Contents:
Researchers discovered an overlooked vulnerability in Lighttpd web server that is used in Baseboard Management Controllers (BMCs). The flaw impacts hardware vendors that use AMI MegaRAC BMCs, like Intel, Lenovo and Supermicro.
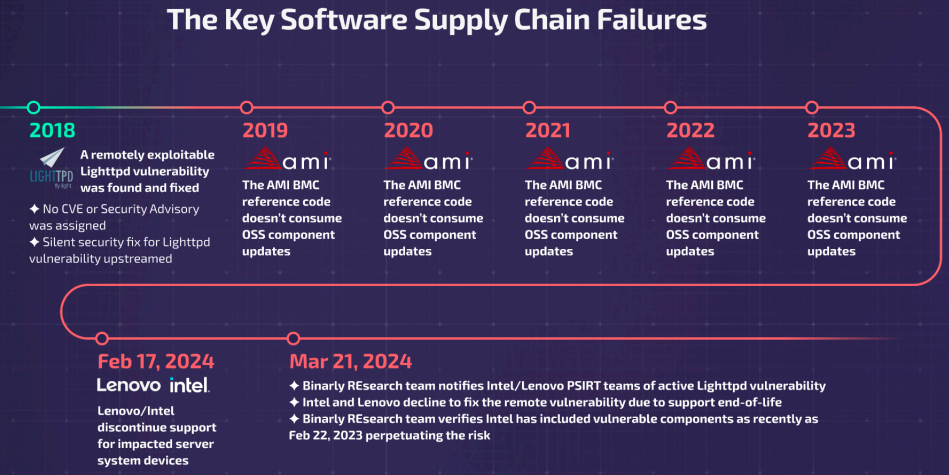
Although developers discovered and fixed the Lighttpd flaw back in 2018, the vulnerability didn’t get a CVE. Further on, Lighttpd users, like AMI and AETN BMCs producers, overlooked it and failed applying the patch.
The security researchers who found the flaw said that:
A very important part of this story is the silent fix that was pushed by lighttpd developers without details in an advisory or without a CVE identifier to help defenders with patch management processes.
Source – Binarly’s report
Unfixed vulnerability in AMI and AETN BMCs puts security at risk
BMCs are small computers used in server motherboards. They facilitate remote management of server fleets for cloud centers and users, including OS reinstallation and app control, even when offline.
Hackers can exploit the lighttpd vulnerability remotely to exfiltrate process memory addresses. Correlating it with other vulnerabilities would lead to evading standard protection measures.
The flaw affects all hardware using lighttpd versions 1.4.35, 1.4.45, and 1.4.51.
Source – BleepingComputer
Researchers first found the vulnerability in one of Intel’s Server System devices lighttpd module. The same team confirmed later finding the same flaw in Lenovo products. Binarly notified both Intel and Lenovo.
The hardware producers say the impacted products are already end-of-life, so are not supporting them anymore. Therefore, the lighttpd vulnerability will remain unfixed.
The researchers pointed out that the security issue remained unpatched for several years, although a patch was available. For a while, producers even released new firmware impacted by the flaw.
All these years, it was present inside the firmware and nobody cared to update one of the third-party components used to build this firmware image. This is another perfect example of inconsistencies in the firmware supply chain. A very outdated third-party component present in the latest version of firmware, creating additional risk for end users.
Source – Binarly’s report
At the moment, more than 2000 impacted devices are still active and exploitable.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and Youtube, for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security