Contents:
Researched and written by Heimdal founder Morten Kjaersgaard, this article exposes how even limited cooperation between registry bodies and law enforcement could cripple ransomware networks and raise the cost for cybercriminals.
This article serves as a wake-up call.
Even limited cooperation between registry bodies and law enforcement could cripple ransomware networks and raise the cost for cybercriminals.
Ransomware payments hit $813 million in 2024 and my expectation is that they will re-surpass $1 billion in 2025, as they did in 2023.
But where is all that money flowing?
Heimdal has conducted an in-depth analysis of internal attack telemetry, tracing attack sources back to ownership and affiliate entities.
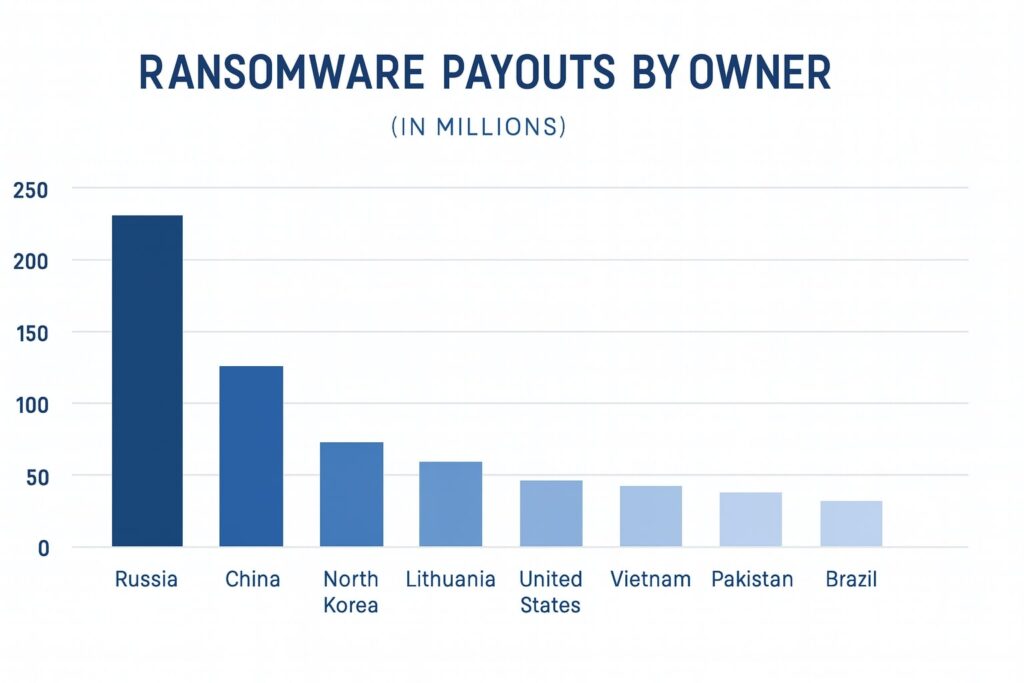
Based on this analysis, if $1 billion were distributed proportionally across observed patterns, the resulting payouts by country would include a staggering $211 million flowing to Russia.
Russia, China, and North Korea combined account for roughly 38 percent of all ransomware payouts, equating to approximately $383 million.
How obfuscation enables attacks
Russia is known to leverage shell companies based in Germany, such as Razi Network, which is listed at a German address but does not appear in the national company register.
China utilizes entities in France while Hong Kong leverages one named Think Tech.
The degree of obfuscation becomes especially clear when looking at the origin of attacks.
Heimdal observed significant activity from North Korea’s APT38 group, which appears to be launching financially motivated attacks from Panama, using IP ranges like 45.227.254.151 to 45.227.254.156.
For such a small country, Panama hosts an unusually high number of attacks.
A heatmap of attack origins underscores the concentration in Russia, China, and North Korea.
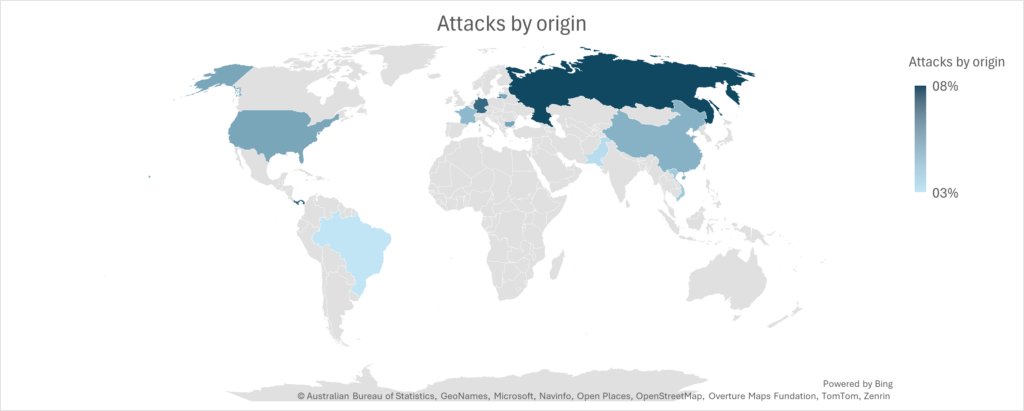
The scale and organization behind these campaigns as alarming.
While it’s not a huge surprise to see Russia, China, and North Korea as major operators behind targeted ransomware attacks, the sophistication and automation with which these attacks are executed is staggering.
By spinning up fake or non-existent companies, these actors circumvent Western controls. Organizations like RIPE and ARIN are meant to manage IP allocations in Europe and the US.
Or let me rephrase: they should manage IPs. The current level of control is clearly extremely poor.
Infrastructure loopholes make it easy
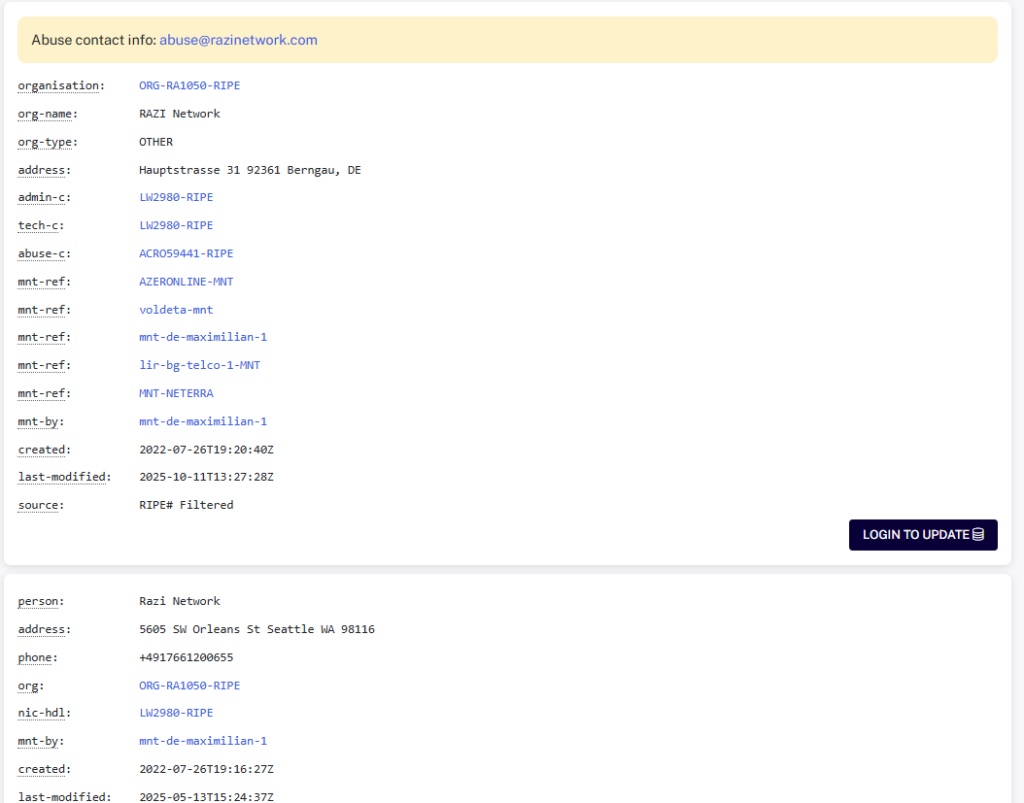
Heimdal has found evidence in the RIPE database of companies that do not appear in official business registries still owning IP addresses via European-based records.
For example, Razi Network claims an address in Bergnau, Germany, but no such company is found in German commercial databases.
Such discrepancies reveal systemic weaknesses in Know Your Customer (KYC) enforcement by registrars and create frictionless paths for threat actors to scale operations.
Call for action
I believe the situation could be reversed with decisive action from governments and registry bodies.
This isn’t an unsolvable problem. German and French law enforcement have jurisdiction. RIPE and the UK’s Companies House have the tools.
All that’s missing is the will to connect the dots.
We urge law enforcement and corporate registry authorities to tighten enforcement and verification. These bodies are well-positioned to dismantle fraudulent networks and significantly raise the cost of doing business for cybercriminals.
This article is intended as a wake-up call.
With even modest cooperation across jurisdictions, many of these ransomware networks could be exposed and disrupted before they cause further global economic harm.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








