Contents:
The Australian Federal Police (AFP) have taken into custody a 19-year-old man in Sydney for reportedly using leaked Optus customer data for extortion.

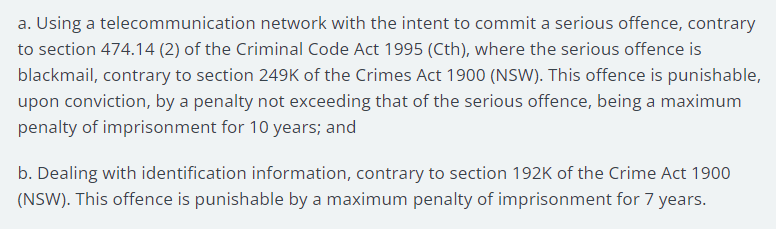
According to the official statement issued by AFP today, the suspect now faces two charges: one for blackmail and the second for dealing with identification information, which carry a maximum penalty of 10 and 7 years’ imprisonment.
How Did the Ransom Attempt Happen?
As Bleeping Computer related, the suspect used 10,200 records leaked by Optus hackers last month to contact victims via SMS and threaten to sell their data to other cybercriminals unless they paid AUD 2,000 ($1,300) within two days.
To receive the ransom money, the young man used a Commonwealth Bank of Australia account. The AFP located the account and obtained data on the account holder from the bank.
It will be alleged in court that text messages were sent to 93 Optus customers who had their data exposed on an internet forum. At this stage it appears none of the individuals who received the text message transferred money to the account.
The suspect is accused of sending 93 people blackmailing messages after an Optus data leak exposed their personal information. Luckily, none of them made the ransom payment.
The Optus Breach and Its Ongoing Investigation
Optus, the second-largest wireless carrier in Australia, was recently the target of one of the biggest cybersecurity attacks in the country’s history. The threat actors obtained information on 9.8 million former and current customers, out of Australia’s population of 26 million.
To combat the Optus Breach, the Australian police launched two operations: Operation Guardian, to protect the most vulnerable customers affected by it and Operation Hurricane to identify the criminals behind the alleged breach.
According to Bleeping Computer, the government ID numbers of 2.1 million of them were compromised, many of these people requiring new IDs to be issued right away. The Optus company has been requested by the Australian government to pay for this procedure.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








