Contents:
Polkit is a system service installed by default on many Linux distributions that are used by systemd, therefore any Linux distribution that uses systemd also uses polkit.
Polkit and Its Importance?
Polkit represents the system that plays the role of a decision-maker tool, as for example, it can decide whether or not you’re allowed to create a new user account.
Polkit is designed to make decisions instantly and also to let an administrator grant authorization for making a decision.
A few weeks ago GitHub Security Lab security researcher Kevin Backhouse found a privilege escalation vulnerability in polkit that enables an unprivileged local user to get a root shell on the system, therefore making it easier to exploit with just a few standard command-line tools.
The polkit local privilege escalation bug was tracked as CVE-2021-3560 after being publicly disclosed and a fix for this specifical vulnerability was released on June 3, 2021.
The bug found was quite old, as it was introduced seven years ago in the commit bfa5036 and shipped with the polkit version 0.113, but as many of the most popular Linux distributions didn’t ship the vulnerable version until more recently.
Linux users: please upgrade polkit to get the fix for CVE-2021-3560. More details in a blog post later this week. https://t.co/NCNY2s6O5g
— Kevin Backhouse (@kevin_backhouse) June 7, 2021
This bug has different history on Debian and other systems, like Ubuntu, because Debian uses a fork of polkit with a different version numbering scheme.
Therefore, it’s worth mentioning that even though many Linux distributions haven’t shipped with the vulnerable polkit version until recently, any Linux system shipping with polkit 0.113 or later installed is exposed to attacks.
The list that contains the vulnerable distros is including popular distros like RHEL 8, Fedora 21 (or later), Ubuntu 20.04, and also unstable versions like Debian testing (‘bullseye’) and its derivatives.
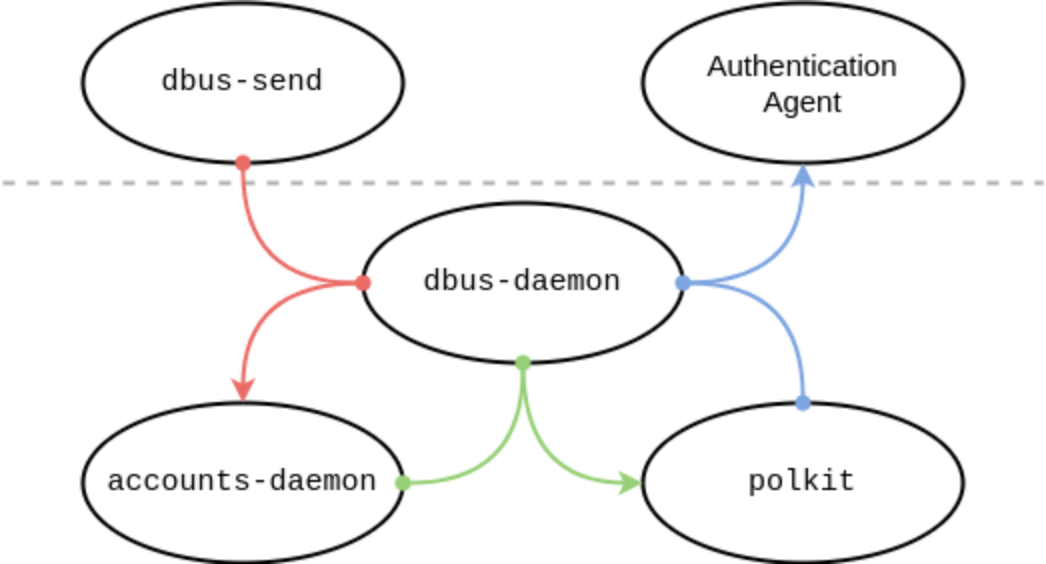
It’s really easy to exploit the vulnerability as it only takes a few terminal commands using only standard tools such as bash, kill, and dbus-send.
When a requesting process disconnects from dbus-daemon just before the call to polkit_system_bus_name_get_creds_sync starts, the process cannot get a unique uid and pid of the process and it cannot verify the privileges of the requesting process.
The highest threat from this vulnerability is to data confidentiality and integrity as well as system availability.
In other news, the researchers from GRIMM have also discovered 15-year-old vulnerabilities in the iSCSI subsystem of the Linux kernel that seems to be affecting all Linux distributions, therefore the vulnerable kernel module is not loaded by default, but the attackers can load and exploit the buggy kernel module themselves.

Heimdal® Network DNS Security
- No need to deploy it on your endpoints;
- Protects any entry point into the organization, including BYODs;
- Stops even hidden threats using AI and your network traffic log;
- Complete DNS, HTTP and HTTPs protection, HIPS and HIDS;


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










