying some databases reach us.
There is also no exact timestamp of when the attack took place, when it was first noticed, its purpose, or the technical cause of exploitation.
Accenture revealed to BleepingComputer that impacted systems had been recovered from a backup:
Through our security controls and protocols, we identified irregular activity in one of our environments. We immediately contained the matter and isolated the affected servers. We fully restored our affected systems from back-up. There was no impact on Accenture’s operations, or on our clients’ systems.
Potential insider job? We know #LockBit #threatactor has been hiring corporate employees to gain access to their targets’ networks.#ransomware #cyber #cybersecurity #infosec #accenture pic.twitter.com/ZierqRVIjj
— Cyble (@AuCyble) August 11, 2021
LockBit claims to have stolen six terabytes of data from Accenture, adding they have gotten access to the company’s network via a corporate “insider”.
Apparently, Accenture had confirmed the attack to at least one CTI vendor, and the IT services provider is also in the process of notifying more customers. What’s more, cybercrime intelligence firm Hudson Rock revealed that Accenture had 2,500 compromised computers belonging to employees and partners.
The recent Accenture Ransomware:
Accenture has 2,500 compromised computers of employees and partners, this information was certainly used by threat actors.
Watch how a compromised employee’s computer looks like in Cavalier –https://t.co/JHI48vyDgf
— Hudson Rock (@HRock) August 11, 2021
Back in April, LockBit ransomware hit Merseyrail, one of the UK’s rail network providers. The threat actors used the Merserayl email system in order to email employees and journalists about the attack.
Earlier this week, ACSC, The Australian Cyber Security Centre issued a warning related to an increase in LockBit 2.0 ransomware attacks against Australian organizations. It’s also interesting to note that LockBit 2.0 is attempting to remove the middlemen by trying to recruit insiders in the hope they would provide the ransomware group with access to corporate networks through Remote Desktop Protocol (RDP) and Virtual Private Network (VPN).


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










