Contents:
Ticketmaster has been breached and the data of over 500 million customers is listed for sale. A threat actor known as ShinyHunters is selling on the recently revived BreachForums hacking forum what they claim is the personal and financial information of Ticketmaster customers. The listing goes for $500,000.
Details About the Breach: What Information Was Stolen?
The allegedly stolen databases initially offered for sale on the Russian hacker site Exploit, are purported to hold 1.3 terabytes of information, including complete client details (including names, home and email addresses, and phone numbers), ticket sales, purchase, and event details.
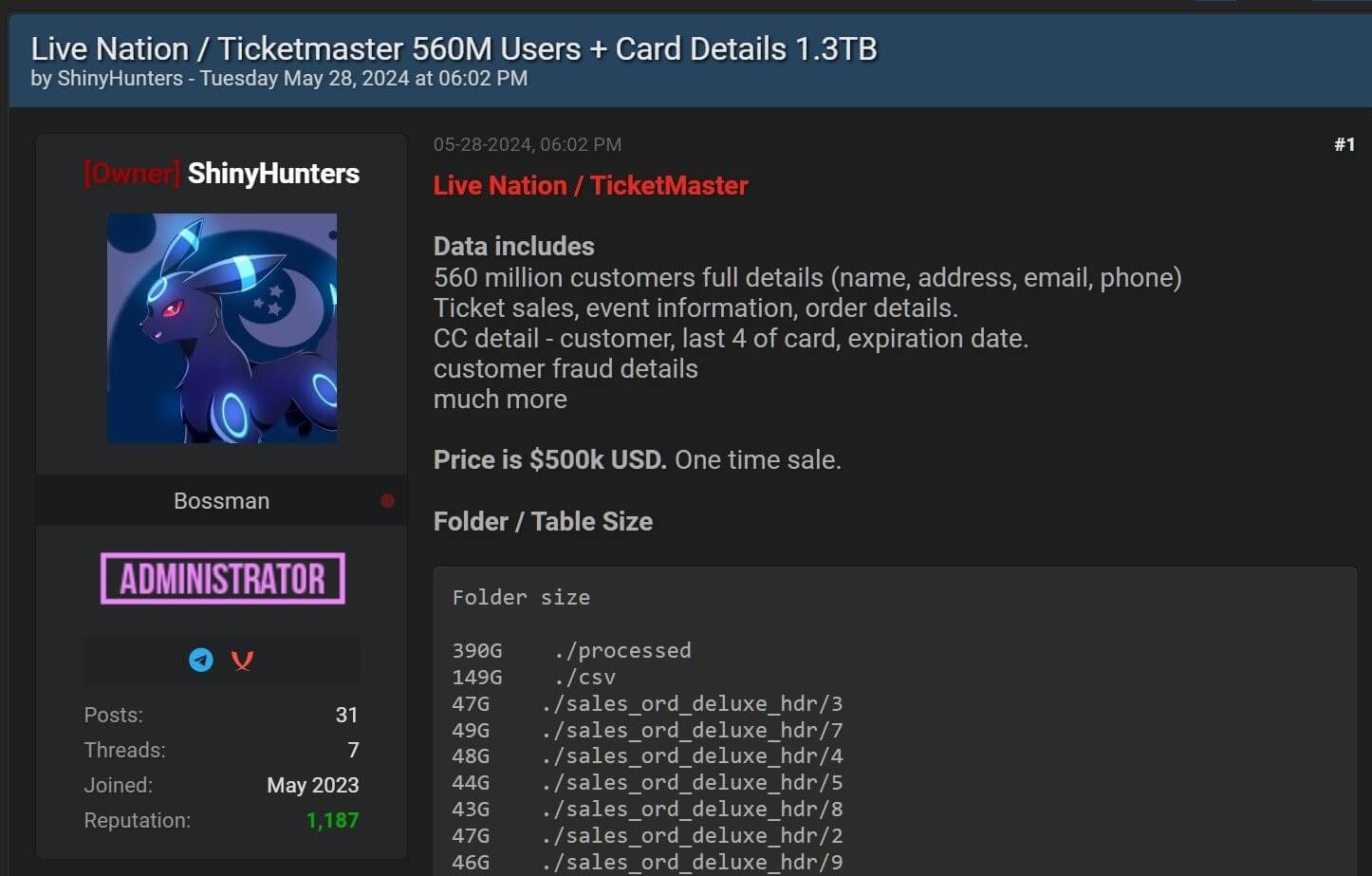
BreachForums Post With the Sale of the Ticketmaster Data (Source)
Along with financial transactions from 2012 to 2024, they also include consumer credit card information, such as hashed credit card numbers, the last four digits of the card numbers, credit card and authentication types, and expiration dates.
As per BleepingComputer, the data seller told them that some buyers are interested in the data and suspect one might be Ticketmaster themselves. The threat actors did not reveal when and how the data was stolen.
Despite this, according to BleepingComputer, the cybersecurity collective vx-underground claimed to have spoken to some threat actors who allegedly breached Ticketmaster, who said that the data could have been stolen from the company’s AWS instances by pivoting from an MSP.
Ticketmaster has yet to offer any information on the breach, or to confirm the claims of the threat actor.
If you liked this piece, follow us on LinkedIn, Twitter, Facebook, and YouTube for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








