Contents:
A high-severity bug in the WordPress Email Template Designer WP HTML Mail, which is installed in more than 20,000 websites, can lead to code injection and the distribution of persuasive phishing emails.
WordPress WP HTML Mail is a plugin for creating tailored emails, contact form alerts, and other custom messages that digital platforms send to their customers.
WP HTML Mail is compatible with WooCommerce, Ninja Forms, BuddyPress, and other popular WordPress plugins. Despite the fact that the number of websites that use it is small, many of them have large audiences, causing the vulnerability to affect numerous users.
Abusing the Flaw
The vulnerability, discovered by the Wordfence Threat Intelligence team and tracked as CVE-2022-0218, could be exploited by an unauthenticated threat actor to inject malicious JavaScript into the mail template that would execute whenever a site administrator accessed the HTML mail editor.
As always, cross-site scripting vulnerabilities can be used to inject code that can add new administrative users, redirect victims to malicious sites, inject backdoors into theme and plugin files, and so much more.
In addition, this bug can lead to a complete site takeover.
The high-severity bug in the WordPress Email Template Designer WP HTML Mail could also enable an attacker to alter the email template to include arbitrary data, which could be used to launch a phishing attack against anyone who got email messages from the compromised website.
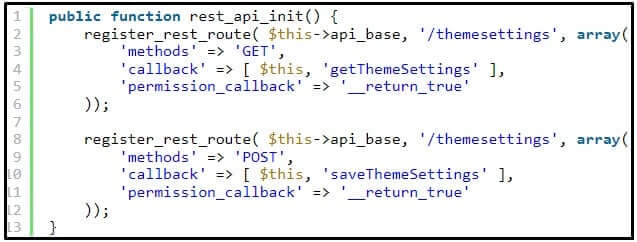
The issue is caused by the plugin’s registration of two REST-API routes used for retrieving and updating email template settings.
As explained by BleepingComputer, unauthenticated users could access these API endpoints because they were “insecurely implemented.”
The plugin registers the /themesettings endpoint, which calls the saveThemeSettings function or the getThemeSettings function depending on the request method.
The REST-API endpoint did use the permission_callback function, however, it was set to __return_true which meant that no authentication was required to execute the functions.
Therefore, any user had access to execute the REST-API endpoint to save the email’s theme settings or retrieve the email’s theme settings.
On December 23, 2021, Wordfence discovered and reported the weakness to the plugin’s developer, but they didn’t hear back until January 10, 2022. A security update to fix the vulnerability was released on January 13, 2022.
The Wordfence Threat Intelligence Team advises all WordPress administrators and owners running the email template designer plugin to update it to version 3.1 as quickly as possible.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security